- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- <iframe src="https://www.slidestalk.com/u181/distributed_systems_and_algorithms04?embed" frame border="0" width="640" height="360" scrolling="no" allowfullscreen="true">复制
- 微信扫一扫分享
分布式系统和算法:互斥
展开查看详情
1 .Distributed Mutual Exclusion
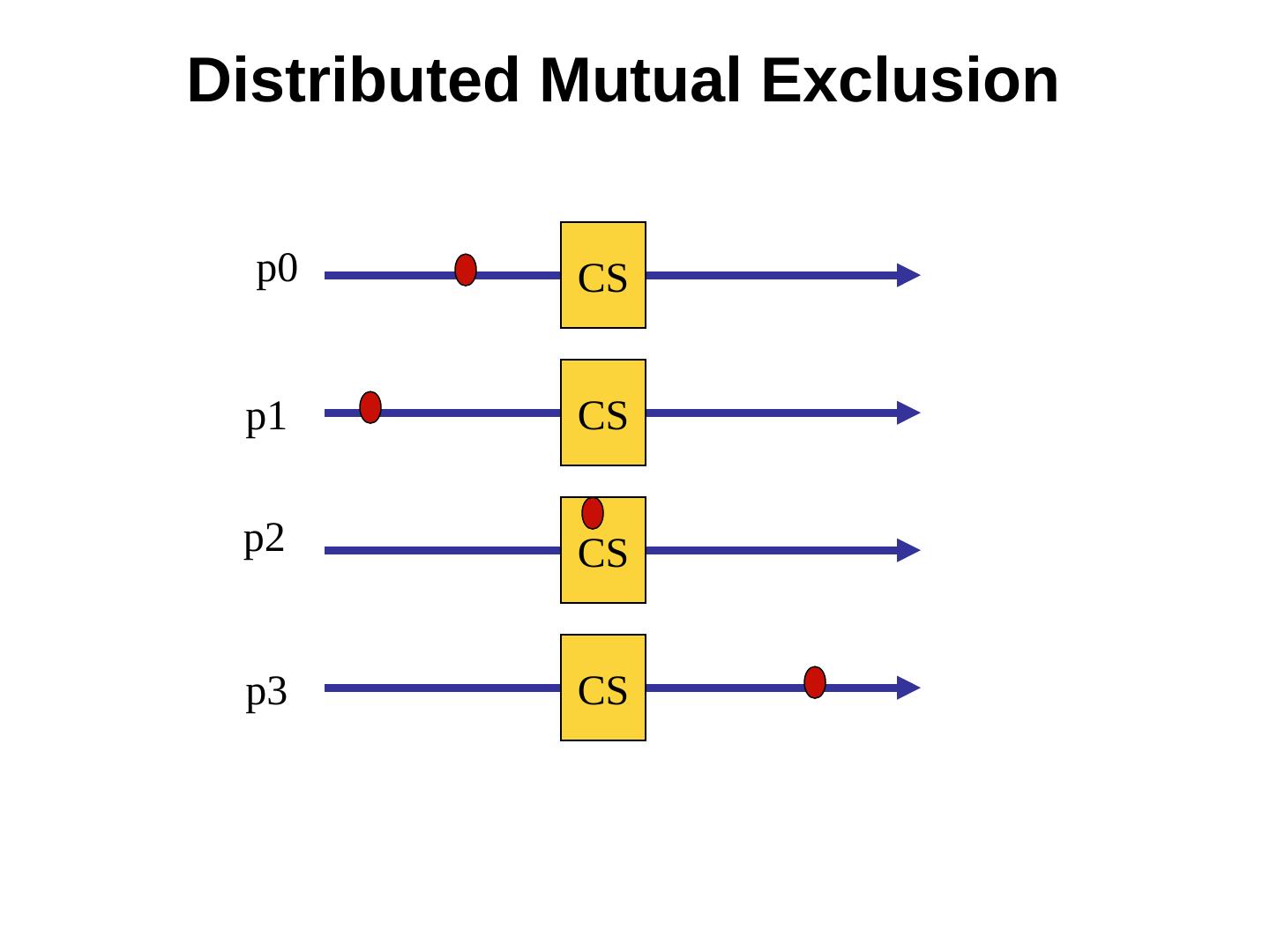
2 .Distributed Mutual Exclusion p0 CS p1 CS p2 CS p3 CS
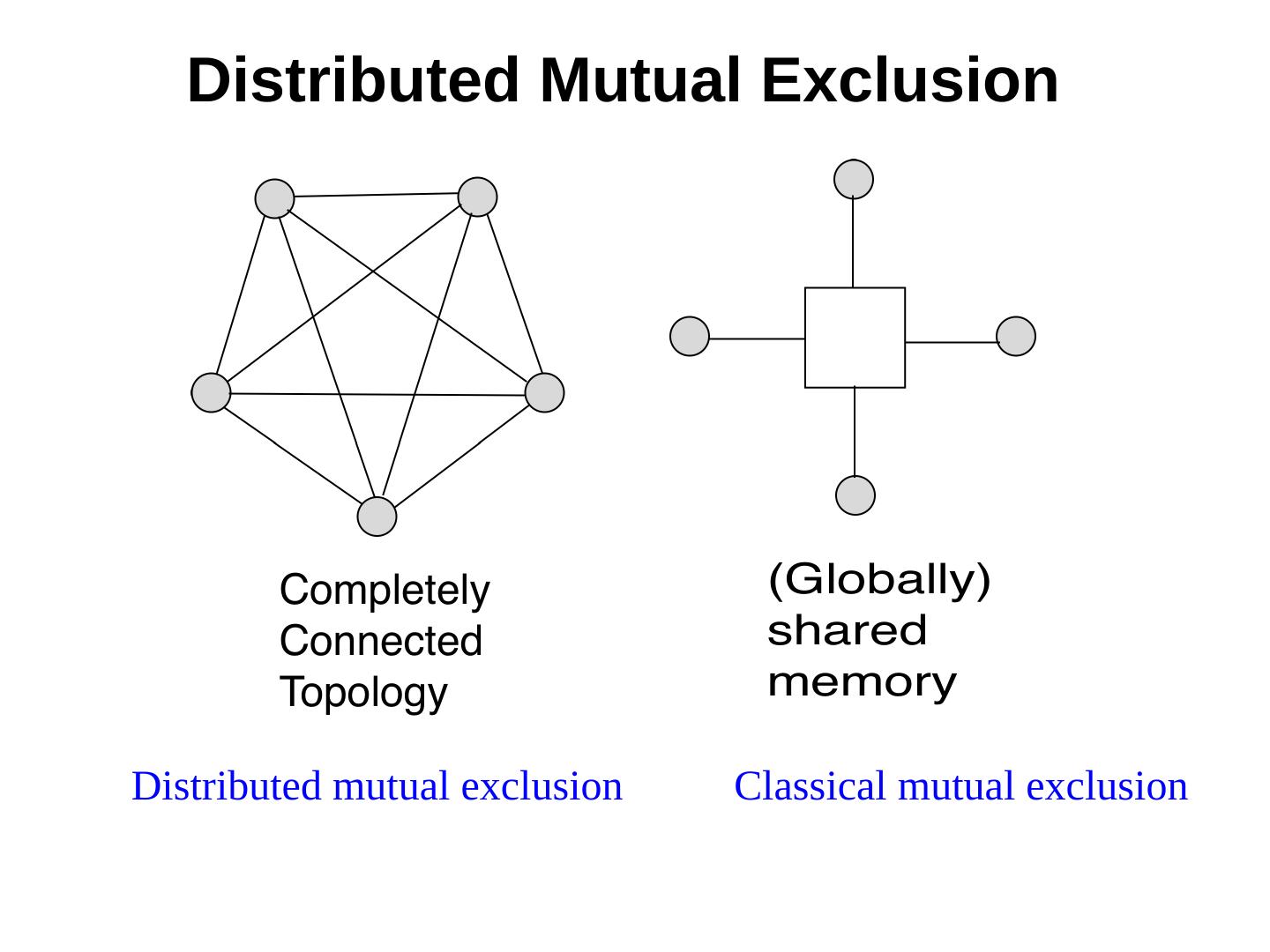
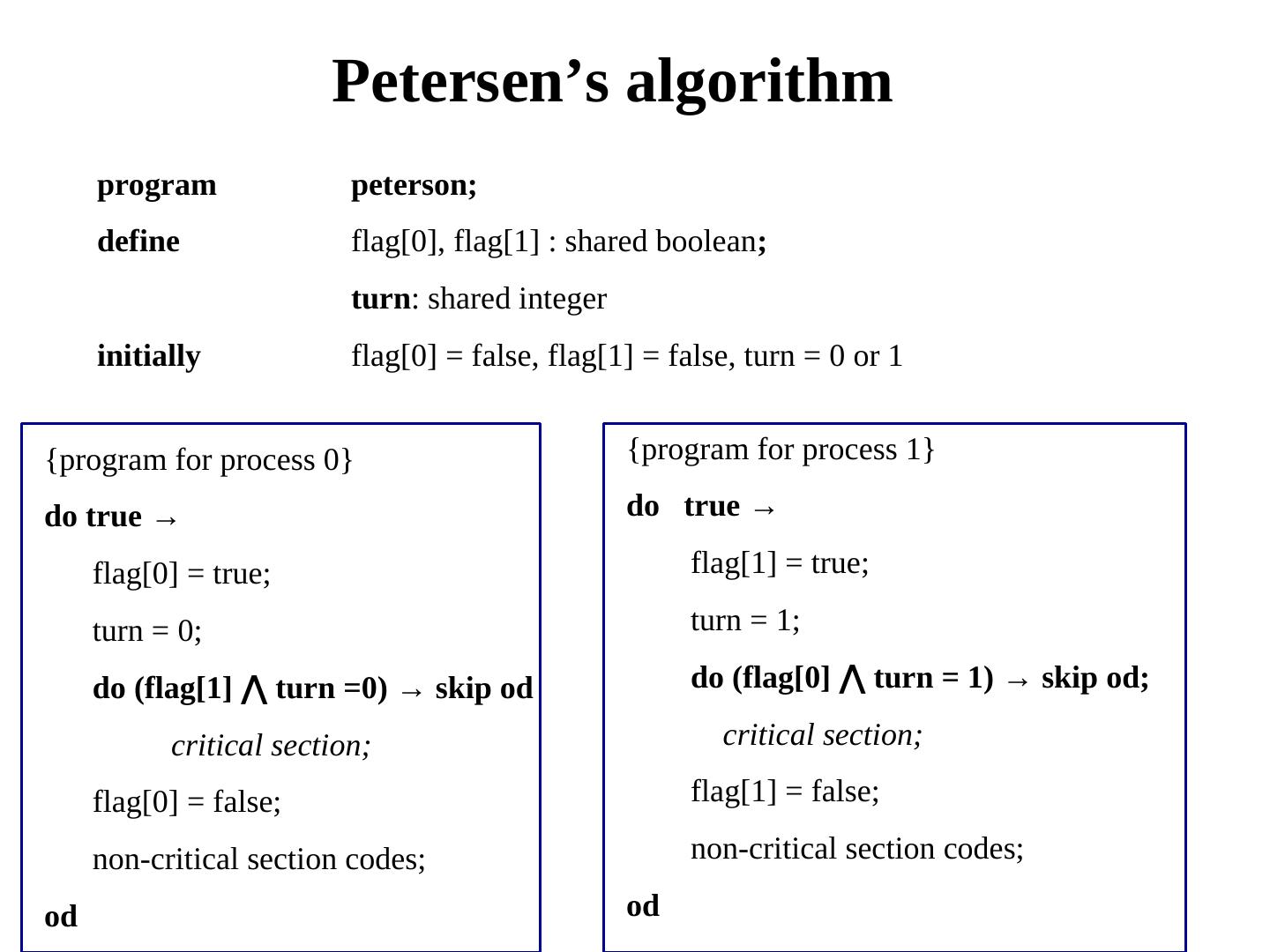
3 . Distributed Mutual Exclusion Distributed mutual exclusion Classical mutual exclusion
4 . Why mutual exclusion? Some applications are: 1. Resource sharing 2. Avoiding concurrent update on shared data 3. Implementing atomic operations 4. Medium Access Control in Ethernet 5. Collision avoidance in wireless broadcasts
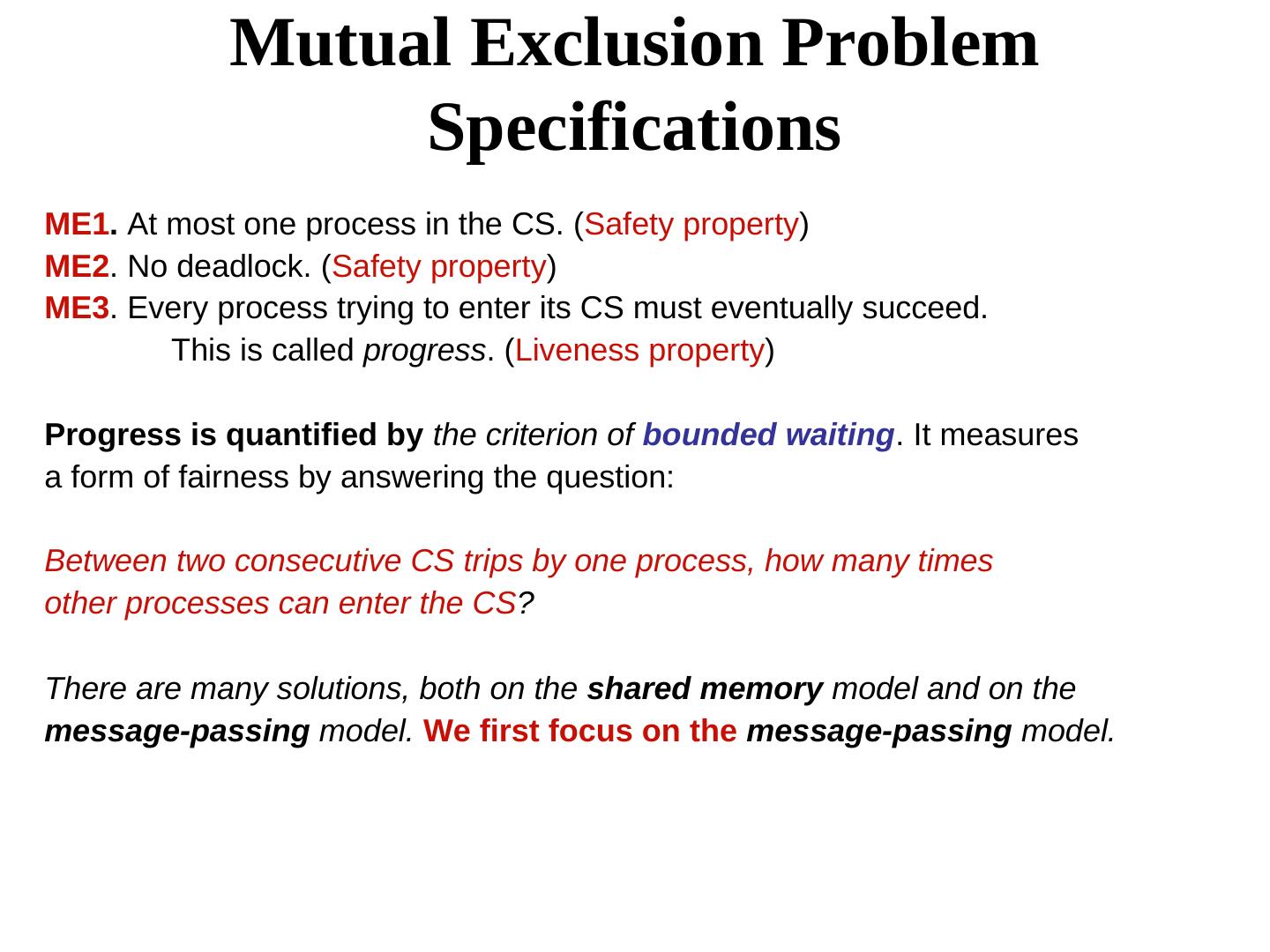
5 . Mutual Exclusion Problem Specifications ME1. At most one process in the CS. (Safety property) ME2. No deadlock. (Safety property) ME3. Every process trying to enter its CS must eventually succeed. This is called progress. (Liveness property) Progress is quantified by the criterion of bounded waiting. It measures a form of fairness by answering the question: Between two consecutive CS trips by one process, how many times other processes can enter the CS? There are many solutions, both on the shared memory model and on the message-passing model. We first focus on the message-passing model.
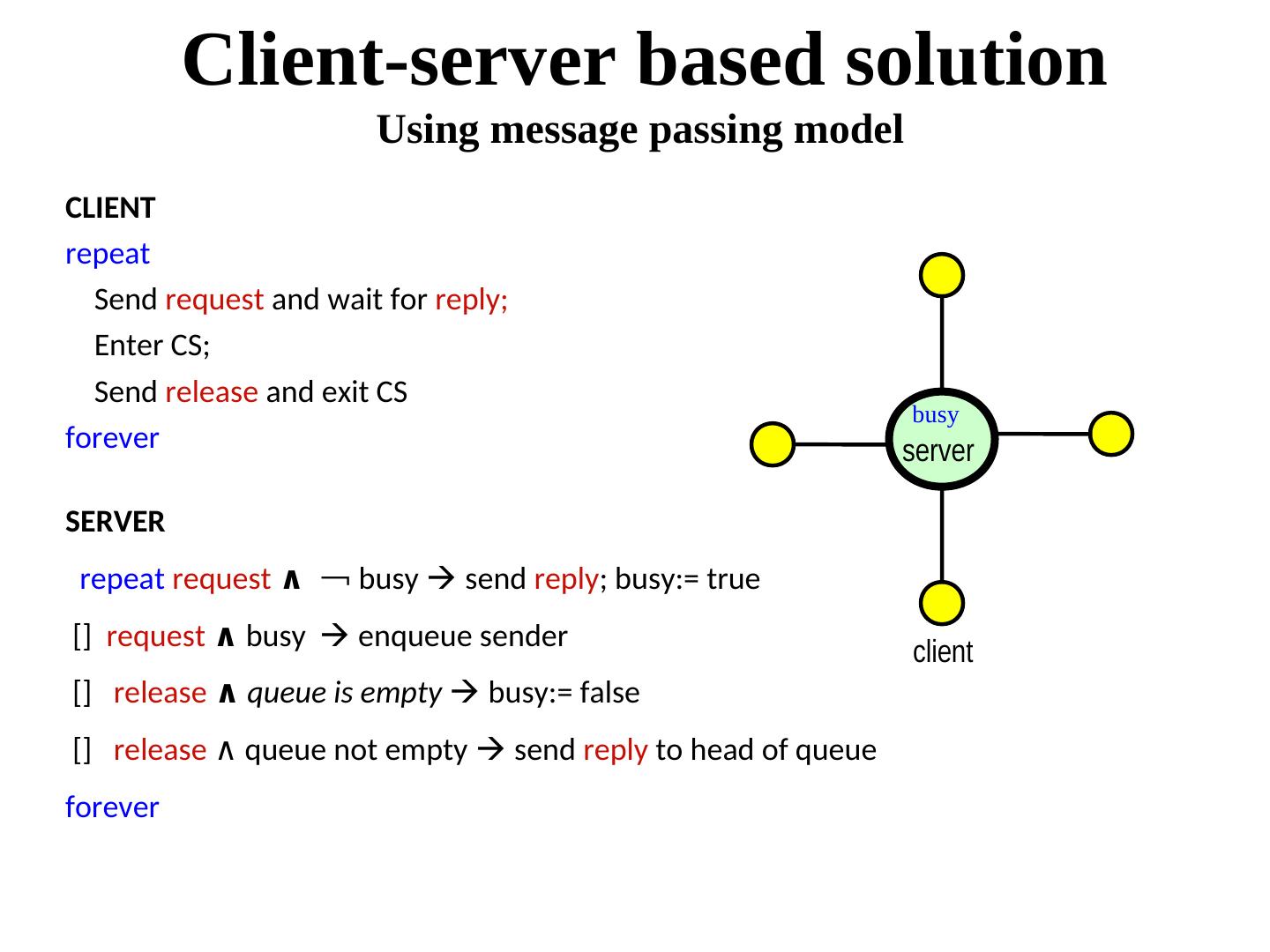
6 . Client-server based solution Using message passing model CLIENT repeat Send request and wait for reply; Enter CS; Send release and exit CS busy forever server SERVER repeat request ∧ ¬ busy send reply; busy:= true [] request ∧ busy enqueue sender client [] release ∧ queue is empty busy:= false [] release ∧ queue not empty queue not empty send reply to head of queue forever
7 . Comments - Centralized solution is simple. - But the central server is a single point of failure. This is BAD. - ME1-ME3 is satisfied, but FIFO fairness is not guaranteed. Why? Can we do without a central server? Yes!
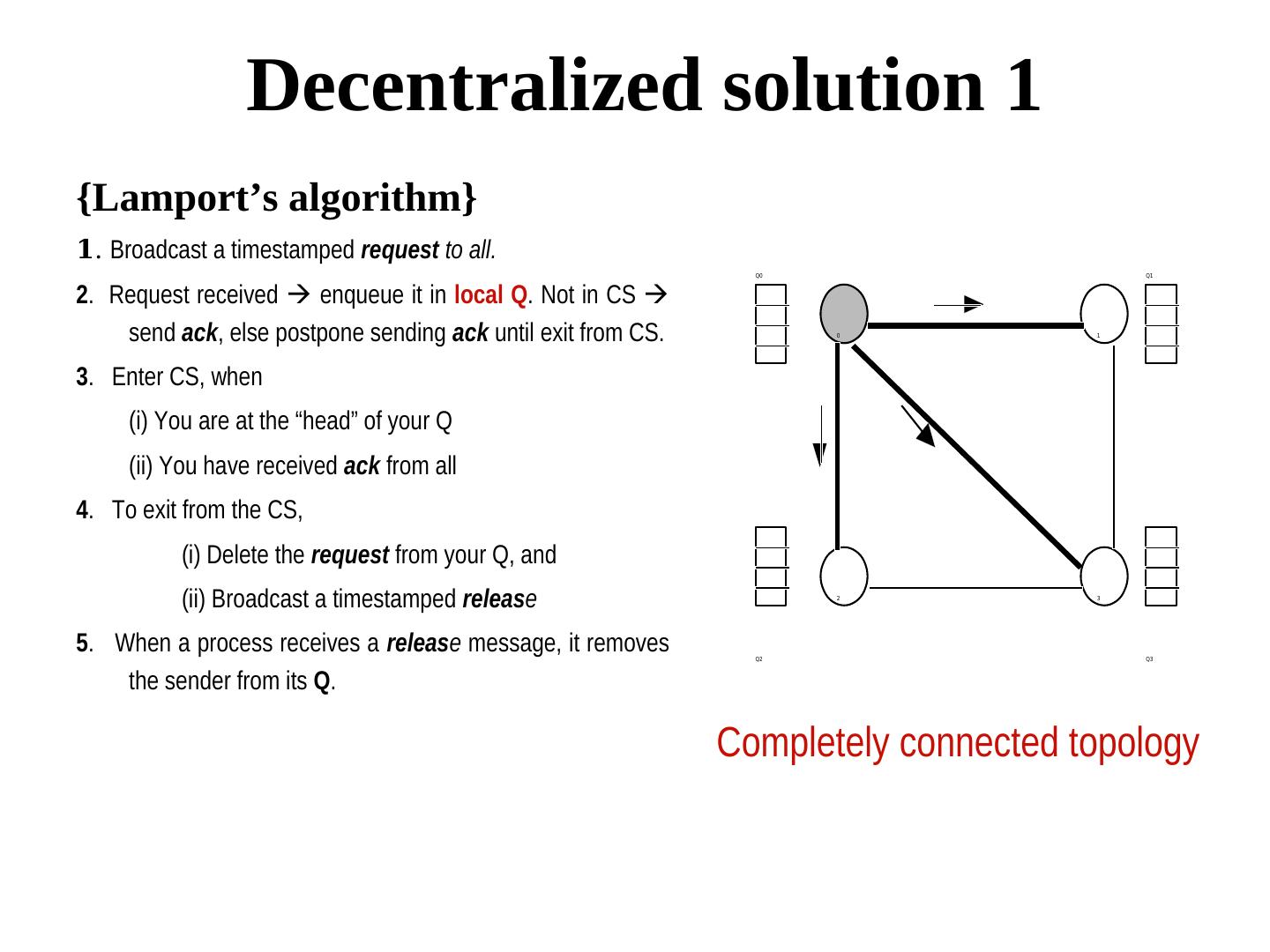
8 . Decentralized solution 1 {Lamport’s algorithm} 1. Broadcast a timestamped request to all. Q0 Q1 2. Request received enqueue it in local Q. Not in CS send ack, else postpone sending ack until exit from CS. 0 1 3. Enter CS, when (i) You are at the “head” of your Q (ii) You have received ack from all 4. To exit from the CS, (i) Delete the request from your Q, and (ii) Broadcast a timestamped release 2 3 5. When a process receives a release message, it removes Q2 Q3 the sender from its Q. Completely connected topology
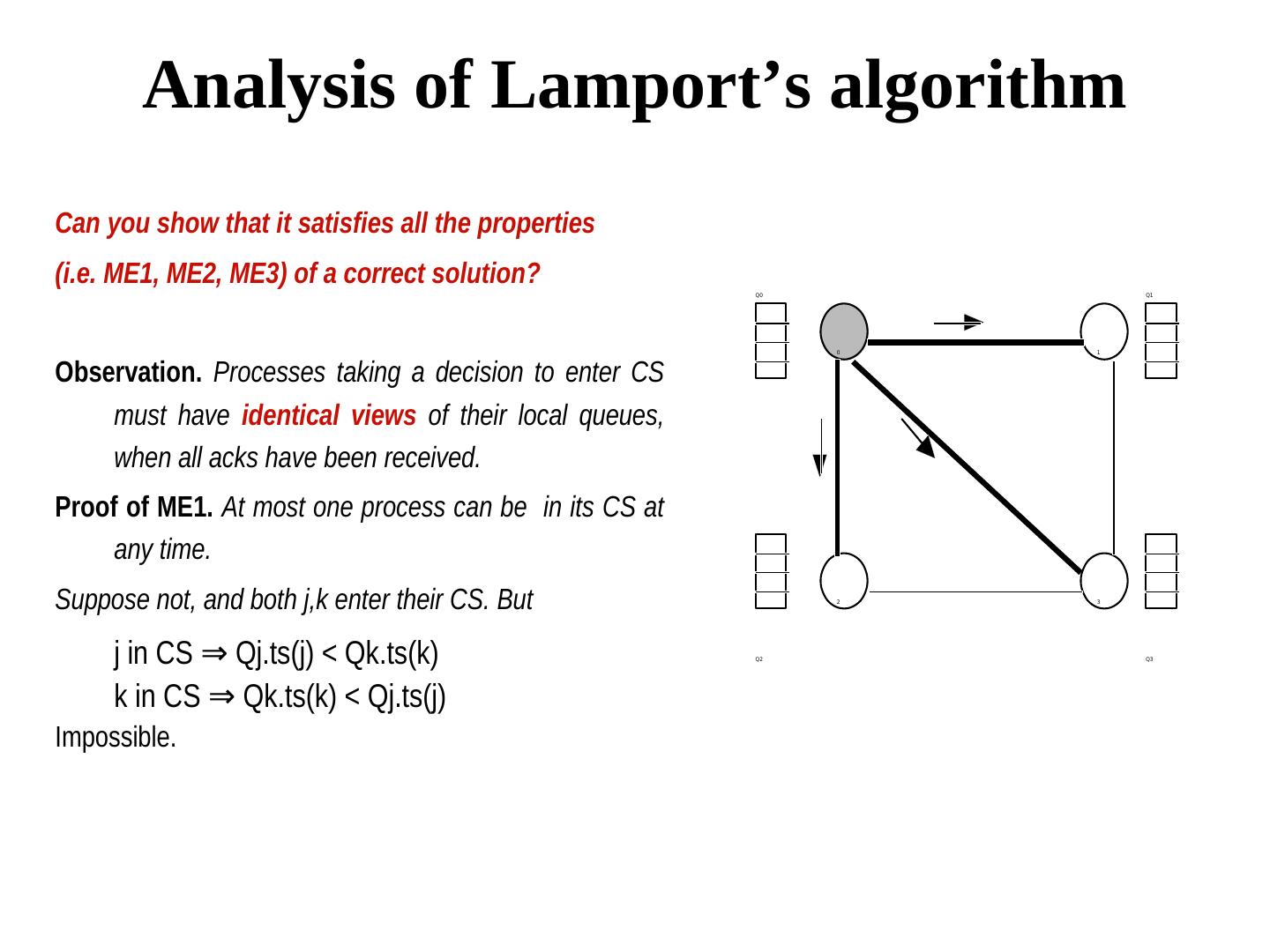
9 . Analysis of Lamport’s algorithm Can you show that it satisfies all the properties (i.e. ME1, ME2, ME3) of a correct solution? Q0 Q1 0 1 Observation. Processes taking a decision to enter CS must have identical views of their local queues, when all acks have been received. Proof of ME1. At most one process can be in its CS at any time. Suppose not, and both j,k enter their CS. But 2 3 j in CS ⇒ Qj.ts(j) < Qk.ts(k) Qj.ts(j) < Qk.ts(k) Q2 Q3 k in CS ⇒ Qj.ts(j) < Qk.ts(k) Qk.ts(k) < Qj.ts(j) Impossible.
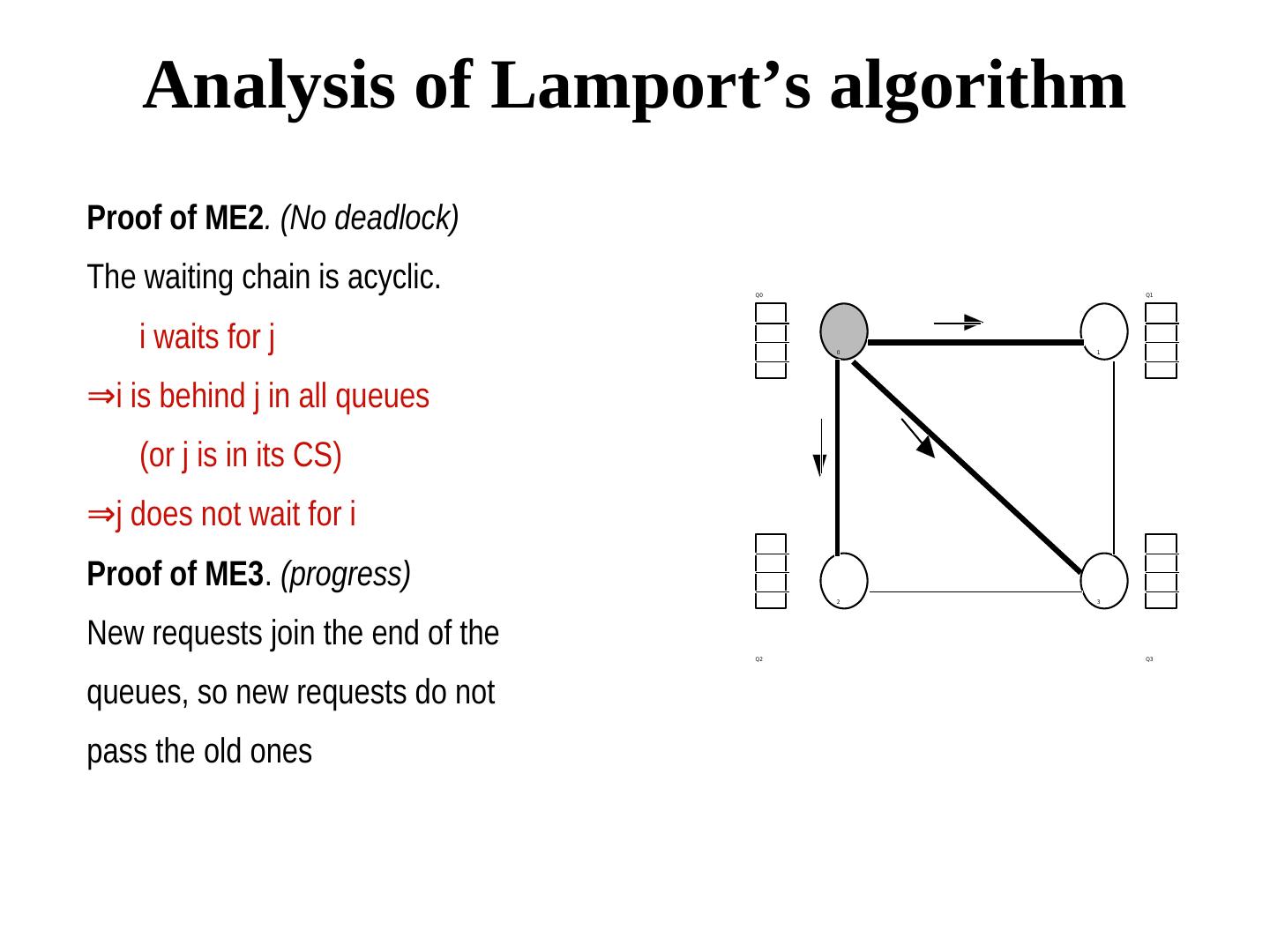
10 . Analysis of Lamport’s algorithm Proof of ME2. (No deadlock) The waiting chain is acyclic. Q0 Q1 i waits for j 0 1 ⇒ Qj.ts(j) < Qk.ts(k) i is behind j in all queues (or j is in its CS) ⇒ Qj.ts(j) < Qk.ts(k) j does not wait for i Proof of ME3. (progress) 2 3 New requests join the end of the Q2 Q3 queues, so new requests do not pass the old ones
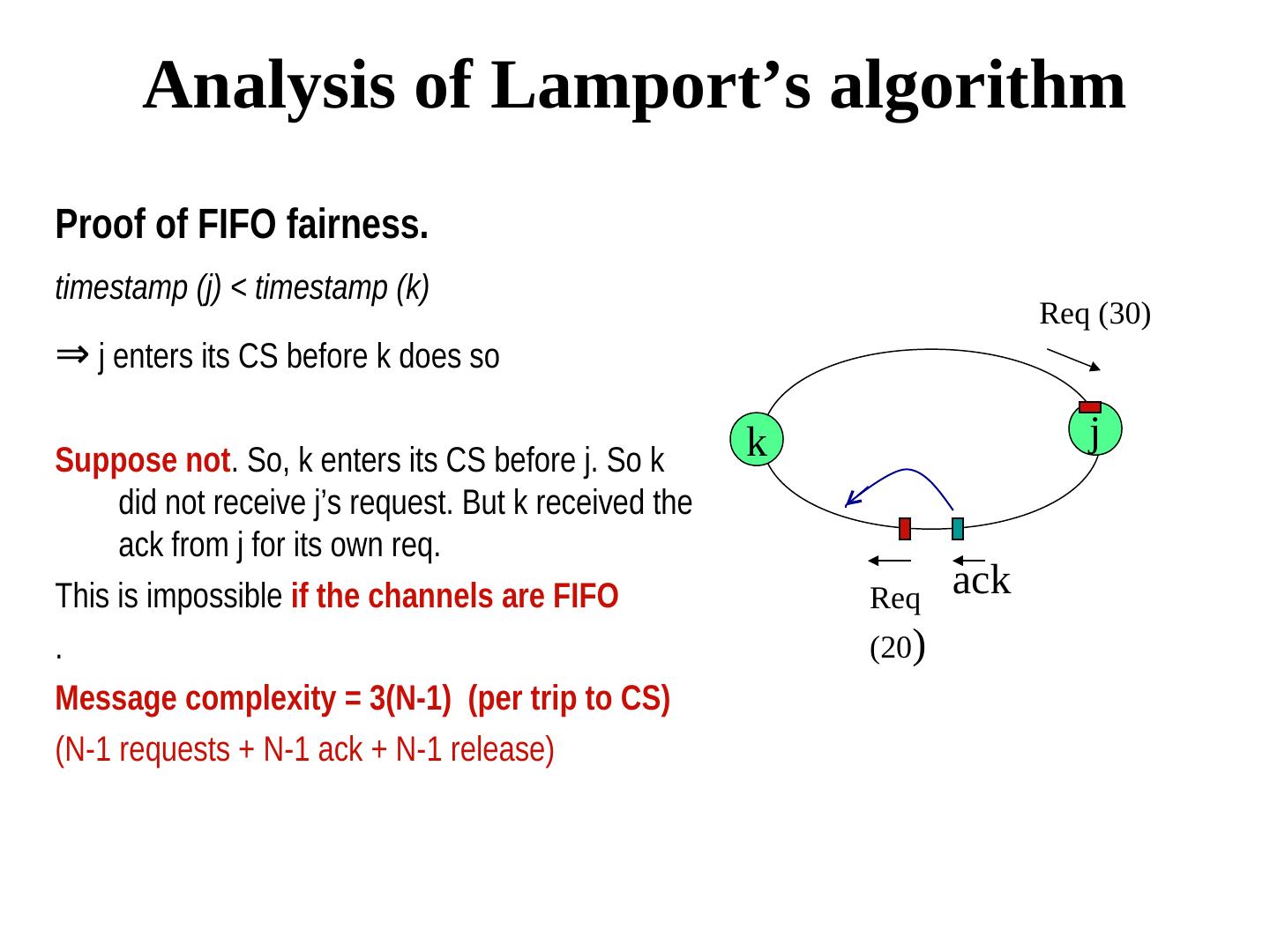
11 . Analysis of Lamport’s algorithm Proof of FIFO fairness. timestamp (j) < timestamp (k) Req (30) ⇒ Qj.ts(j) < Qk.ts(k) j enters its CS before k does so k j Suppose not. So, k enters its CS before j. So k did not receive j’s request. But k received the ack from j for its own req. This is impossible if the channels are FIFO Req ack . (20) Message complexity = 3(N-1) (per trip to CS) (N-1 requests + N-1 ack + N-1 release)
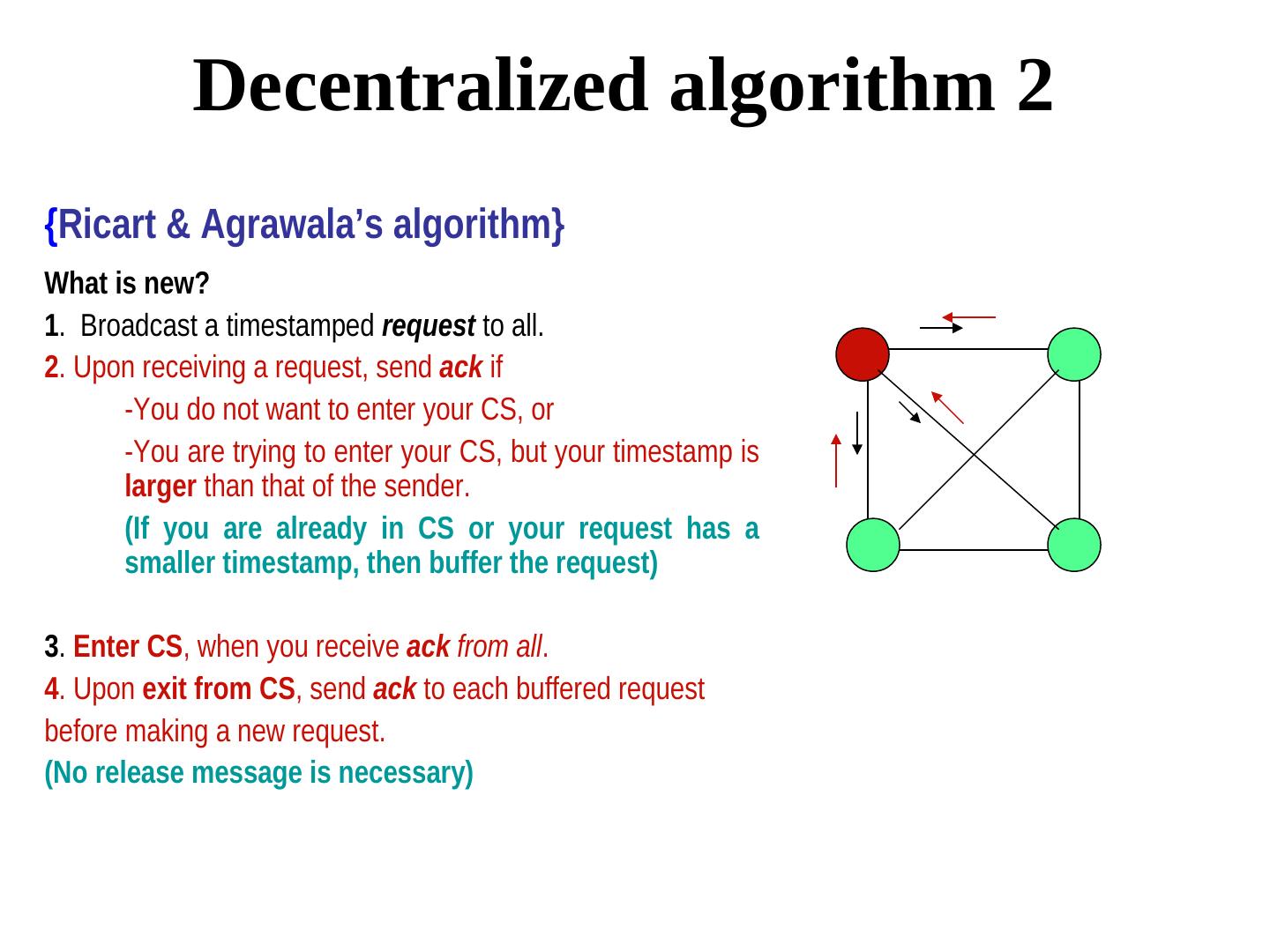
12 . Decentralized algorithm 2 {Ricart & Agrawala’s algorithm} What is new? 1. Broadcast a timestamped request to all. 2. Upon receiving a request, send ack if -You do not want to enter your CS, or -You are trying to enter your CS, but your timestamp is larger than that of the sender. (If you are already in CS or your request has a smaller timestamp, then buffer the request) 3. Enter CS, when you receive ack from all. 4. Upon exit from CS, send ack to each buffered request before making a new request. (No release message is necessary)
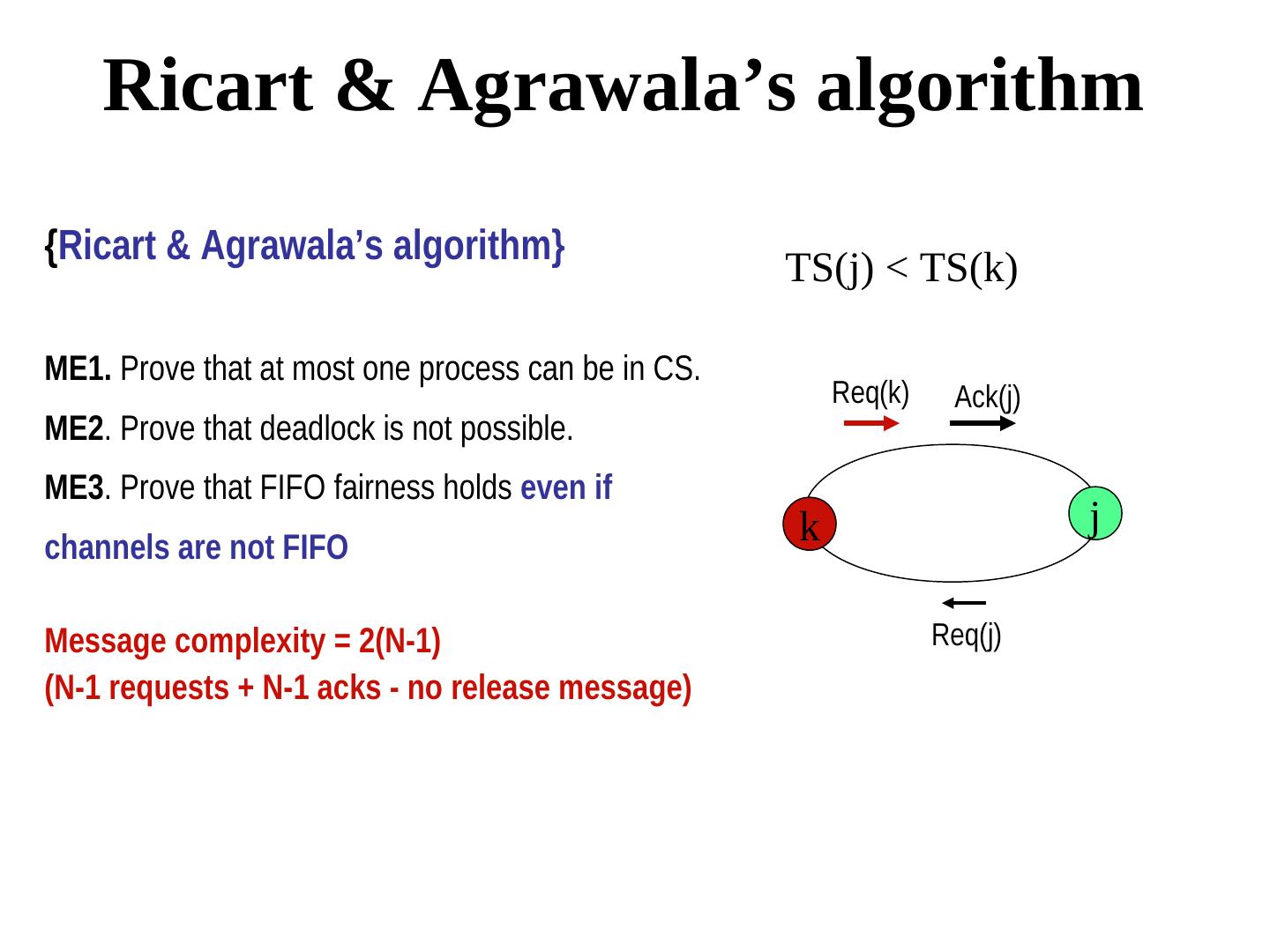
13 . Ricart & Agrawala’s algorithm {Ricart & Agrawala’s algorithm} TS(j) < TS(k) ME1. Prove that at most one process can be in CS. Req(k) Ack(j) ME2. Prove that deadlock is not possible. ME3. Prove that FIFO fairness holds even if k j channels are not FIFO Message complexity = 2(N-1) Req(j) (N-1 requests + N-1 acks - no release message)
14 . Unbounded timestamps Timestamps grow in an unbounded manner. This makes real implementations impossible. Can we somehow bounded timestamps? Think about it.
15 . Decentralized algorithm 3 {Maekawa’s algorithm} - First solution with a sublinear O(sqrt N) message complexity. - “Close to” Ricart-Agrawala’s solution, but each process is required to obtain permission from only a subset of peers
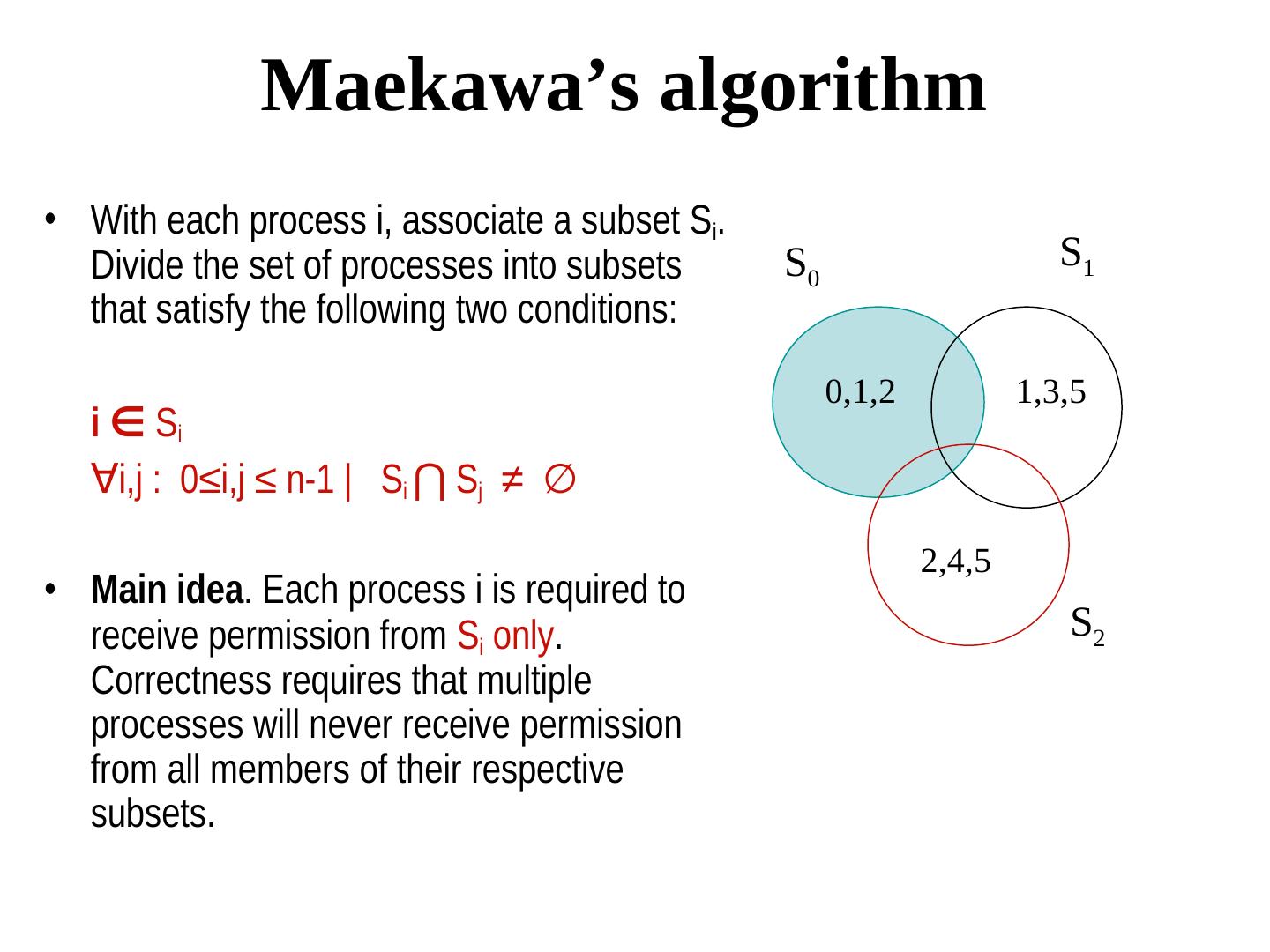
16 . Maekawa’s algorithm • With each process i, associate a subset Si. Divide the set of processes into subsets S0 S1 that satisfy the following two conditions: 0,1,2 1,3,5 i ∈ Si ∀i,j : 0≤i,j ≤ n-1 | Si ⋂ S Sj ≠ ∅ 2,4,5 • Main idea. Each process i is required to receive permission from Si only. S2 Correctness requires that multiple processes will never receive permission from all members of their respective subsets.
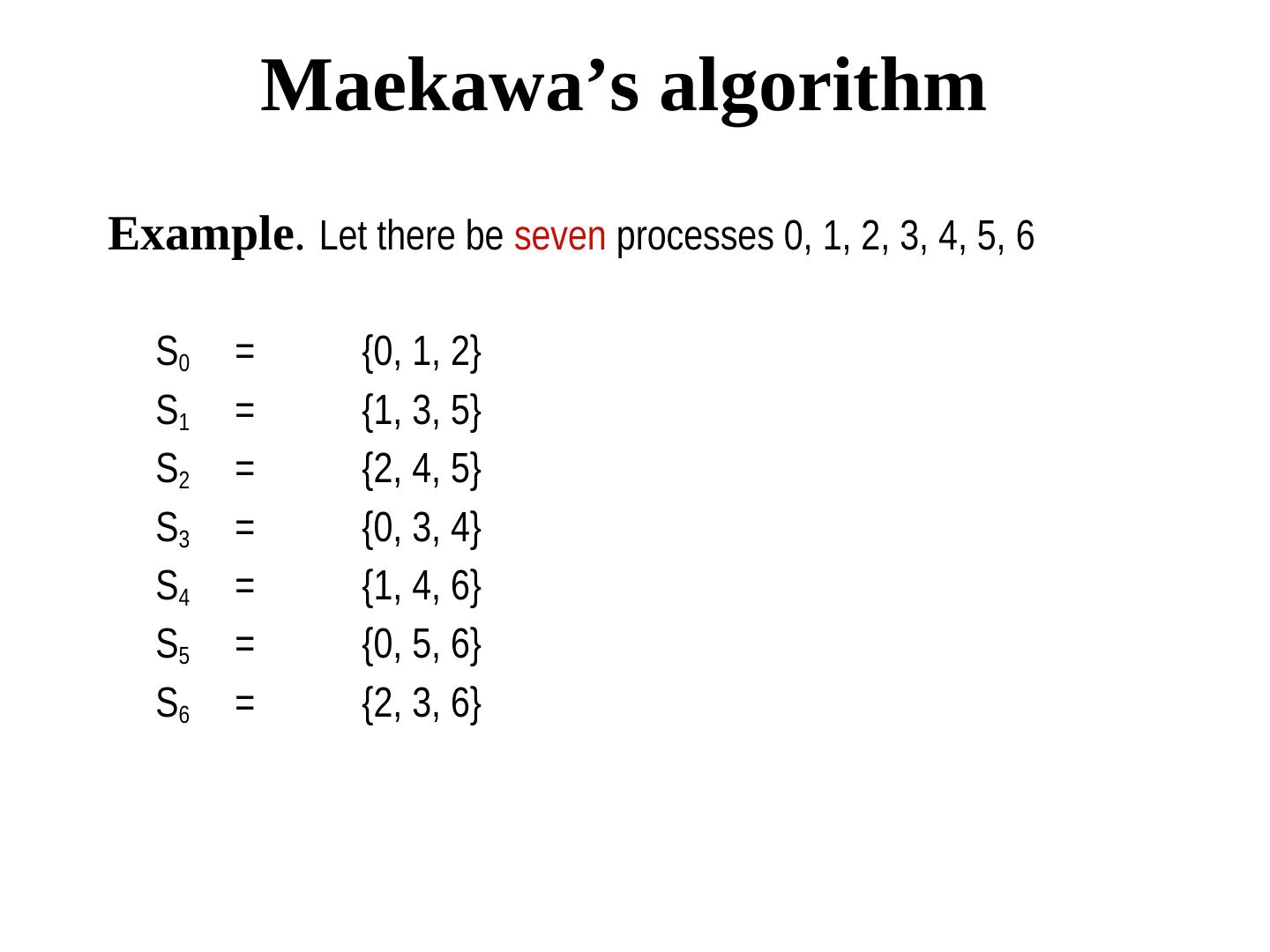
17 . Maekawa’s algorithm Example. Let there be seven processes 0, 1, 2, 3, 4, 5, 6 S0 = {0, 1, 2} S1 = {1, 3, 5} S2 = {2, 4, 5} S3 = {0, 3, 4} S4 = {1, 4, 6} S5 = {0, 5, 6} S6 = {2, 3, 6}
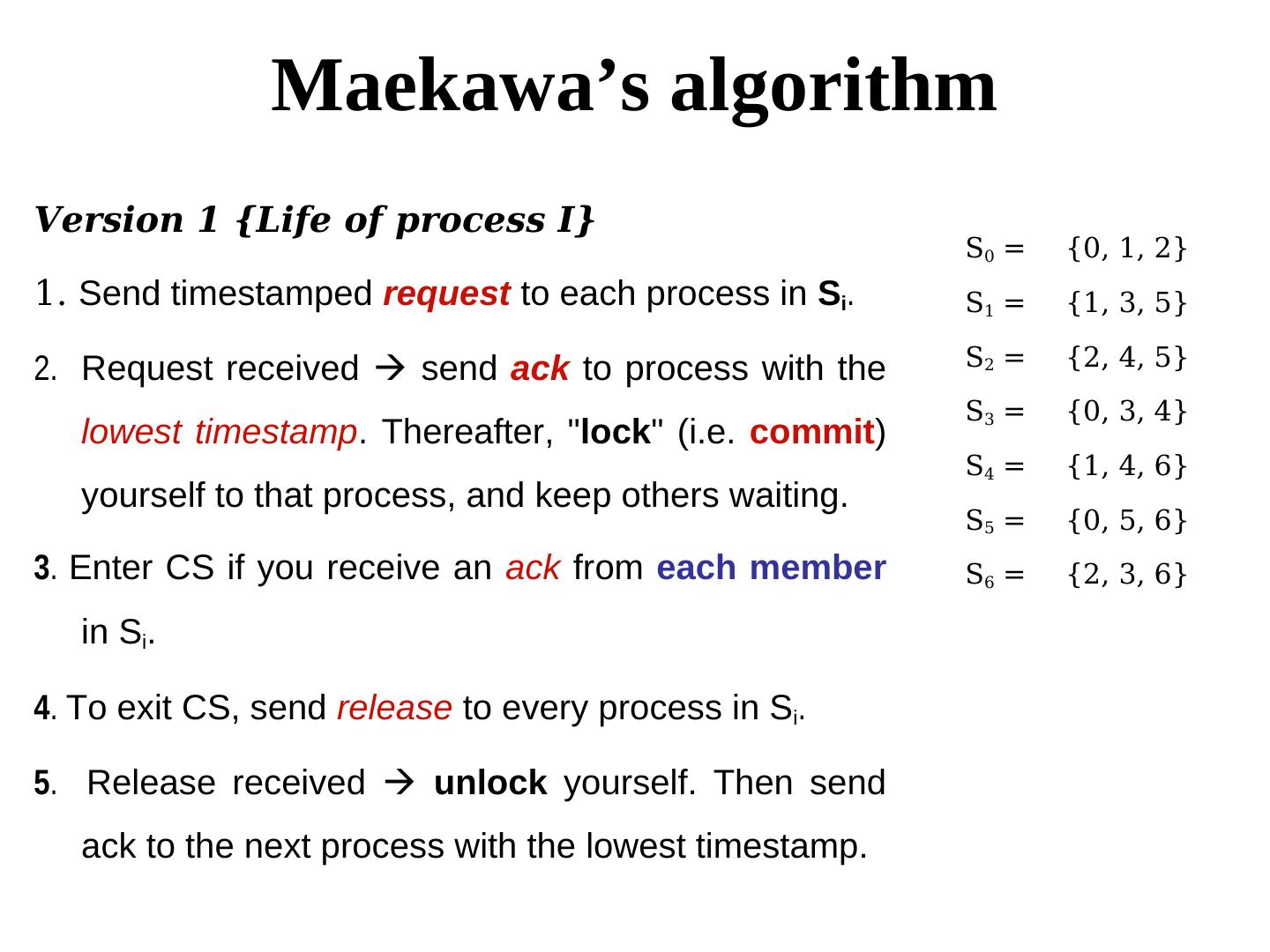
18 . Maekawa’s algorithm Version 1 {Life of process I} S0 = {0, 1, 2} 1. Send timestamped request to each process in Si. S1 = {1, 3, 5} 2. Request received send ack to process with the S2 = {2, 4, 5} S3 = {0, 3, 4} lowest timestamp. Thereafter, "lock" (i.e. commit) S4 = {1, 4, 6} yourself to that process, and keep others waiting. S5 = {0, 5, 6} 3. Enter CS if you receive an ack from each member S6 = {2, 3, 6} in Si. 4. To exit CS, send release to every process in Si. 5. Release received unlock yourself. Then send ack to the next process with the lowest timestamp.
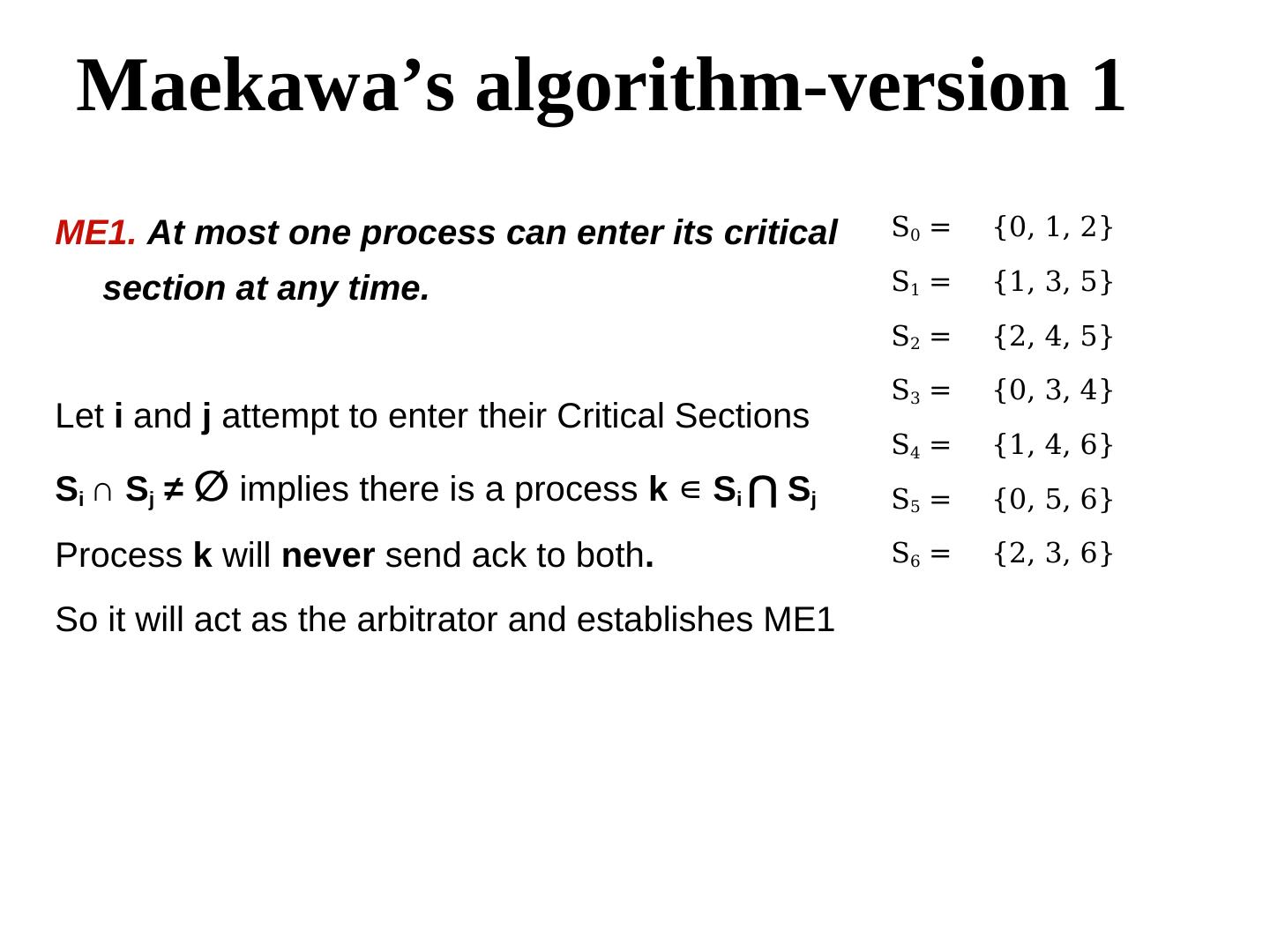
19 . Maekawa’s algorithm-version 1 ME1. At most one process can enter its critical S0 = {0, 1, 2} section at any time. S1 = {1, 3, 5} S2 = {2, 4, 5} S3 = {0, 3, 4} Let i and j attempt to enter their Critical Sections S4 = {1, 4, 6} Si ∩ Sj ≠ ∅ implies there is a process k ∊ Si ⋂ S Sj S5 = {0, 5, 6} Process k will never send ack to both. S6 = {2, 3, 6} So it will act as the arbitrator and establishes ME1
20 . Maekawa’s algorithm-version 1 ME2. No deadlock. Unfortunately deadlock is possible! Assume 0, 1, 2 want to enter their critical sections. S0 = {0, 1, 2} S1 = {1, 3, 5} From S0= {0,1,2}, 0,2 send ack to 0, but 1 sends ack to 1; S2 = {2, 4, 5} From S1= {1,3,5}, 1,3 send ack to 1, but 5 sends ack to 2; S3 = {0, 3, 4} S4 = {1, 4, 6} From S2= {2,4,5}, 4,5 send ack to 2, but 2 sends ack to 0; S5 = {0, 5, 6} Now, 0 waits for 1 (to send a release), 1 waits for 2 (to send a S6 = {2, 3, 6} release), , and 2 waits for 0 (to send a release), . So deadlock is possible!
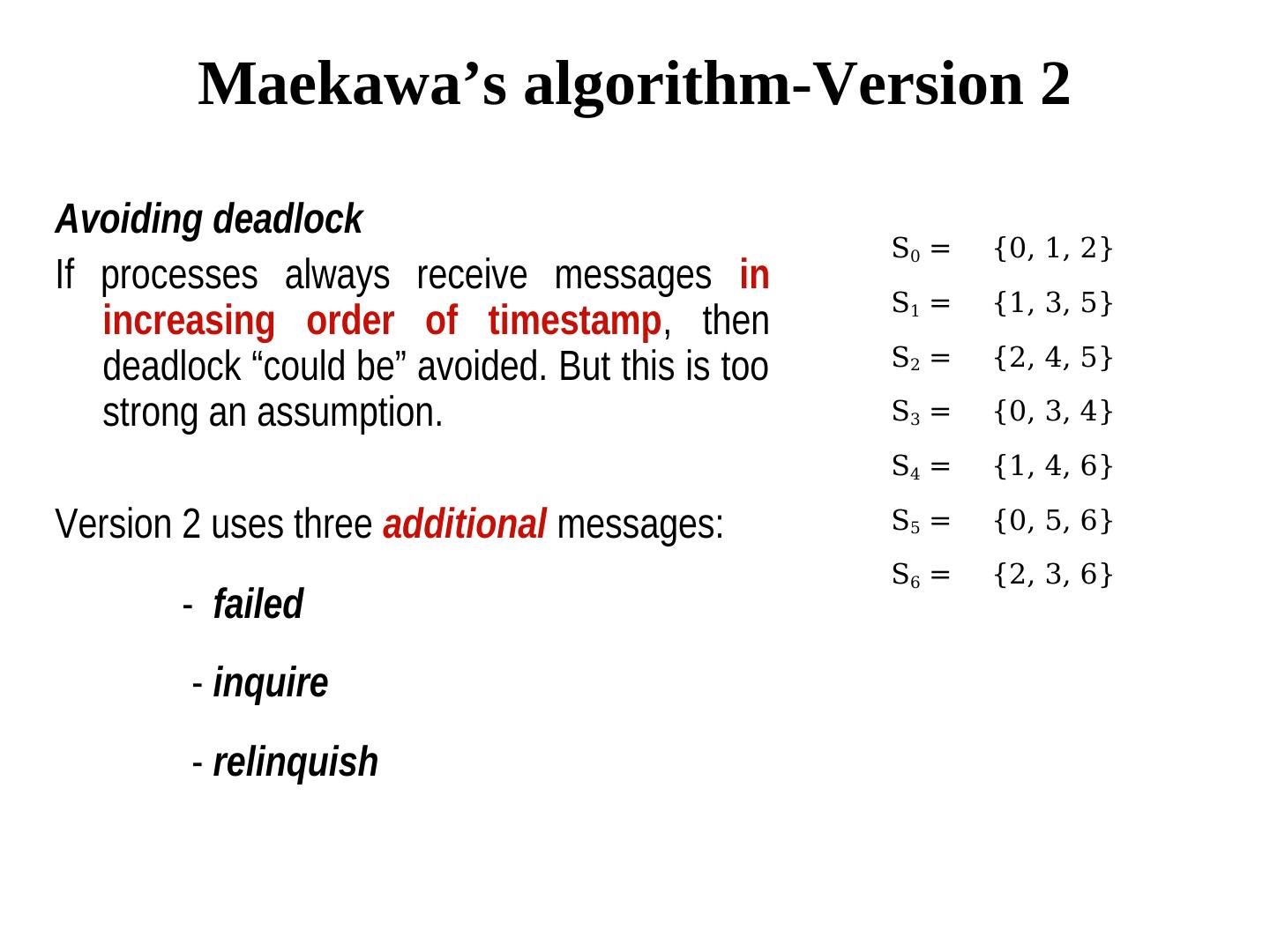
21 . Maekawa’s algorithm-Version 2 Avoiding deadlock S0 = {0, 1, 2} If processes always receive messages in S1 = {1, 3, 5} increasing order of timestamp, then deadlock “could be” avoided. But this is too S2 = {2, 4, 5} strong an assumption. S3 = {0, 3, 4} S4 = {1, 4, 6} Version 2 uses three additional messages: S5 = {0, 5, 6} S6 = {2, 3, 6} - failed - inquire - relinquish
22 . Maekawa’s algorithm-Version 2 New features in version 2 S0 = {0, 1, 2} S1 = {1, 3, 5} - Send ack and set lock as usual. S2 = {2, 4, 5} - If lock is set and a request with a larger S3 = {0, 3, 4} timestamp arrives, send failed (you have no S4 = {1, 4, 6} chance). If the incoming request has a lower timestamp, then send inquire (are you in S5 = {0, 5, 6} CS?) to the locked process. S6 = {2, 3, 6} - Receive inquire and at least one failed message send relinquish. The recipient resets the lock.
23 . Maekawa’s algorithm-Version 2 0 0 6 1 6 1 25 failed req ack inquire 18 18 5 req 2 5 2 12 12 req 4 3 4 3
24 . Comments - Let K = |Si|. Let each process be a member of D subsets. When N = 7, K = D = 3. When K=D, N = K(K-1)+1. So K =O(√N) - The message complexity of Version 1 is 3√N. Maekawa’s analysis of Version 2 reveals a complexity of 7√N • Sanders identified a bug in version 2 …
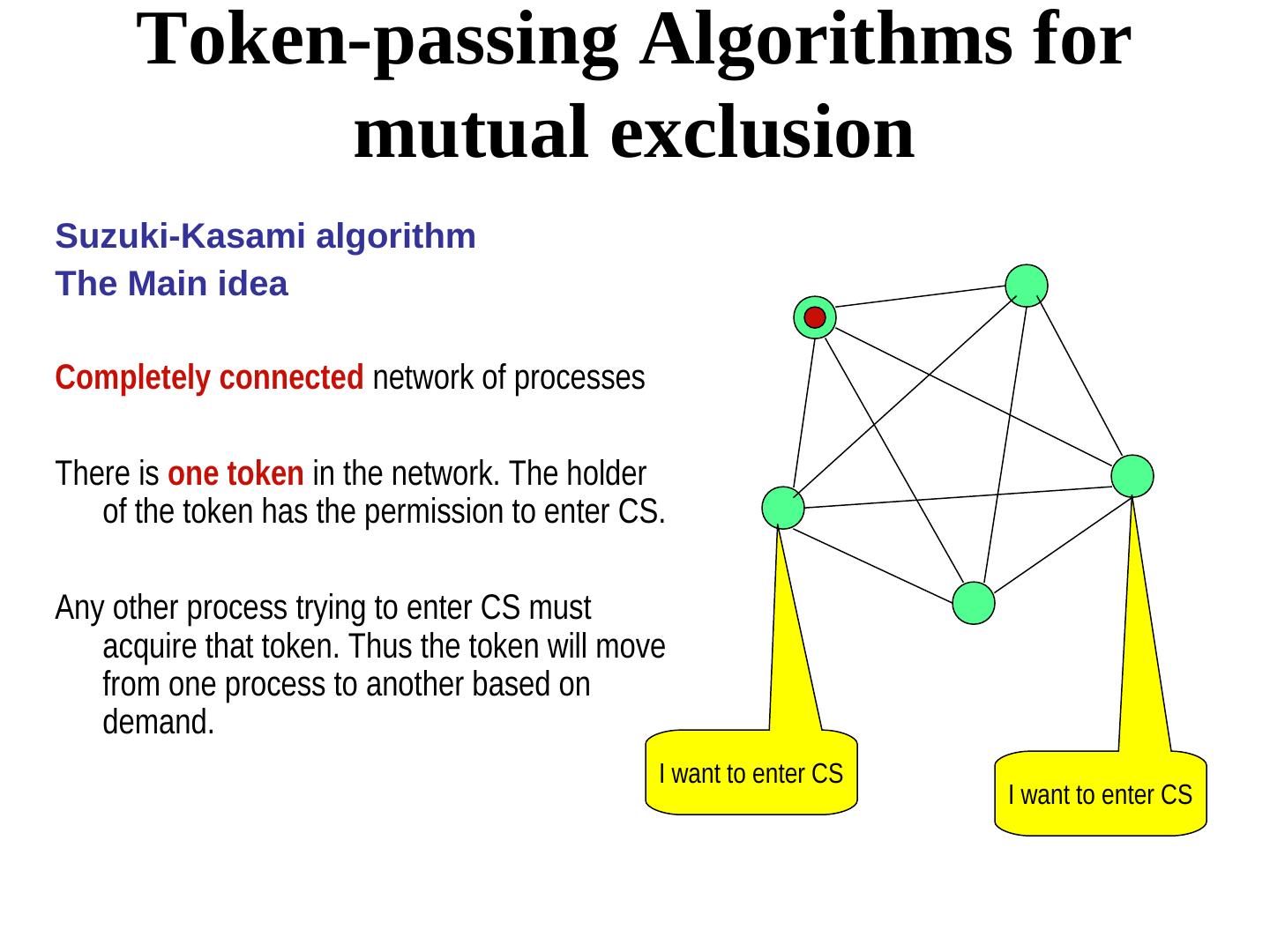
25 . Token-passing Algorithms for mutual exclusion Suzuki-Kasami algorithm The Main idea Completely connected network of processes There is one token in the network. The holder of the token has the permission to enter CS. Any other process trying to enter CS must acquire that token. Thus the token will move from one process to another based on demand. I want to enter CS I want to enter CS
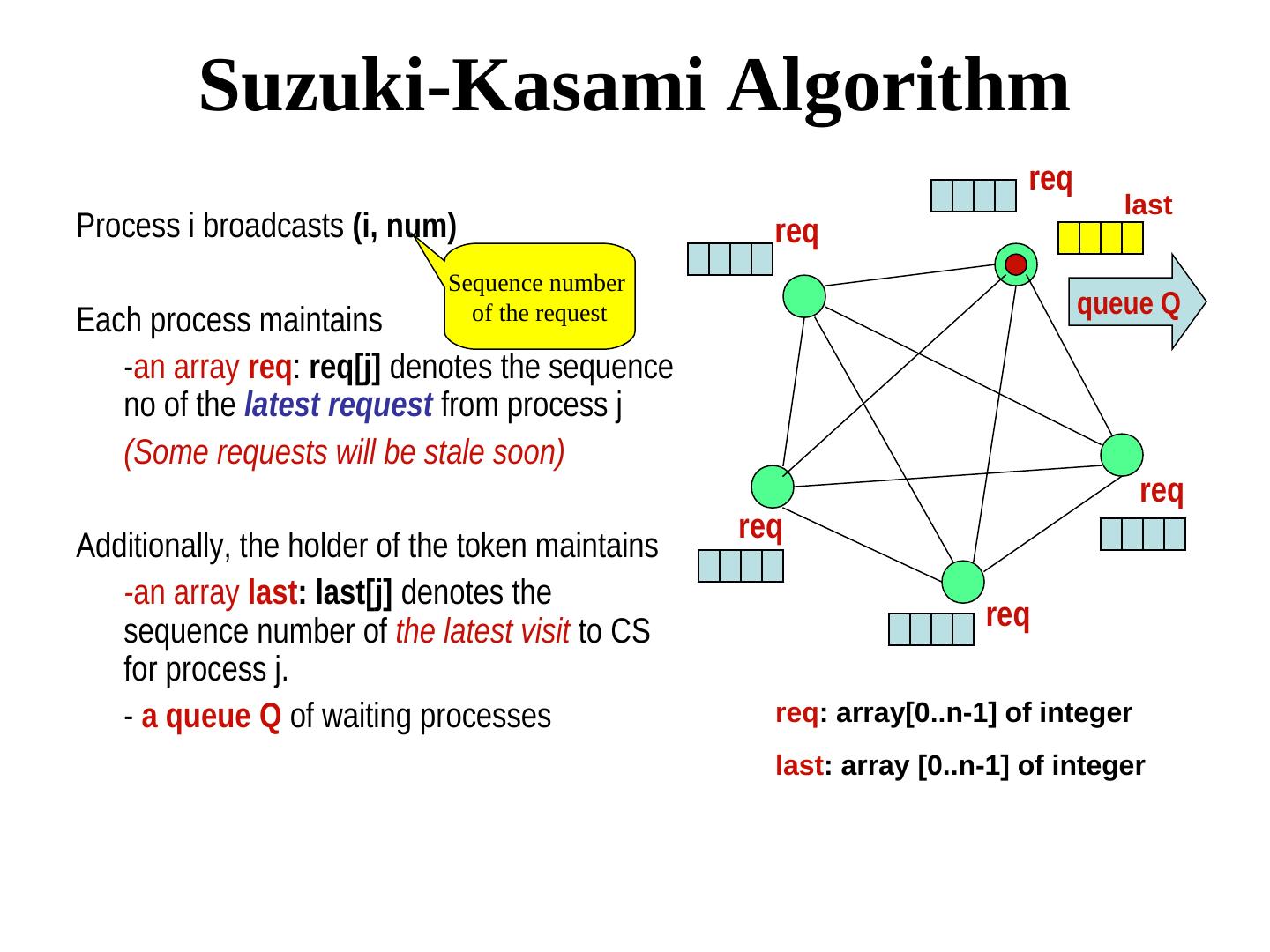
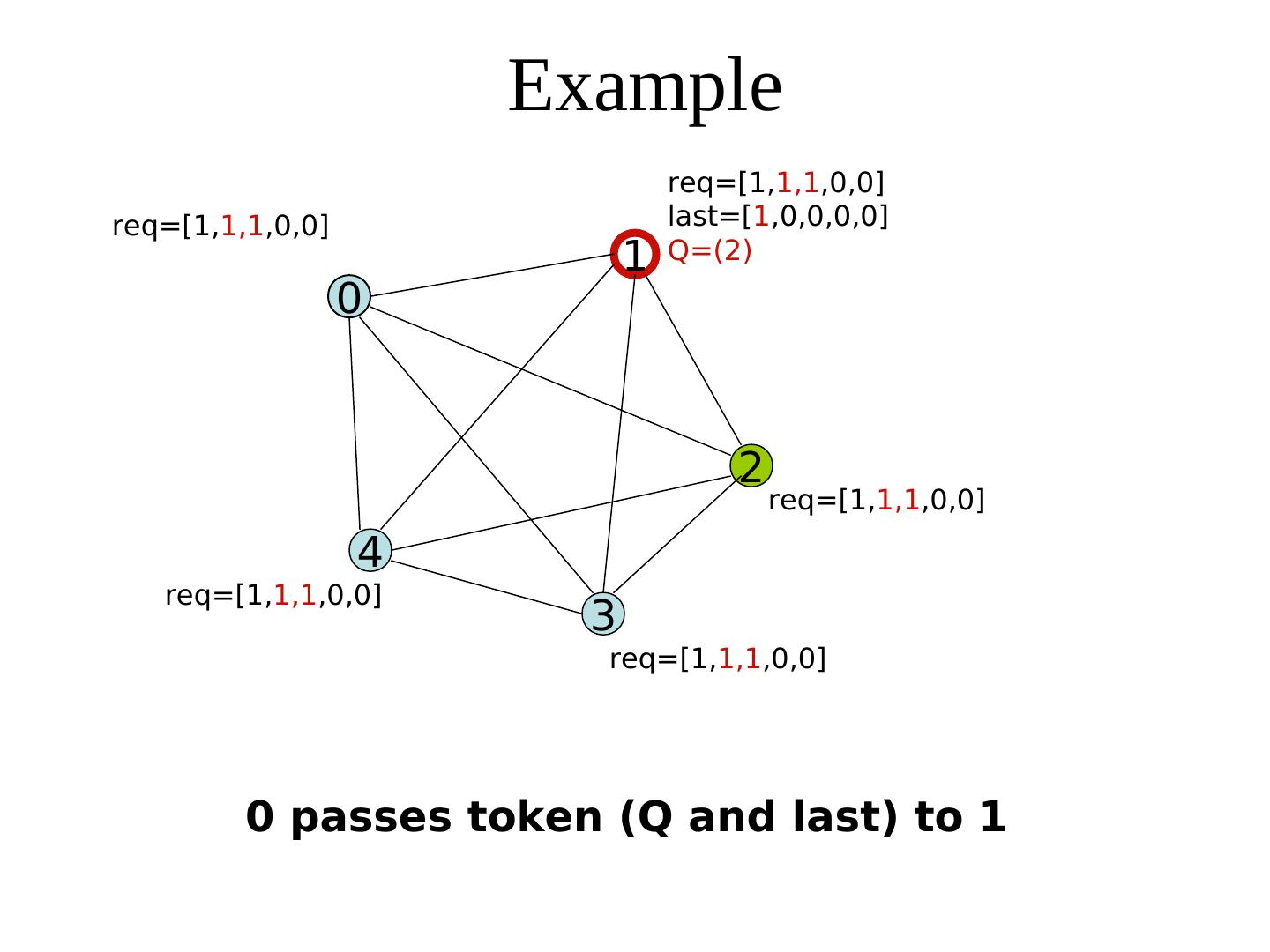
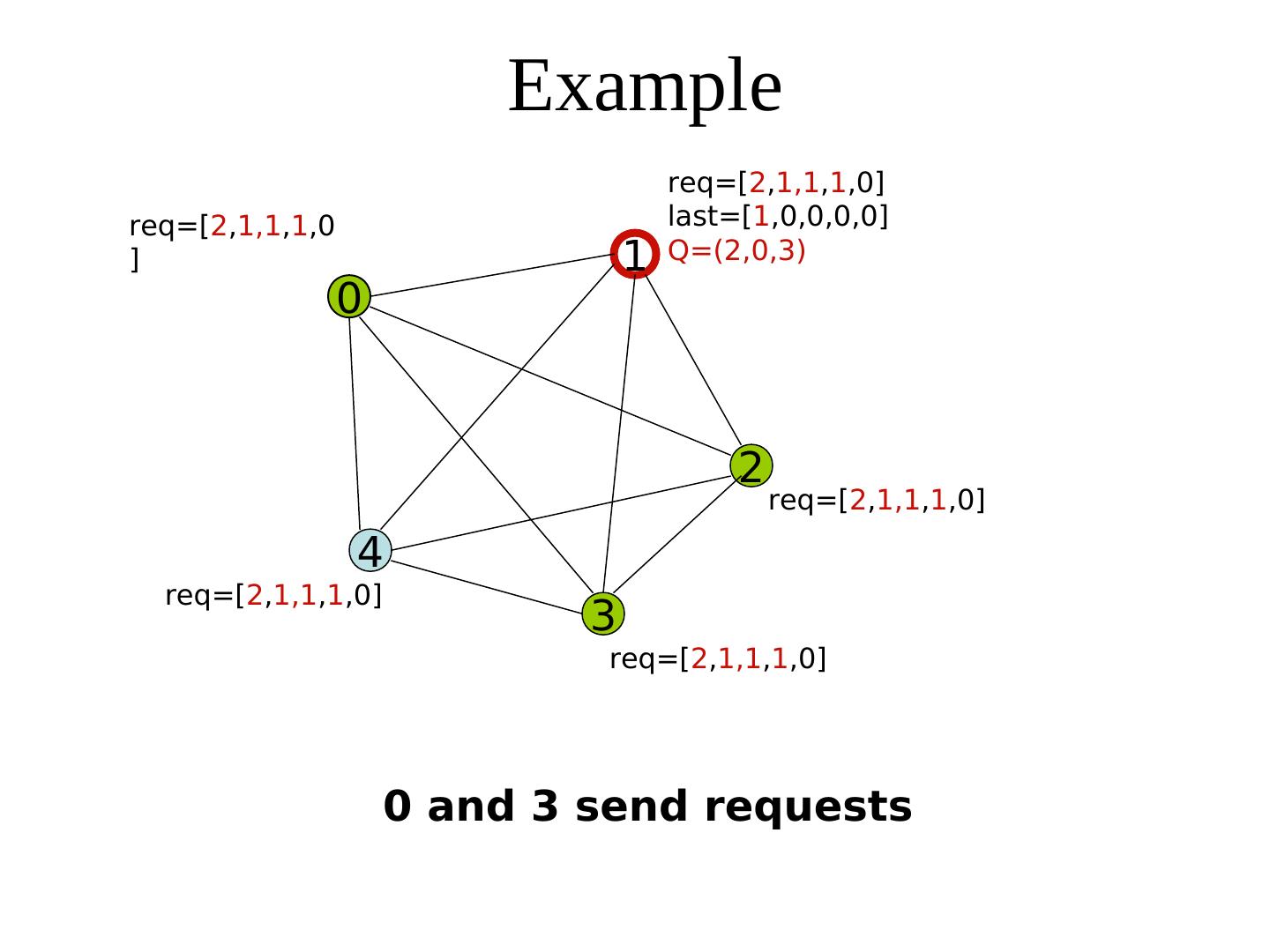
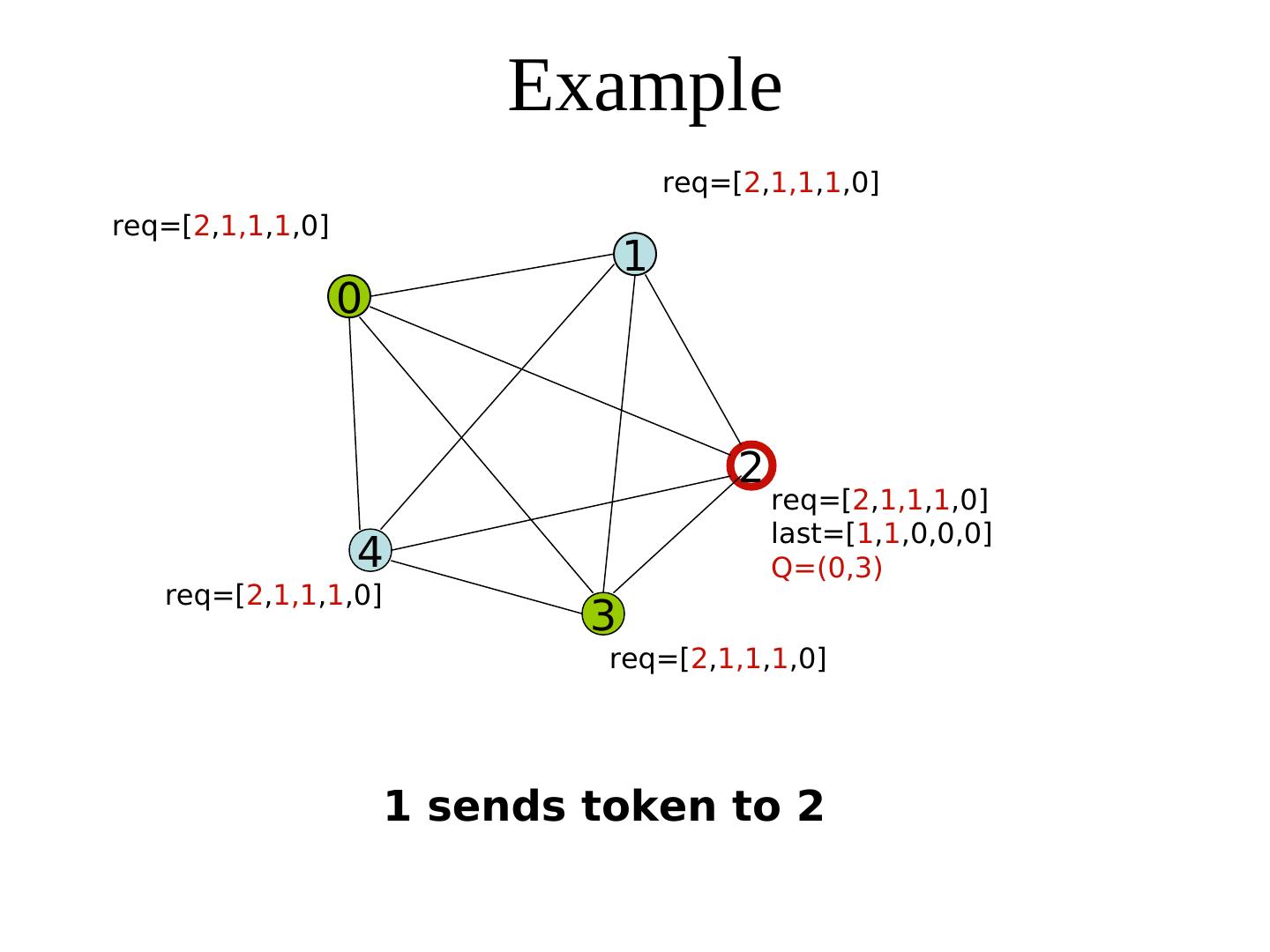
26 . Suzuki-Kasami Algorithm req last Process i broadcasts (i, num) req Sequence number queue Q Each process maintains of the request -an array req: req[j] denotes the sequence no of the latest request from process j (Some requests will be stale soon) req req Additionally, the holder of the token maintains -an array last: last[j] denotes the sequence number of the latest visit to CS req for process j. - a queue Q of waiting processes req: array[0..n-1] of integer last: array [0..n-1] of integer
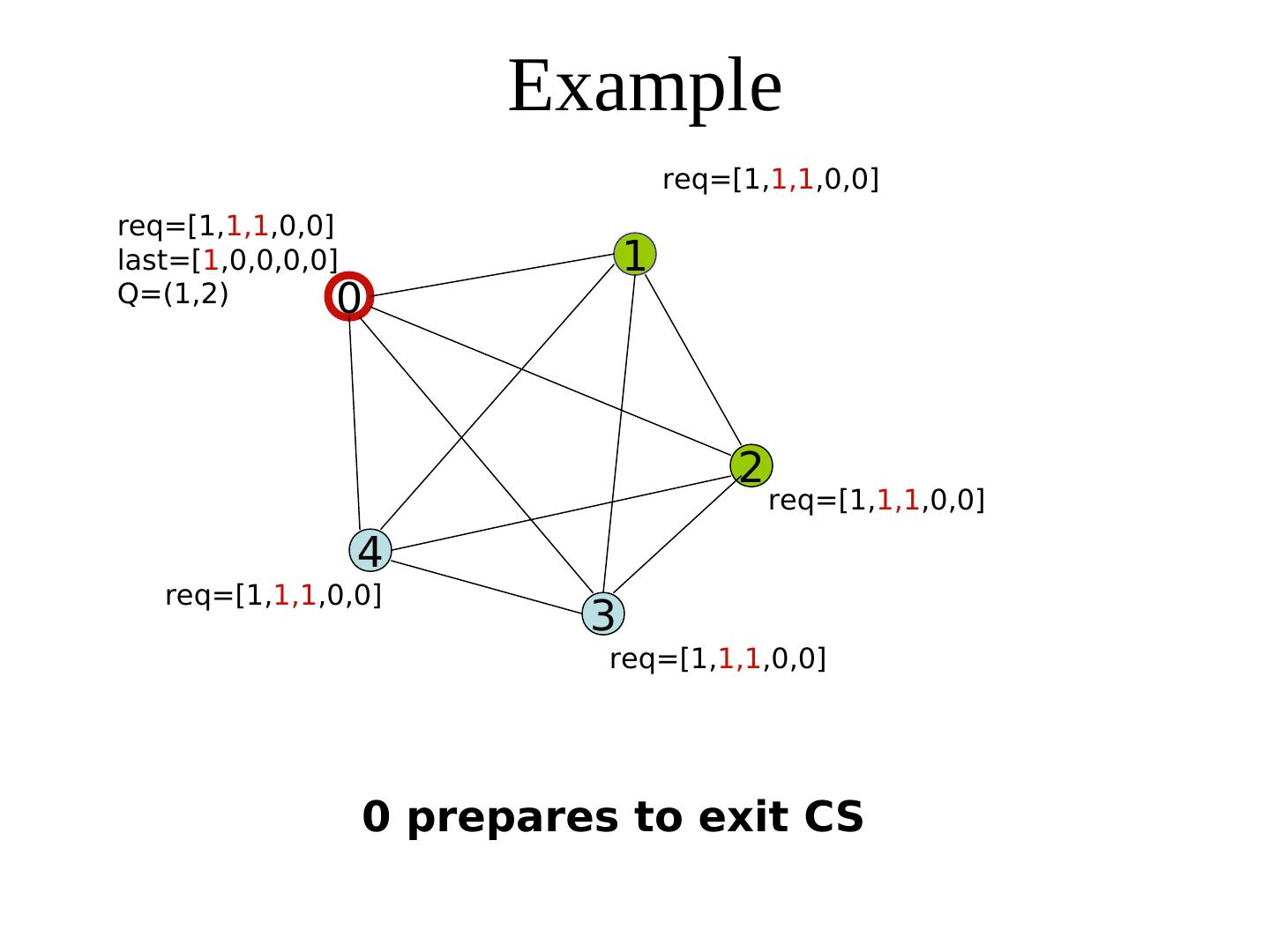
27 . Suzuki-Kasami Algorithm When a process i receives a request (k, num) from process k, it sets req[k] to max(req[k], num). The holder of the token --Completes its CS --Sets last[i]:= its own num --Updates Q by retaining each process k only if 1+ last[k] = req[k] (This guarantees the freshness of the request) --Sends the token to the head of Q, along with the array last and the tail of Q Req: array[0..n-1] of integer In fact, token ≡ (Q, last) Last: Array [0..n-1] of integer
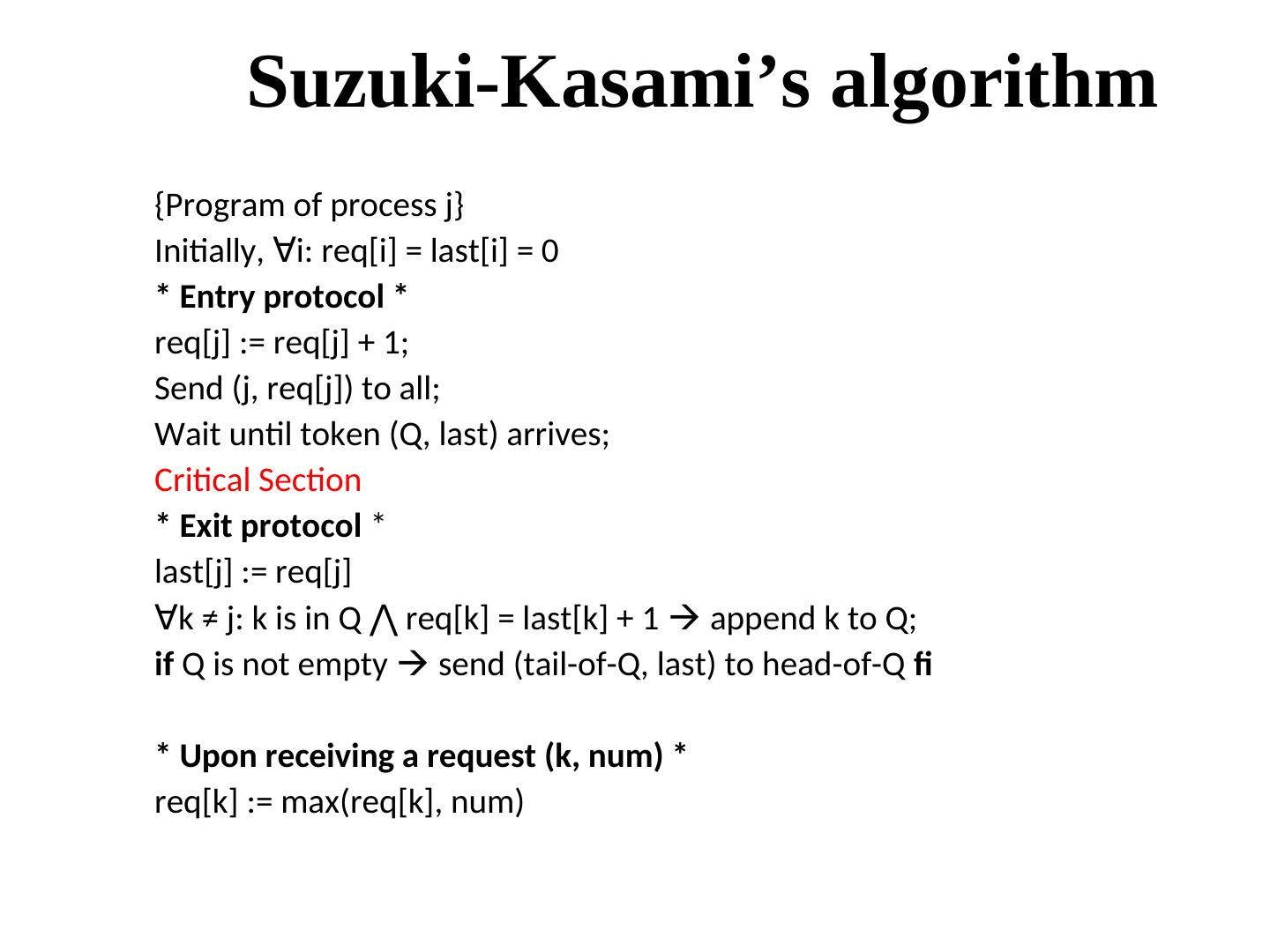
28 . Suzuki-Kasami’s algorithm {Program of process j} Initially, ∀i: req[i] = last[i] = 0 * Entry protocol * req[j] := req[j] + 1; Send (j, req[j]) to all; Wait until token (Q, last) arrives; Critical Section * Exit protocol * last[j] := req[j] ∀k ≠ j: k is in Q ⋀ req[k] = last[k] + 1 req[k] = last[k] + 1 append k to Q; if Q is not empty send (tail-of-Q, last) to head-of-Q fi * Upon receiving a request (k, num) * req[k] := max(req[k], num)
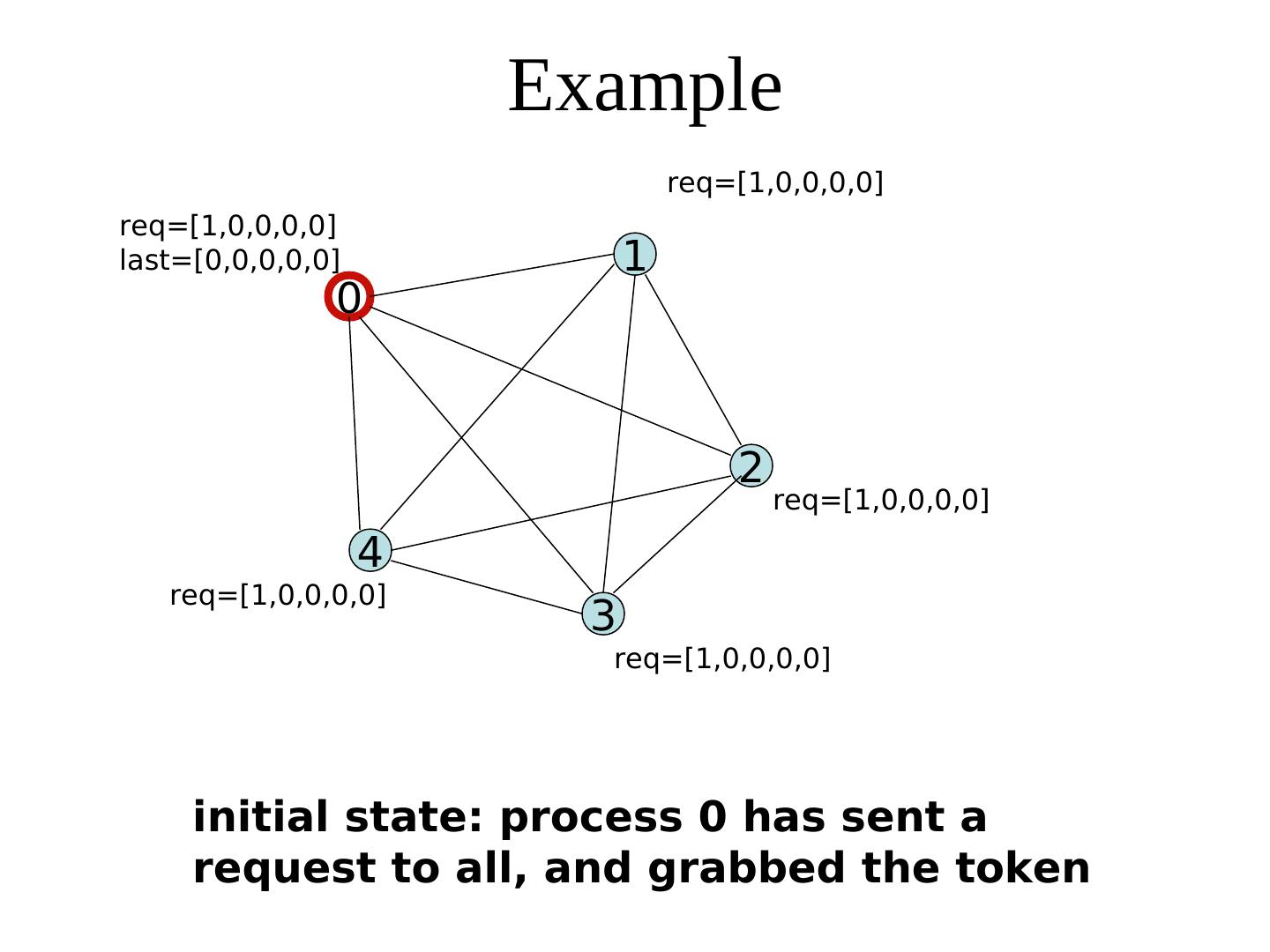
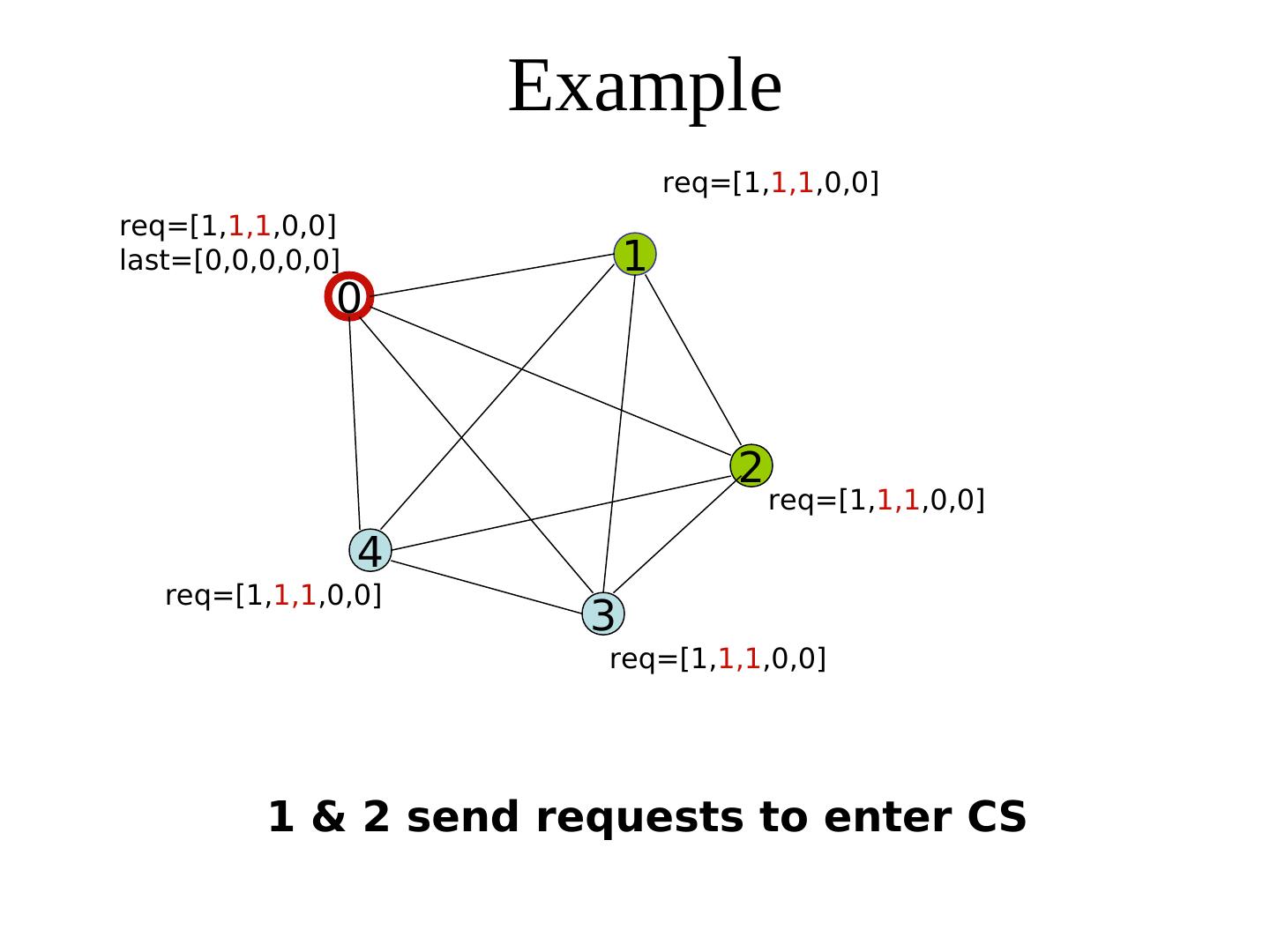
29 . Example req=[1,0,0,0,0] req=[1,0,0,0,0] last=[0,0,0,0,0] 1 0 2 req=[1,0,0,0,0] 4 req=[1,0,0,0,0] 3 req=[1,0,0,0,0] initial state: process 0 has sent a request to all, and grabbed the token