- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
slides
展开查看详情
1 . Phu H. Phung University of Dayton Abhinav Mohanty , Rahul Rachapalli and Meera Sridhar University of NC at Charlotte MOBILE SECURITY TECHNOLOGIES (MOST) 2017 Thursday , May 25, 2017 The Fairmont Hotel, San Jose, CA HybridGuard : A Principal-based Permission and Fine-Grained Policy Enforcement Framework for Web-based Mobile Applications
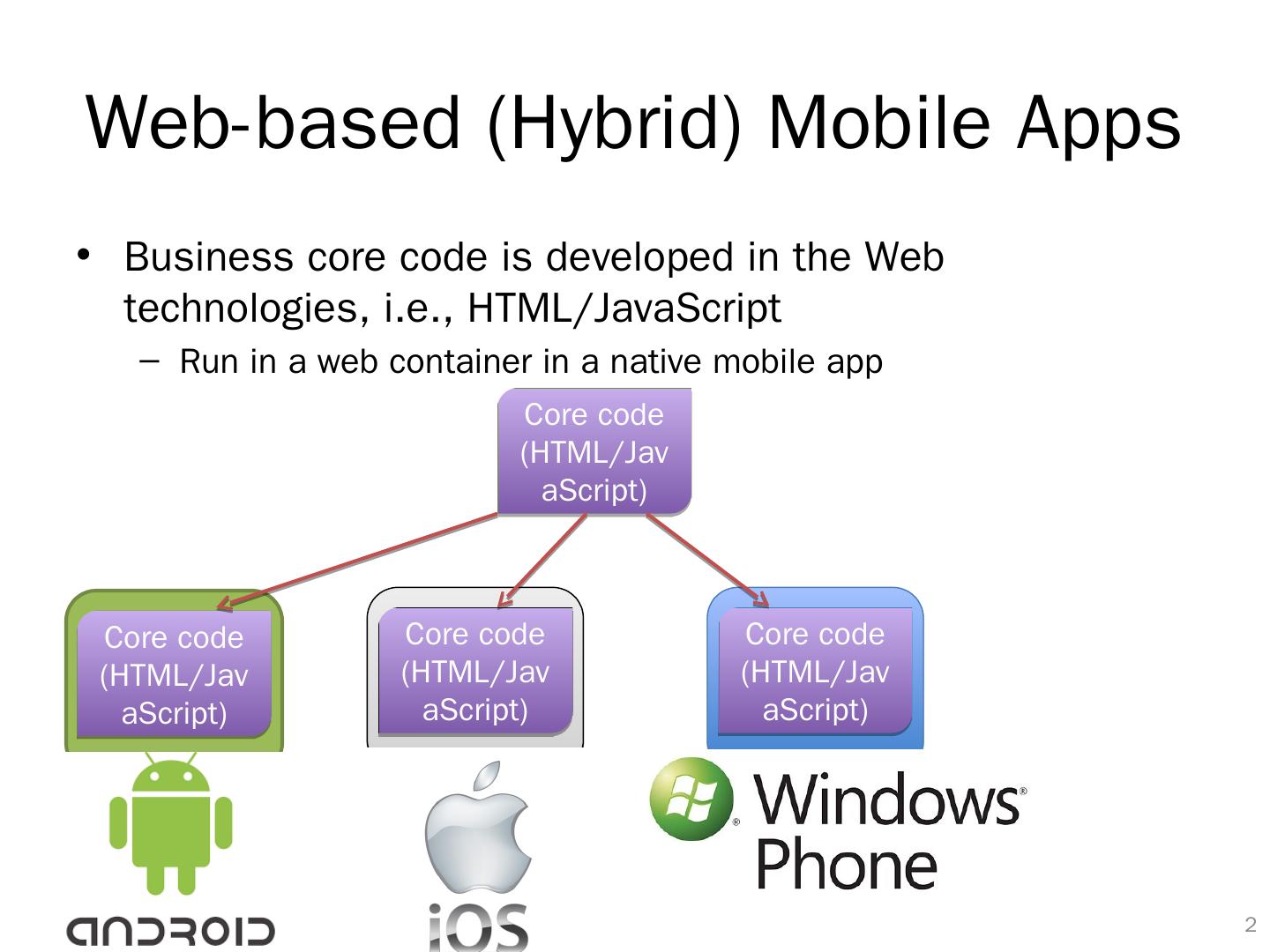
2 .Core code ( HTML/JavaScript) Web-based (Hybrid) Mobile Apps Business core code is developed in the Web technologies, i.e., HTML/JavaScript Run in a web container in a native mobile app 1 Core code ( HTML/JavaScript) Core code ( HTML/JavaScript) Core code ( HTML/JavaScript)
3 .Hybrid Apps – Interaction with Mobile Device 2 Credit: http :// www.xrgsystems.com /
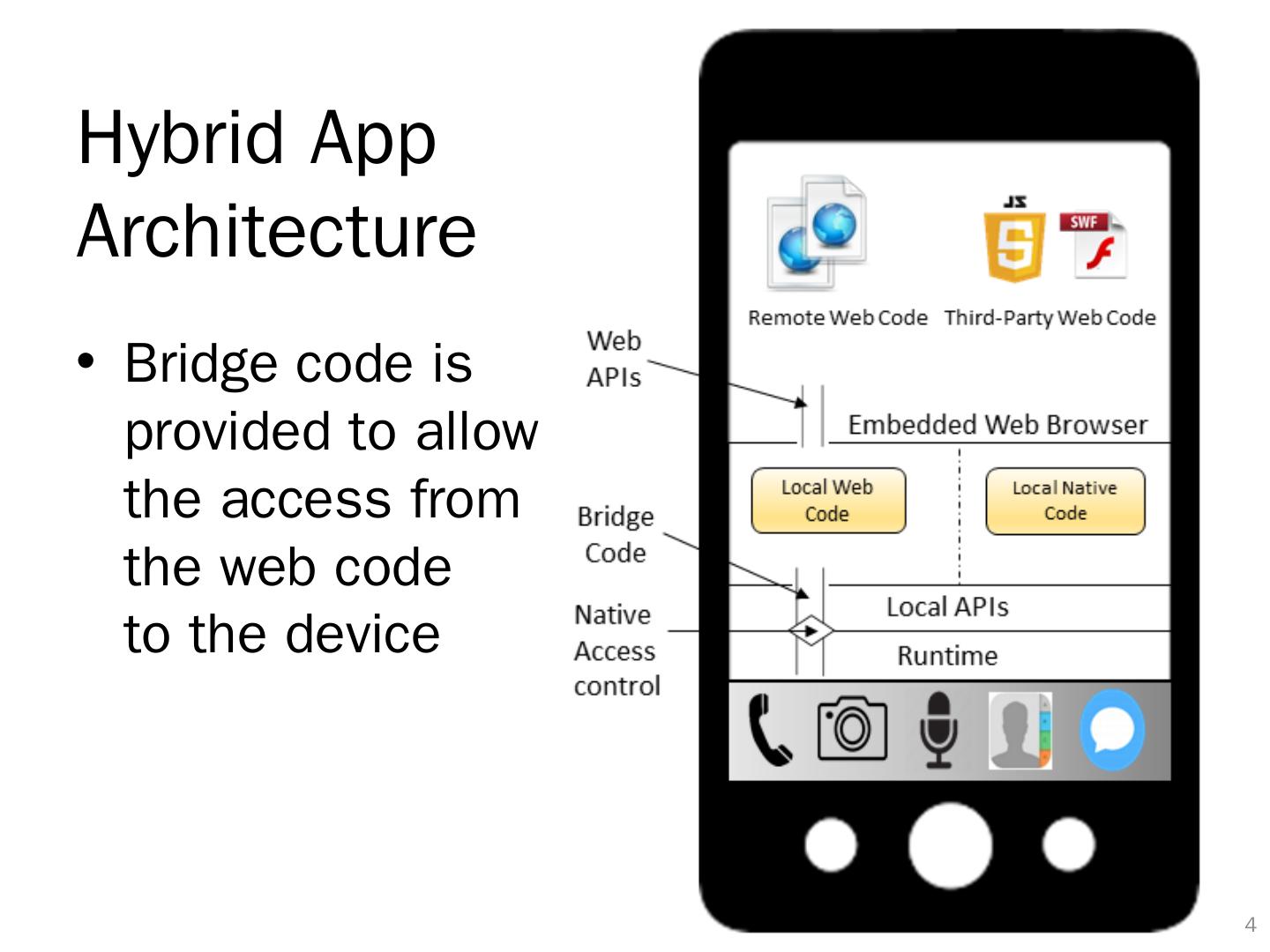
4 .Hybrid App Architecture 3 Bridge code is provided to allow the access from the web code to the device
5 .JavaScript Bridge in Web-based Apps 4 //implemented in a native language, // e.g., Java for Android addJavascriptInterface ( new MyObject () , " myinterface " ); //core code in JavaScript myinterface. sendSMS (..) ; MyObject () myinterface
6 .Hybrid Mobile Frameworks The JavaScript Bridge is typically provided automatically by hybrid mobile development frameworks E.g., Cordova ( PhoneGap ) , Ionic, Onsen , React Native, and more than 70 others JavaScript Bridge APIs are provided through plugins Native implementations and JavaScript interfaces 5
7 .Permission Model in Mobile Apps Users can grant permissions for a mobile app to access the device resources such as geolocation , SMS, … Once a permission is granted (either static or dynamic), there is no way to control how the app uses the permissions 6
8 .Permission in Web-based Mobile Apps Any JavaScript code can access the exposed JavaScript bridge APIs 7 MyObject () myinterface Local JavaScript Third-party JavaScript
9 .Security in Web-based Mobile Apps Domain Whitelisting, e .g., in Cordova Allow code from some whitelisted domains can access Content Security Policy Limit the access of JavaScript code based on domain 8 These mechanisms are coarse-grained: Once an access is granted, no more control on that
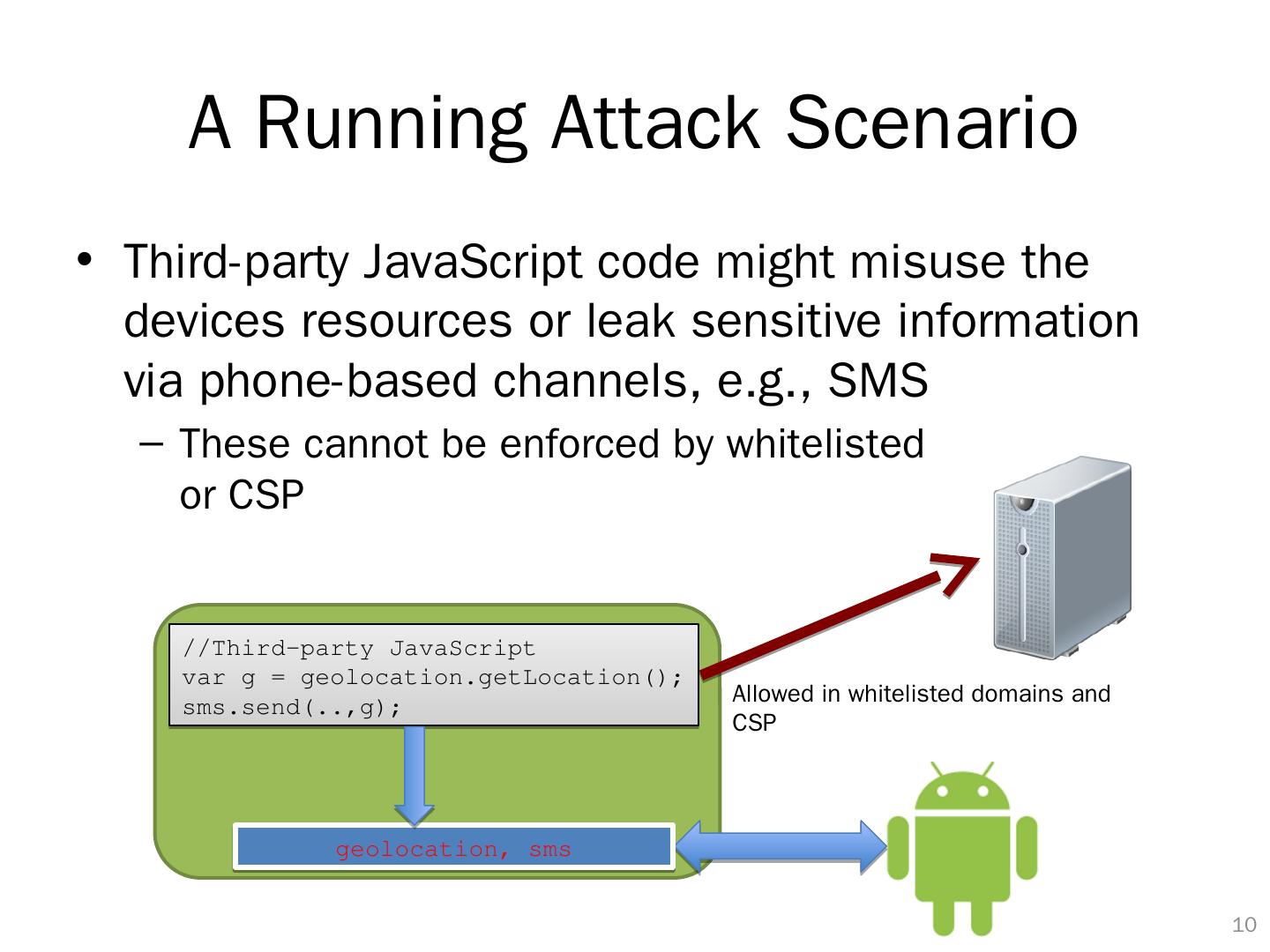
10 .A Running Attack Scenario Third-party JavaScript code might misuse the devices resources or leak sensitive information via phone-based channels, e.g., SMS These cannot be enforced by whitelisted or CSP 9 geolocation , sms //Third-party JavaScript var g = geolocation.getLocation (); sms.send (..,g); Allowed in whitelisted domains and CSP
11 .The state-of-the-art Existing JavaScript security solutions Do not cover phone-related channels, e.g., sms Some hybrid app security solutions focus on a specific platform, e.g., WebView in Android [ Georgiev et al., WWW’15], [ Tuncay et al ., CCS’16] Some approaches modify the hybrid framework, e.g., PhoneGap [ Georgiev et al., NDSS’15 ], [Jin et al., ISC’15] Few work can enforce principal-based policies for mobile apps but do not protect the web environment, e.g., [ Georgiev et al., WWW’15 ] 10
12 .Our Motivation Provide a framework to allow hybrid app developers to define and enforce principal-based access control and fine-grained policies Do not depend on a specific mobile platform Work with any hybrid frameworks 11
13 .Outline Motivation Our Approach - HybridGuard Implementation Evaluation Concluding Remarks 12
14 .Threat Model Hybrid Apps are legitimate and trusted by the users Permissions are granted Content Security Policy (CSP) is deployed to e.g., present Cross-site Scripting Attacks In-scope threats - third-party JavaScript code, e.g., advertisements, allowed by the developers in CSP: Benign but under the control of an attacker Malicious by intentions 13
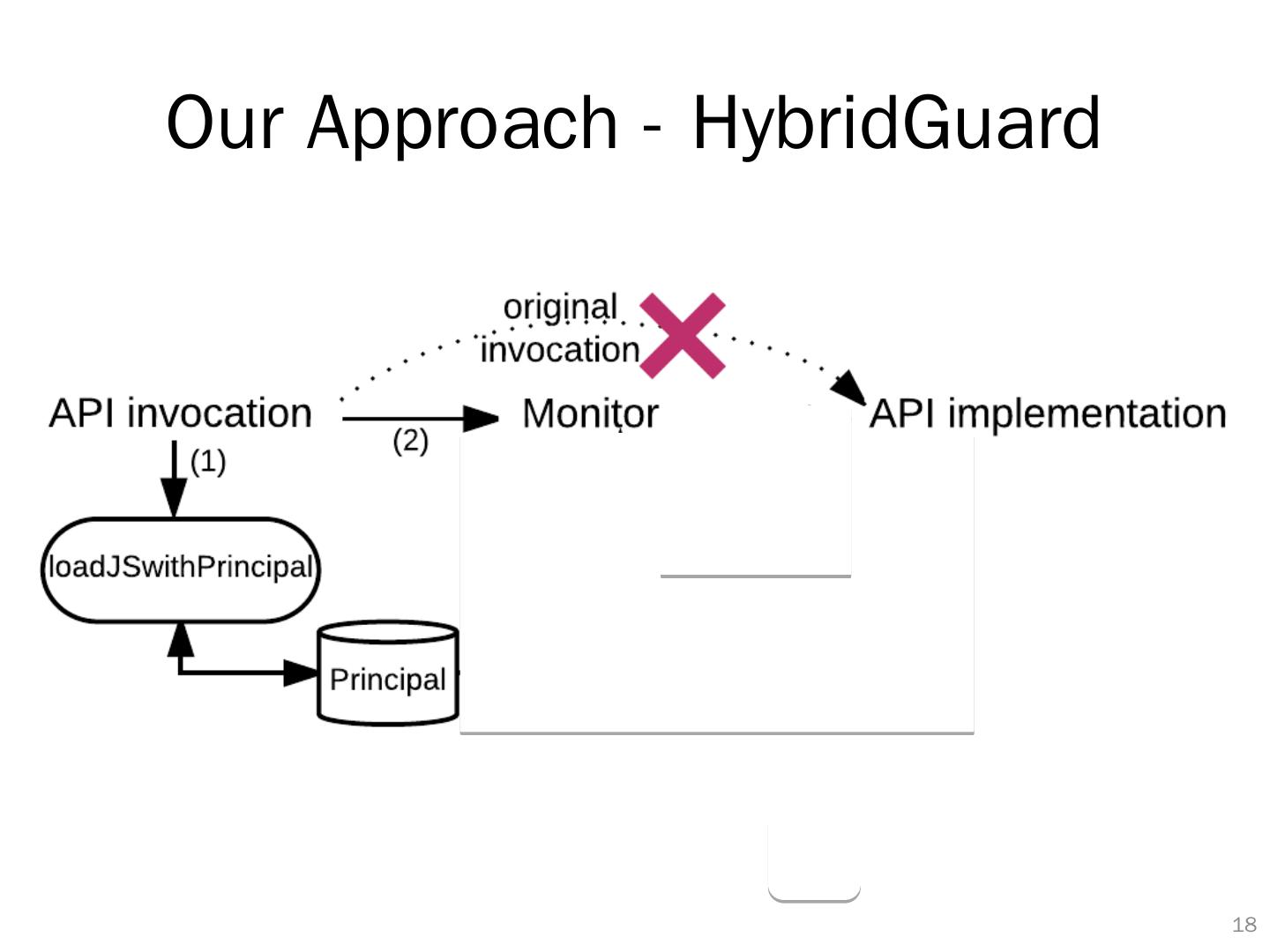
15 .Our Approach 14 Load a piece of JavaScript code under a principal name, i.e.,: Replace the original JavaScript inclusion <script src =" http://third-party.com/script.js "> by our interface: loadJSwithPrincipal (" principal", "http ://third-party.com/ script.js ") Wrap critical JavaScript APIs (Web APIs + JavaScript Bridge APIs ) Enforce policies based on caller’s principals
16 .JavaScript Invocation 15
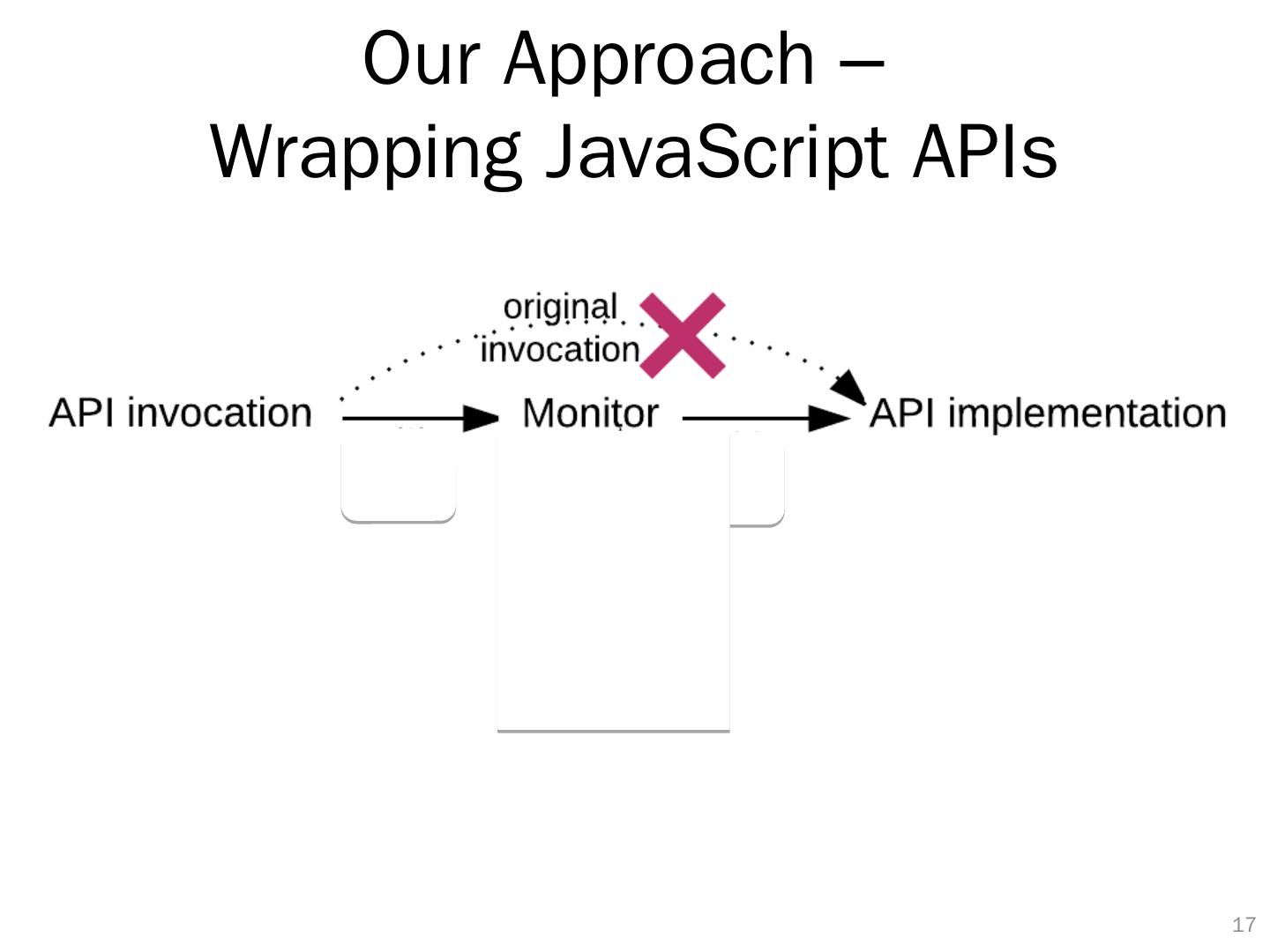
17 .Our Approach – Wrapping JavaScript APIs 16
18 .Our Approach - HybridGuard 17
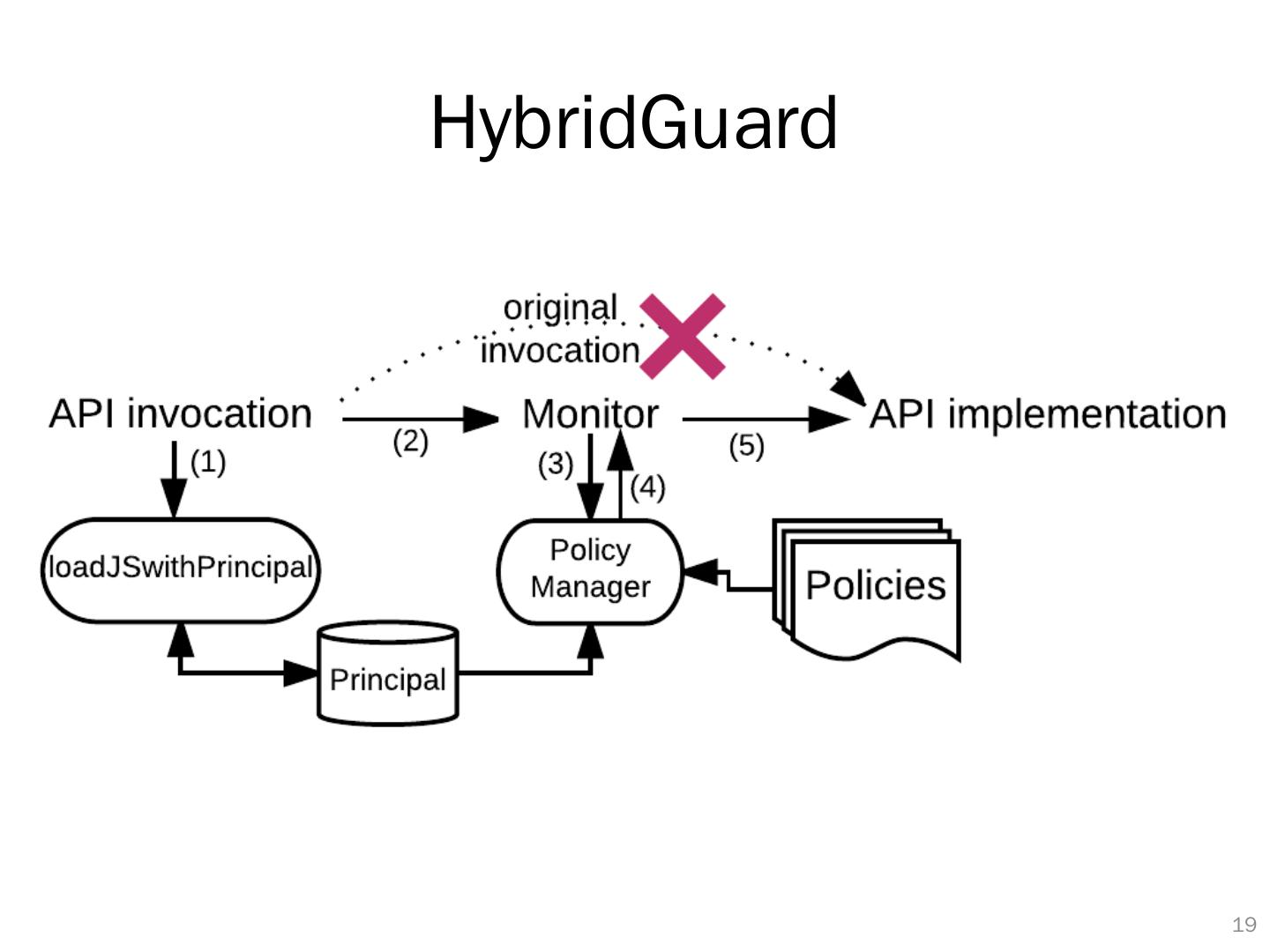
19 .HybridGuard 18
20 .Wrapping JavaScript (Web/Bridge) APIs 19 sms.send (…); orig_sms_send = sms.send ; sms.send = function(){ } if ( policyCheck (..)) execute ( orig_sms_send , ..); else{..} 1. Keep the original reference 2. Redefine the reference 3. Check policy to control the execution Security code is injected before any other JavaScript code to monitor them
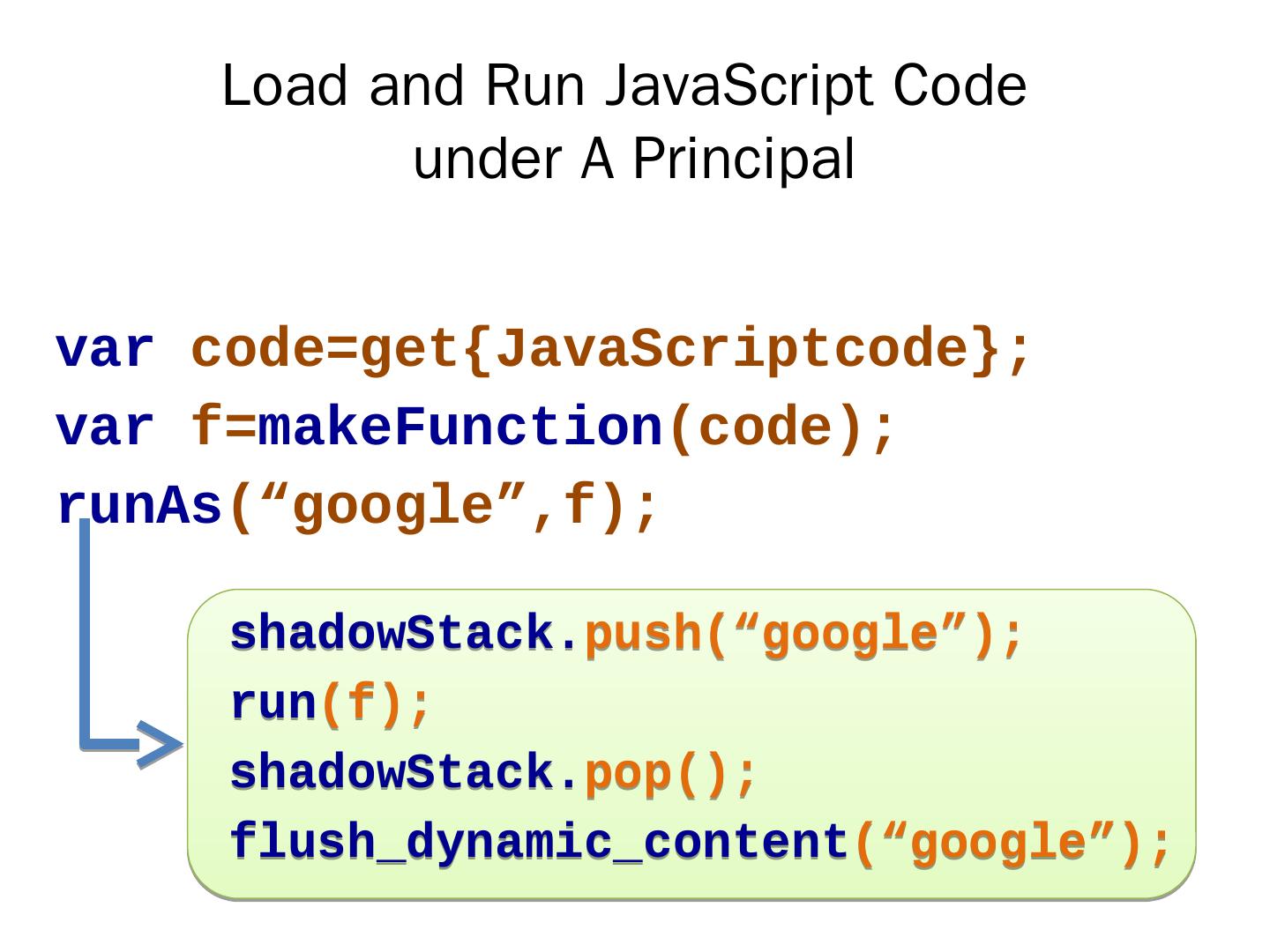
21 .Principal Management and Tracking Based on “run-to-completion” execution model of JavaScript We maintain a shadow stack to track the execution of each principal We catch dynamic generated code and event handlers Load these code under the same principal that generates them 20
22 .Load and Run JavaScript Code under A Principal var code=get { JavaScriptcode }; var f= makeFunction (code); runAs (“ google ”,f); shadowStack. push (“ google ”); run (f); shadowStack. pop (); flush_dynamic_content (“ google ”);
23 .Principal Tracking Example 22
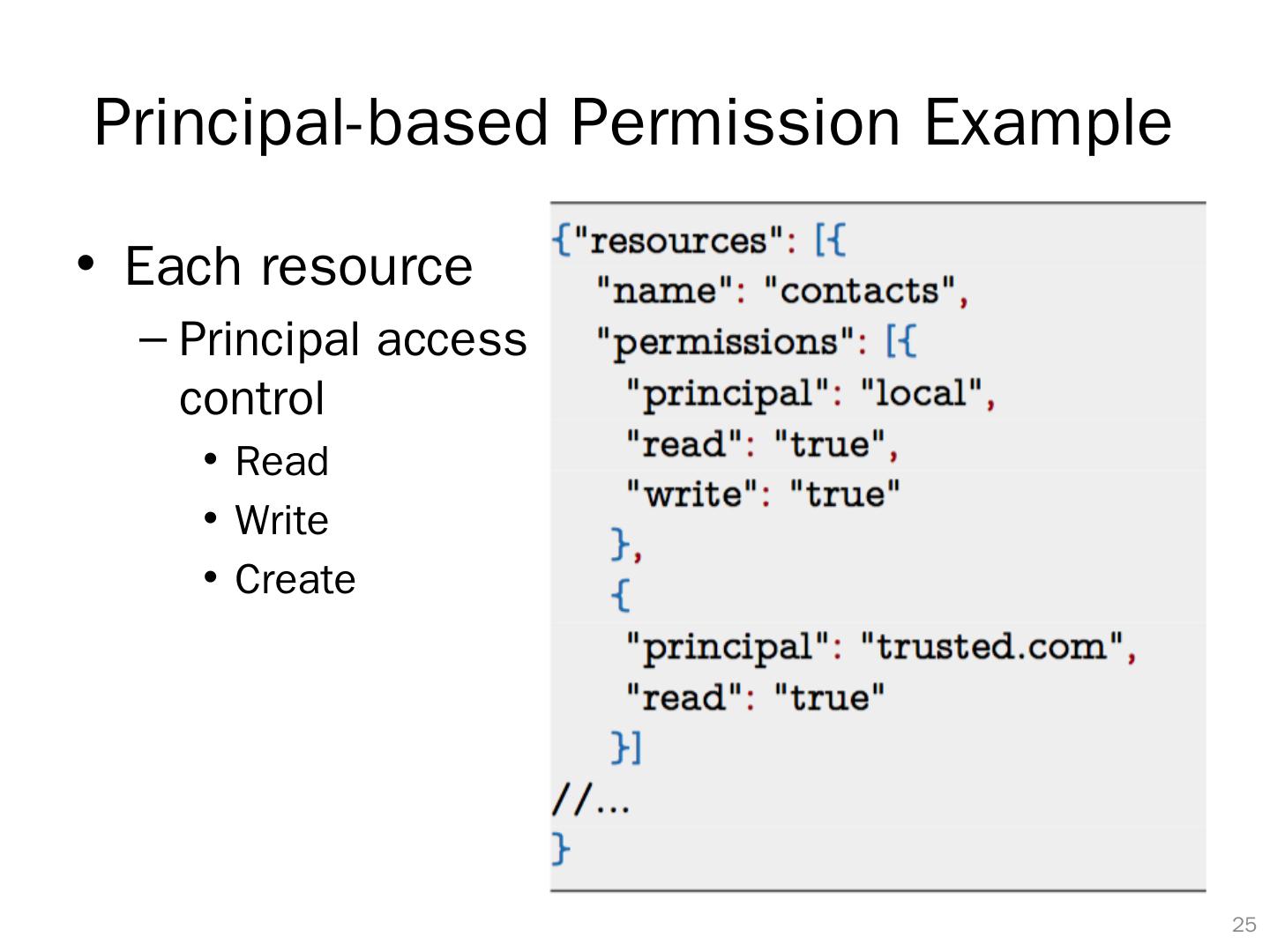
24 .Principal-based Permission Wrap the JavaScript Bridge APIs Grant access to these APIs based on principal E.g.: "trusted" principal can have full access to all resources "local" principal can have access to resources A, B "remote" principal can have access to resources C 23
25 .Principal-based Permission Example Each resource Principal access control Read Write Create 24
26 .Stateful and Fine-grained Security Policies Based on Behavior of the code Principal of the code E.g.: Disallow the sms.send if the untrusted principal has accessed the geolocation API 25
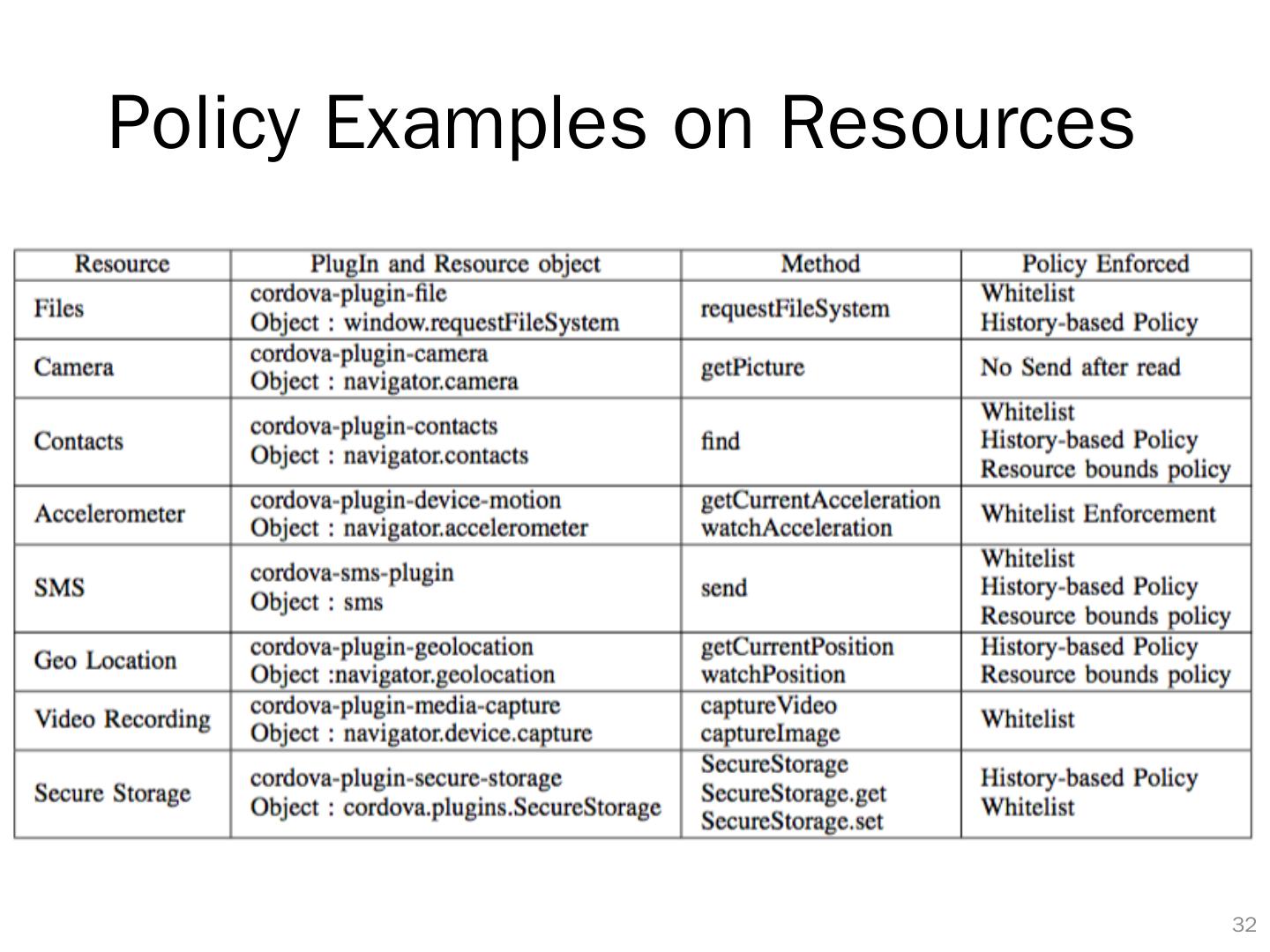
27 .More Fine -grained Policy Patterns Resource bounds Policy Limit the number of accesses to a resource E .g.,: limit the number of sms send Whitelist Policies A resource access is allowed only under some conditions E.g.,: allow sms send to some predefined receipts History-based Policies Policies depending on the previous execution status E.g.,: no SMS sending after contact list is read Any custom policies, e.g., preventing UI attacks 26
28 .Complete Mediation Web APIs: We apply the secure wrapper implementations for JavaScript in the literature Ensure that our monitor implementation is tamper-proof from potentially malicious code JavaScript bridge APIs Direct access to native APIs is disallowed We rely on app developers to identify bridge APIs and wrap them with our interface 27
29 .HybridGuard Security 28 By lexical scoping Keeping original APIs with a protected lexical scope ; wraps all channels generating JS code at runtime Labeling all dynamically written content with the authoring principal