- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
05-物联网传感器注册,传感器不准确的风险
展开查看详情
1 .Lecture 5: Azure IoT Hub and The Sensor Lifecycle Ken Birman Spring, 2019 http://www.cs.cornell.edu/courses/cs5412/2019sp 1
2 .The future smart world http://www.cs.cornell.edu/courses/cs5412/2019sp 2 http://www.plmconnections.com Puzzles… Who “builds” this world? Will they maintain it properly? Can the devices be trusted?
3 .Long-Standing Issue with Sensors People have talked about using sensors to create a “smart world” since 1980’s, but it hasn’t been as simple as they imagined! It is fairly easy to put RFID tags on devices, but those are passive. In fact “full fledged” IoT with sophisticated sensors and actuators poses a wide range of challenges that we are only starting to appreciate. http://www.cs.cornell.edu/courses/cs5412/2019sp 3
4 .Iot is everywhere, but poorly managed Your Internet router, and networked printer Cortana/Alexa/Siri/Google Nest Your TV and home entertainment system The network-connected microwave, fridge, range. Smart hot-water heater, and A/C, and room heating units Smart power meter, to connect them all together Smart water meter (might even be able to diagnose leaks) Solar panels on the roof, energy storage batteries in the wall http://www.cs.cornell.edu/courses/cs5412/2019sp 4
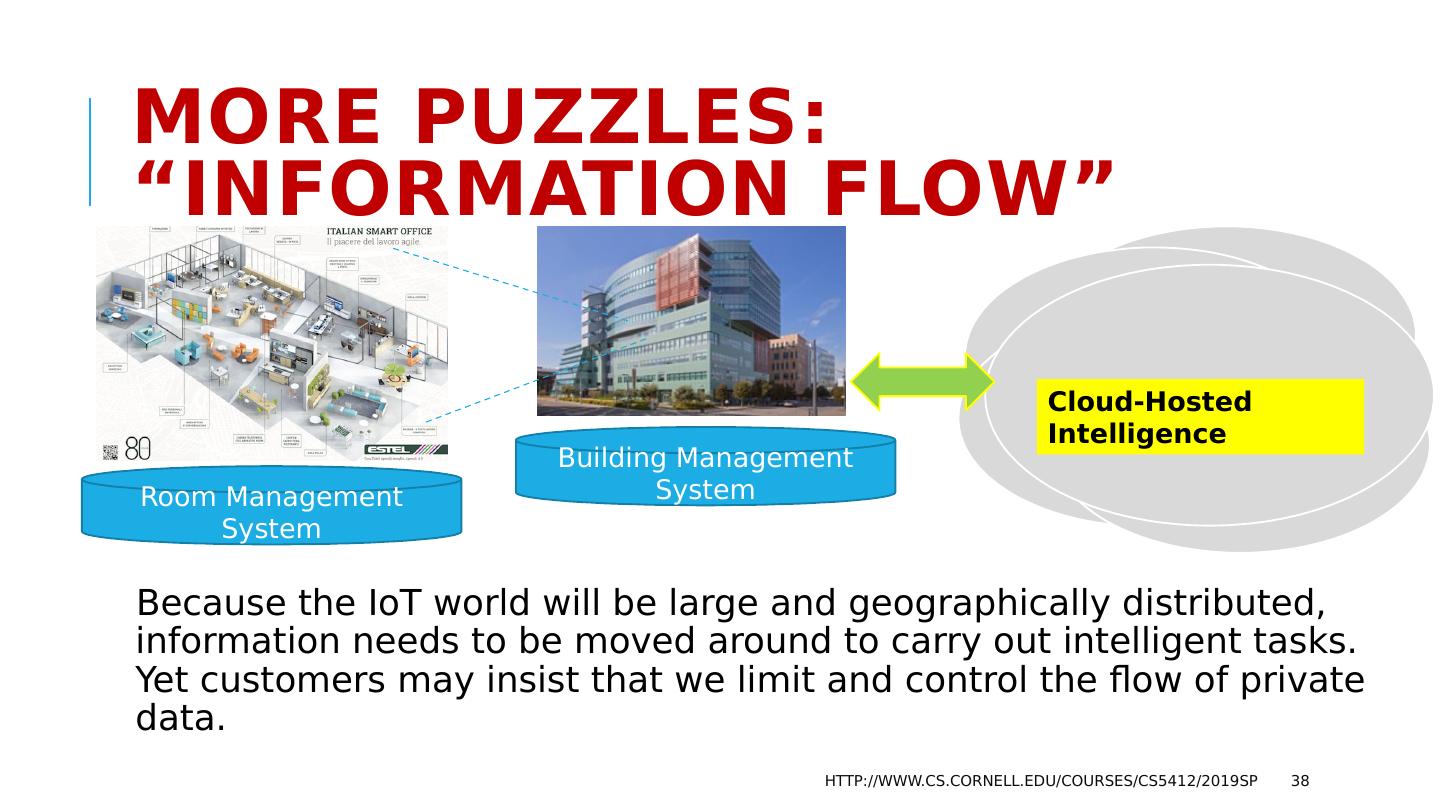
5 .I o T doesn’t need to be obvious! Estel : Italian design firm specializing in smart offices The technology is subtle but pervasive. Dozens of smart devices http://www.cs.cornell.edu/courses/cs5412/2019sp 5
6 .… Examples of I o T in the office Room occupancy, temperature, humidity sensors and sector control Sensor to detect exterior light, actuator to control lights & window shades Desktop microphone for conferencing Smart copier/scanner with network-enabled functionality The elevator system The expresso machine that automatically orders new coffee packs Door locks that check ID cards http://www.cs.cornell.edu/courses/cs5412/2019sp 6
7 .… Even the electric power grid is smart Most of the world’s bulk electric power systems are becoming smart This is IoT on a “grand scale” and covers more than just power: coal/gas delivery, scheduling of power plants, maybe even water delivery, too. But this means that the power grid will need to keep a close eye on everything using electric power, or generating it. More IoT! http://www.cs.cornell.edu/courses/cs5412/2019sp 7
8 .… the list really is endless Smart farm Smart city Smart highway Smart emergency first-response…. http://www.cs.cornell.edu/courses/cs5412/2019sp 8
9 .Who keeps this stuff Secure + Robust? Even if every light bulb “could” have a computer in it, why would this benefit anyone, and who would make sure the broken ones are replaced? How can we protect privacy and ensure that these things are secure? What costs could be incurred for violations? What if a sensor malfunctions? Can we figure out that it needs repair? http://www.cs.cornell.edu/courses/cs5412/2019sp 9
10 .Situation today? Very poorly managed, huge numbers of IoT devices yet very little attention to software upgrades, network security issues raised. There are network-enabled printers that turned out to have entire spy computing systems embedded in them, to retain copies of everything. Largest “zombie/bot” population? By one estimate, it may be Internet Wifi routers with default password settings! http://www.cs.cornell.edu/courses/cs5412/2019sp 10
11 .More puzzles: Contextualization How do IoT devices know which room they are in? Alexa, adjust the shades to block the glare on my display Siri, use active noise cancellation to block that street noise Cortana, find me a nearby conference room we can book for an hour. … in addition to the IoT devices themselves we will need increasingly detailed “environmental maps” for everything, down to individual rooms! http://www.cs.cornell.edu/courses/cs5412/2019sp 11
12 .Minimal acceptable state? Sensors need to be secured and trustworthy. We need to understand the context in which the sensor was deployed. And private data will need to be respected – which is not the case in the cloud as things stand! http://www.cs.cornell.edu/courses/cs5412/2019sp 12
13 .Microsoft’s Azure Intelligent Edge Exciting because for the first time, a really big company is viewing IoT as a serious business opportunity. Reminiscent of early PC days. Microsoft also has an unusually strong commitment to security and privacy. On the down side, they have a lot of challenges to overcome. But the smart devices are out there already, demand is increasingly real, and the winner could dominate a multi-trillion dollar market. http://www.cs.cornell.edu/courses/cs5412/2019sp 13
14 .Microsoft has a history of “big plays” They first emerged by betting big on PC’s and PC operating systems. Later, they were late to notice the Java trends, but caught up with C#/.NET Then, they were slow to wake up to the Internet, but ended up as a dominant cloud player, most recently with Office 365 for Business. http://www.cs.cornell.edu/courses/cs5412/2019sp 14
15 .Office 365: A glimpse of Azure I o T? Microsoft had a huge success with their Office 365 concept: Started by recognizing enormous popularity of their desktop software. Migration of this to the cloud made people productive anytime, anywhere (hence “365”), but also enables integration with social networking graphs and tools. “Do we have any experts on insurance products for salmon fishing fleets?” By acquiring LinkedIn, Microsoft, created a kind of “Facebook” for career-oriented tasks like tracking new automotive technologies, or fishery-management. It seems very likely that their approach to IoT will follow a similar plan. http://www.cs.cornell.edu/courses/cs5412/2019sp 15
16 .Azure I o T Today: Aiming for a Minimal but adequate launch point. The company’s first step has focused on IoT for corporate customers with huge numbers of smart devices, and little control over them. And within that first step, they focus on management of the “fleet” of sensor and actuator devices: Unmanaged sensors are a danger and a nightmare to the “owner” Seems like a necessary first step, in any case Can we “secure” the IoT devices, and make them “trustworthy”? http://www.cs.cornell.edu/courses/cs5412/2019sp 16
17 .Key architectural elements? Microsoft product: Azure IoT Hub, Iot Edge and Intelligent Edge First, the hub handles secure registration of devices and status tracking Next, it automates software upgrades It deals with issues of intermittent connectivity For devices that can be controlled from the cloud, it creates a “model” to enable you to perform those control actions http://www.cs.cornell.edu/courses/cs5412/2019sp 17
18 .Azure IoT: Database of sensors. The first step centers on secure registration of devices. The Azure IoT Hub manages a scalable database of sensors and associated data. The enterprise owner also records information such as: Device make and model, Software revision level, battery lifetime, when it was last serviced Where it is located, role it plays Additional application-specific information or “knowledge” http://www.cs.cornell.edu/courses/cs5412/2019sp 18
19 .This makes it an Active database! In a normal database the data tuples are just plain old data objects. In Azure IoT Hub, the objects in the database are intended to be “real” sensors and actuators. In effect, we now have meta-data describing the sensor combined with live properties (like battery level, photos cached, filter settings) that are wired to the actual device and change in real-time! http://www.cs.cornell.edu/courses/cs5412/2019sp 19
20 .Device security The level of security for today’s network-enabled IoT devices is poor to non-existent, making them way too easy to hack or disable. So Microsoft has a new product aimed at sensor manufacturers . The Azure Sphere is a special low-power security chip that embodies a hardware root of trust and low-power cryptographically protected HTTPS. With Azure Sphere, device manufactures can secure existing sensor products, and the resulting sensors will interoperate with Azure IoT hub. http://www.cs.cornell.edu/courses/cs5412/2019sp 20 Azure Sphere Development Kit
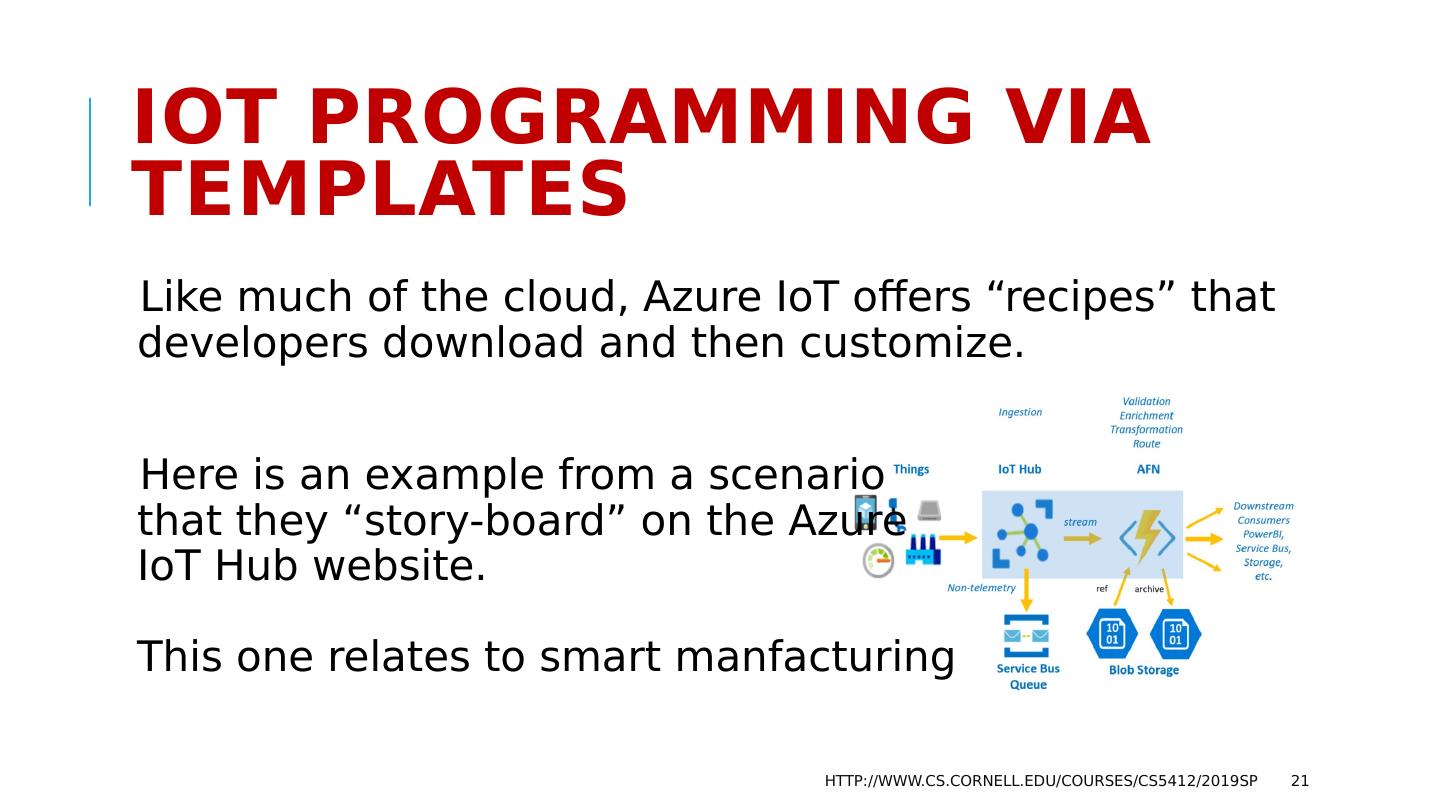
21 .IoT Programming via Templates Like much of the cloud, Azure IoT offers “recipes” that developers download and then customize. Here is an example from a scenario that they “story-board” on the Azure IoT Hub website. This one relates to smart manfacturing http://www.cs.cornell.edu/courses/cs5412/2019sp 21
22 .Every Azure IoT device has a “proxy” Many devices have limited network connectivity and won’t always be online. So in Azure IoT Hub, every device has a cloud-hosted “representative”: a software agent that can respond to device operations 24x7, and then will push updates (like new software revisions) when an opportunity arises. The agent can also schedule maintenance operations. http://www.cs.cornell.edu/courses/cs5412/2019sp 22
23 .Proxy programming In this Azure proxy mode, you can send information to a device even if the device is currently disconnected! The proxy is always available. For example, a firmware update or patch, or new device configuration. But obviously the action can’t occur until the device connects. So there is always a back-and-forth: Event “to” the device, and later, an event “back”. Applications will need to work in this very asynchronous way. http://www.cs.cornell.edu/courses/cs5412/2019sp 23
24 .Quality of Service issues For many devices, network quality is also an issue. Over time, a network link might be unavailable, or available but slow, or temporarily very fast (at a high price). In normal networks we don’t think about this much. But for IoT, our applications may need to be dynamically responsive as conditions change. http://www.cs.cornell.edu/courses/cs5412/2019sp 24
25 .The quality of the sensor itself is also a serious concern With large numbers of sensors we often get redundancy Wood and Marzullo explored this in a system called Meta here at Cornell. Key idea: first, that sensors have “range of accuracy”, and second that time also has a range of accuracy. Finally, that by leveraging this insight, we can actually identify and correct for many kinds of inaccuracy! http://www.cs.cornell.edu/courses/cs5412/2019sp 25
26 .Deep Dive: How does sensor accuracy impact the way we might use them? http://www.cs.cornell.edu/courses/cs5412/2019sp 26 Sensor A claims temperature was 70F at 10:01am Time Temp 70 75 65
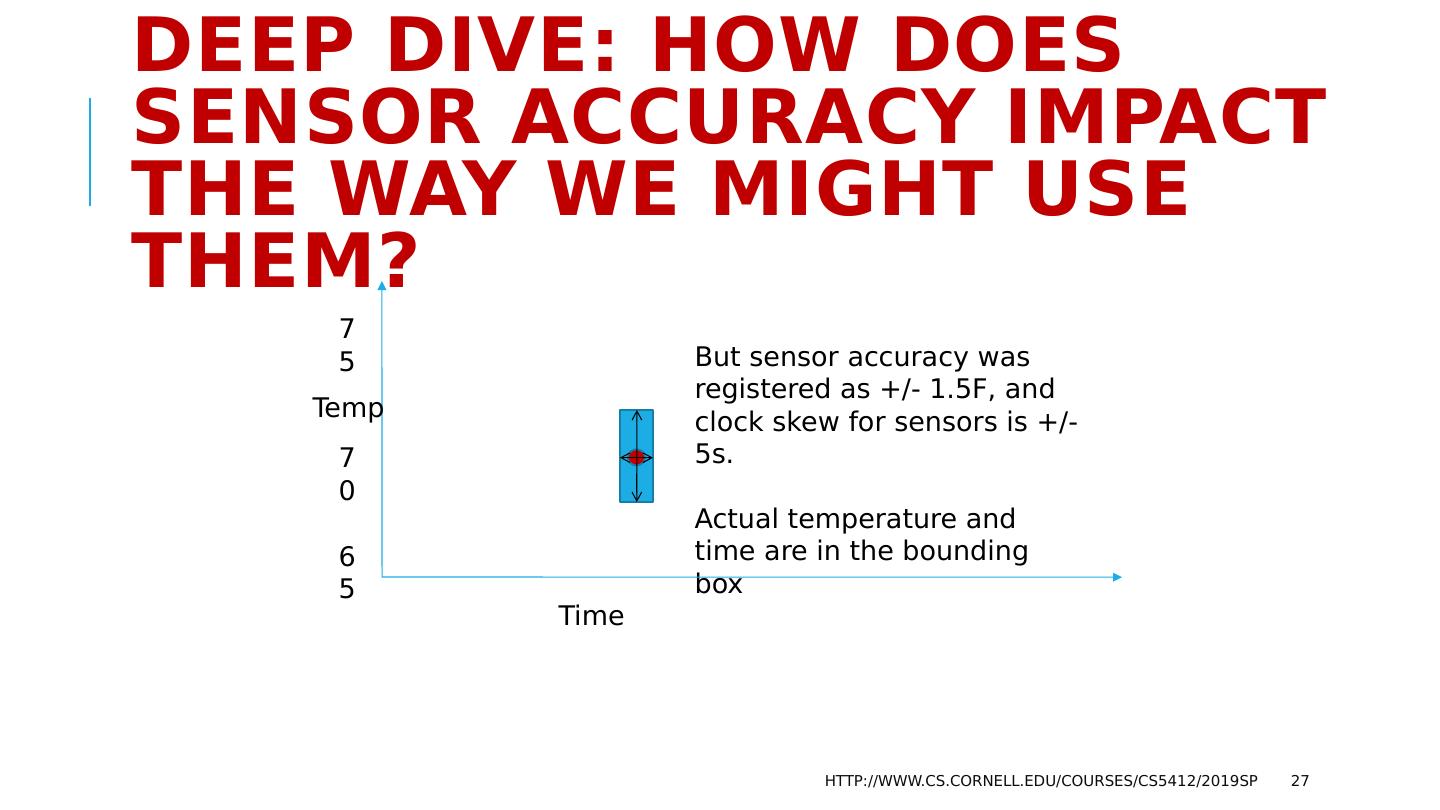
27 .Deep Dive: How does sensor accuracy impact the way we might use them? http://www.cs.cornell.edu/courses/cs5412/2019sp 27 But sensor accuracy was registered as +/- 1.5F, and clock skew for sensors is +/- 5s. Actual temperature and time are in the bounding box Time Temp 70 75 65
28 .Deep Dive: How does sensor accuracy impact the way we might use them? http://www.cs.cornell.edu/courses/cs5412/2019sp 28 Perhaps the room actually has three devices that measure temperature either directly, or in some indirect way: A, B and C. Time Temp 70 75 65
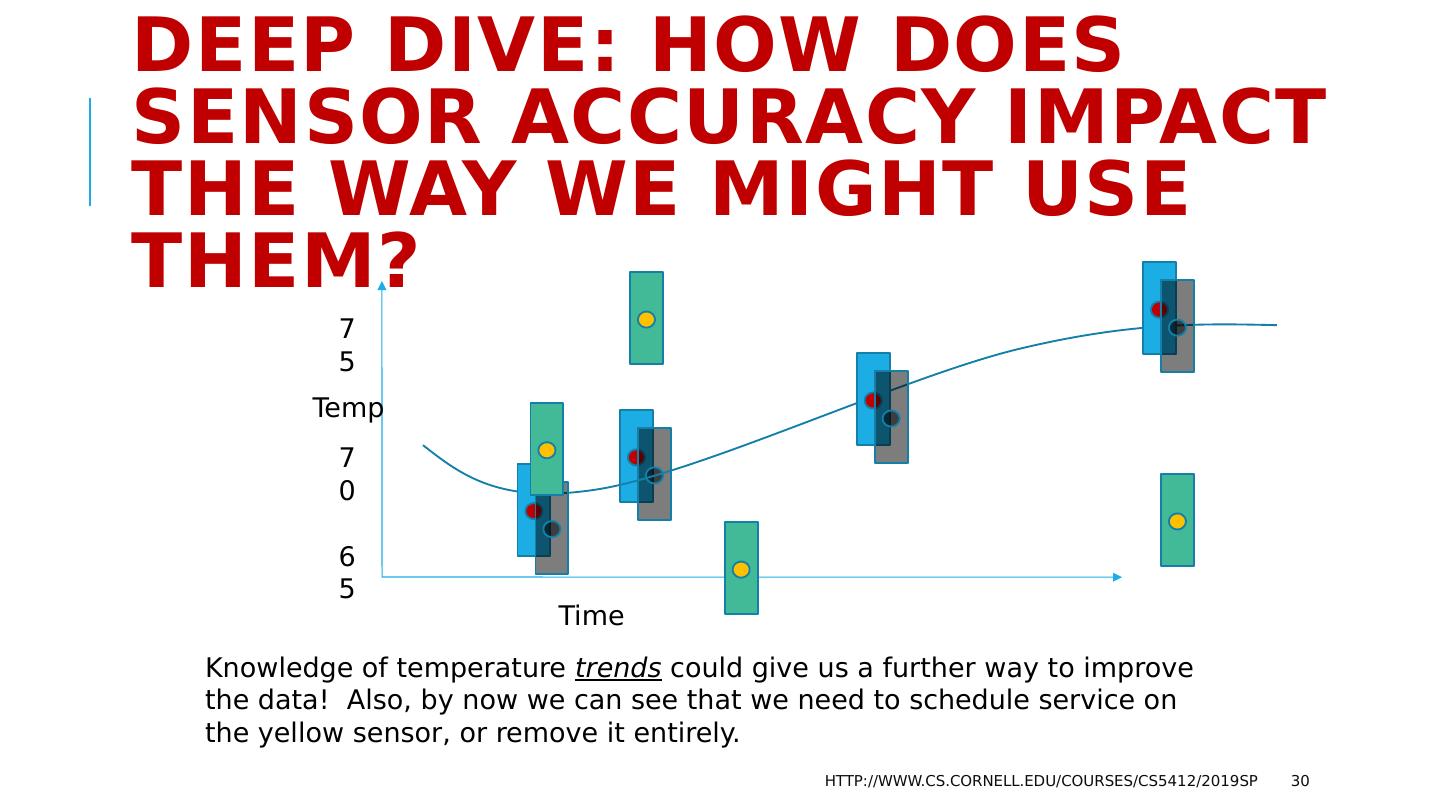
29 .Deep Dive: How does sensor accuracy impact the way we might use them? http://www.cs.cornell.edu/courses/cs5412/2019sp 29 Now we can recognize that one (the orange one) is faulty or miscalibrated . But the actual temperature must be in the overlap of the two correct ones, so we not only can figure this out, we can even improve the accuracy! Time Temp 70 75 65