- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- <iframe src="https://www.slidestalk.com/u3795/Protection_Security_Interface?embed" frame border="0" width="640" height="360" scrolling="no" allowfullscreen="true">复制
- 微信扫一扫分享
12-Protection/Security Interface
展开查看详情
1 .12. Protection/Security Interface 12.1 Security Threats Types of Damage Vulnerable Resources Types of Attacks 12.2 Functions of a Protection System 12.3 User Authentication Approaches to Authentication Passwords 12.4 Secure Communication Principles of Cryptography Secret-Key Cryptosystems Public-Key Cryptosystems Operating Systems 1
2 .Security Threats Types of damage Information Disclosure t heft Information Destruction possible without disclosure Unauthorized Use of services i nstall SW without license, pirated copies (theft) u se fake ID/password to use online service Denial of Service d ifficult to quantify Vulnerable resources Hardware (CPU, memory, communications, devices) Software (files, processes, VM) Operating Systems 2
3 .Types of Attacks Browsing of Information Unauthorized search for residual information Unused memory and disk space is generally not deleted Typically done by a user who is already inside Information leaking A trusted service leaks confidential/secret information (Confinement Problem) Operating Systems 3
4 .Types of Attacks Trojan Horse Greek mythology—the siege of Troy wooden horse = “present” by Greeks soldiers hidden inside Trojans pulled the horse into the city soldiers opened the gates for the Greeks, causing the destruction of Troy Attack: trusting user accepts a “ present ”, e.g. a free program, that causes damage (don’t open email attachments) Trap door a n undocumented feature i nserted on purpose or as a flaw to enter later Operating Systems 4
5 .Types of Attacks Viruses Designed to replicate themselves r emovable storage media, email, file transfer Intended to cause damage Need a host program a ttach to and modify host e xecute as part of host Virus detection c heck program length (but virus can hide or compress program) c heck for virus “signature”—bit pattern used by virus to mark already infected program (viruses use encryption) Operating Systems 5
6 .Types of Attacks Worms Intended to cause damage Exploit some system weakness to replicate No host needed Example: Robert Morris Internet Worm (Nov 2, 1988) Excessive replication caused major havoc on the internet (denial of service) 3 separate attacks : rsh : Spawn process on remote machine without pw (using a list of “trusted” systems) sendmail : Exploited an error that allows a message to send itself and start finger: Buffer overflow not checked – major weakness to take over the system Operating Systems 6
7 .Types of Attacks Buffer Overflow: Example : foo calls finger Attack hijacks return address by supplying a parameter that is longer than the buffer ( overflows) When finger terminates, control goes to a place set by the attack and is not returned to foo . Operating Systems 7
8 .Types of Attacks Remote execution Service to upload and start code on remote machine Mobile agent : may migrate among machines Like worm but legitimate migration Must be designed carefully to prevent abuse of privileges of remote host environment Wire tapping Insert a device into line or listen to wireless Passive (listen) or Active (modify) Waste searching Look for passwords or sensitive data Operating Systems 8
9 .Types of Attacks Masquerading Impersonate process, user, service Used from outside : Use stolen password (impersonate a legitimate user) Break communication line, assume session Used from within ( spoofing ) : Impersonate login shell, steal password Trial and error e.g., try to guess password Operating Systems 9
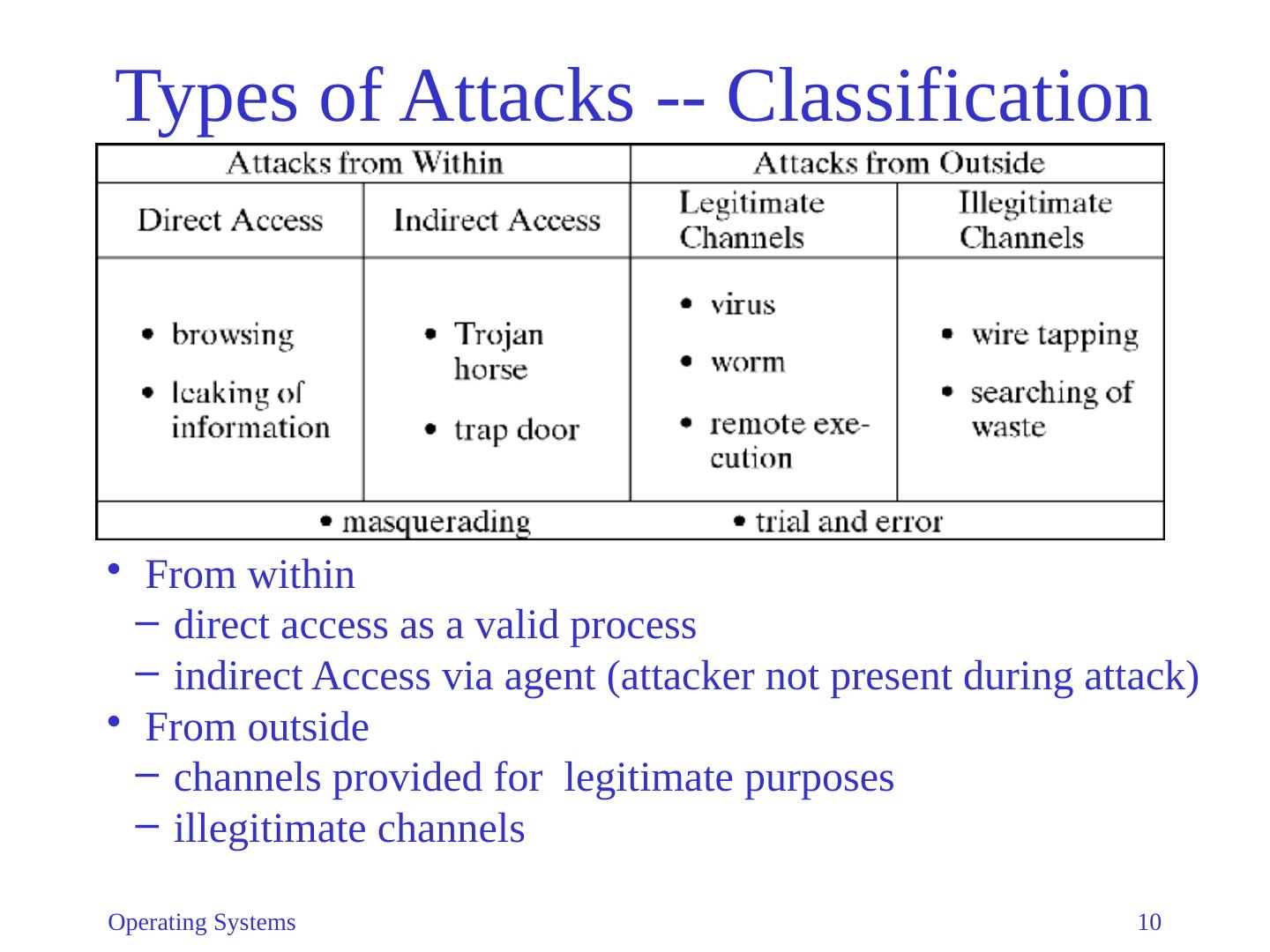
10 .Types of Attacks -- Classification From within d irect access as a valid process i ndirect Access via agent (attacker not present during attack) From outside c hannels provided for legitimate purposes i llegitimate channels Operating Systems 10
11 .Functions of a Protection System External safeguards g uard physical access (locks, badges, cameras) Verification of user identity (User Authentication) Communication safeguards p rotect public/vulnerable lines : cryptography Access control ( Ch 13) c an S ubject perform f unction on R esource Information flow control ( Ch 13) c an S get information contained in R (indirectly) Operating Systems 11
12 .User Authentication Approaches: Knowledge of some information Password, dialog Possession of some artifact Machine-readable cards (ATM) Combine with knowledge (PIN) Biometrics : Physical characteristics of person Fingerprint Hand geometry Face geometry Retina or iris scan Voice print Signature dynamics Operating Systems 12
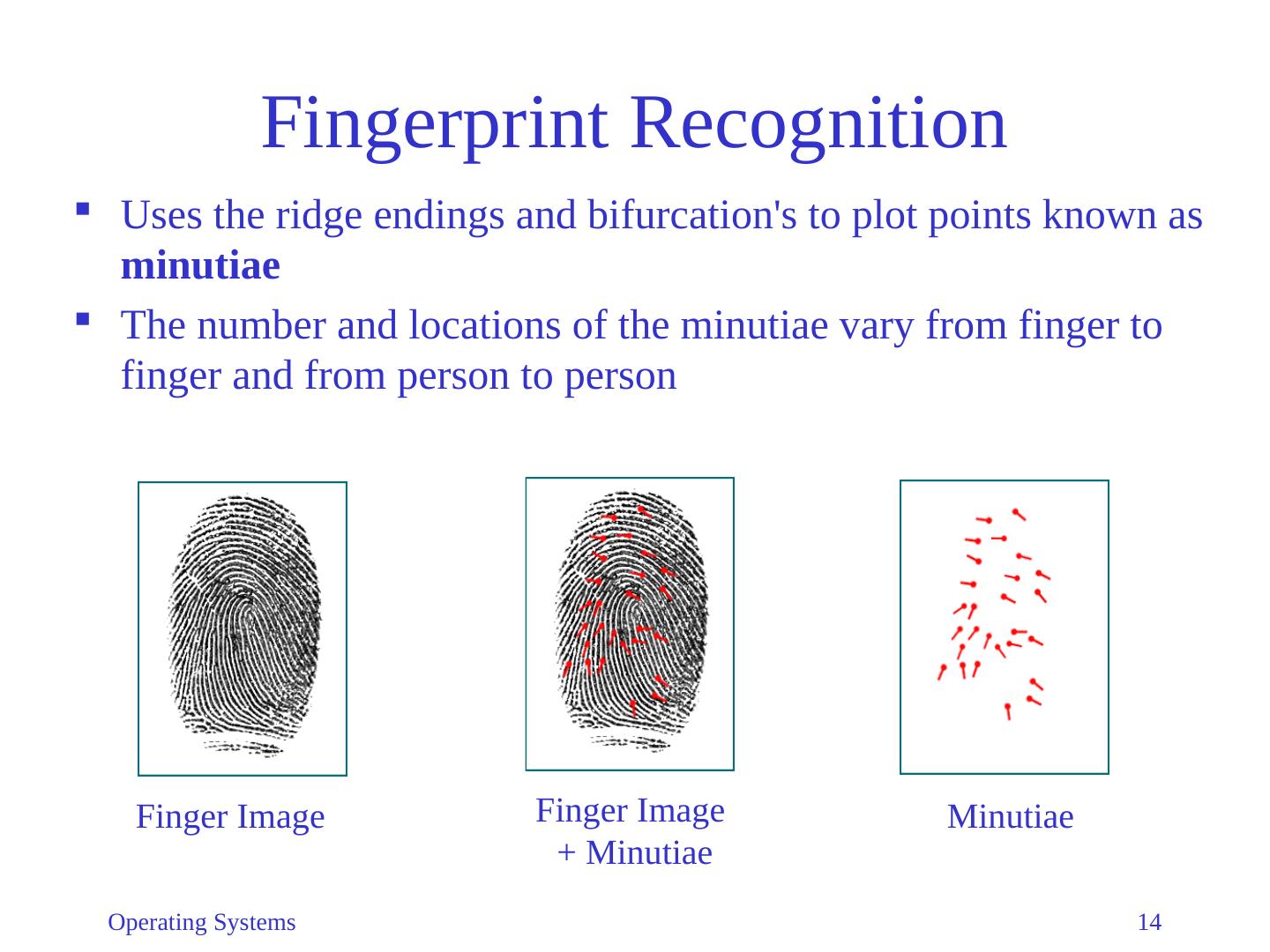
13 .Fingerprint Recognition Extremely useful biometrics technology Fingerprints are a primary and accurate identification method Operating Systems 13
14 .Fingerprint Recognition Extremely useful biometrics technology Fingerprints are a primary and accurate identification method Operating Systems 13
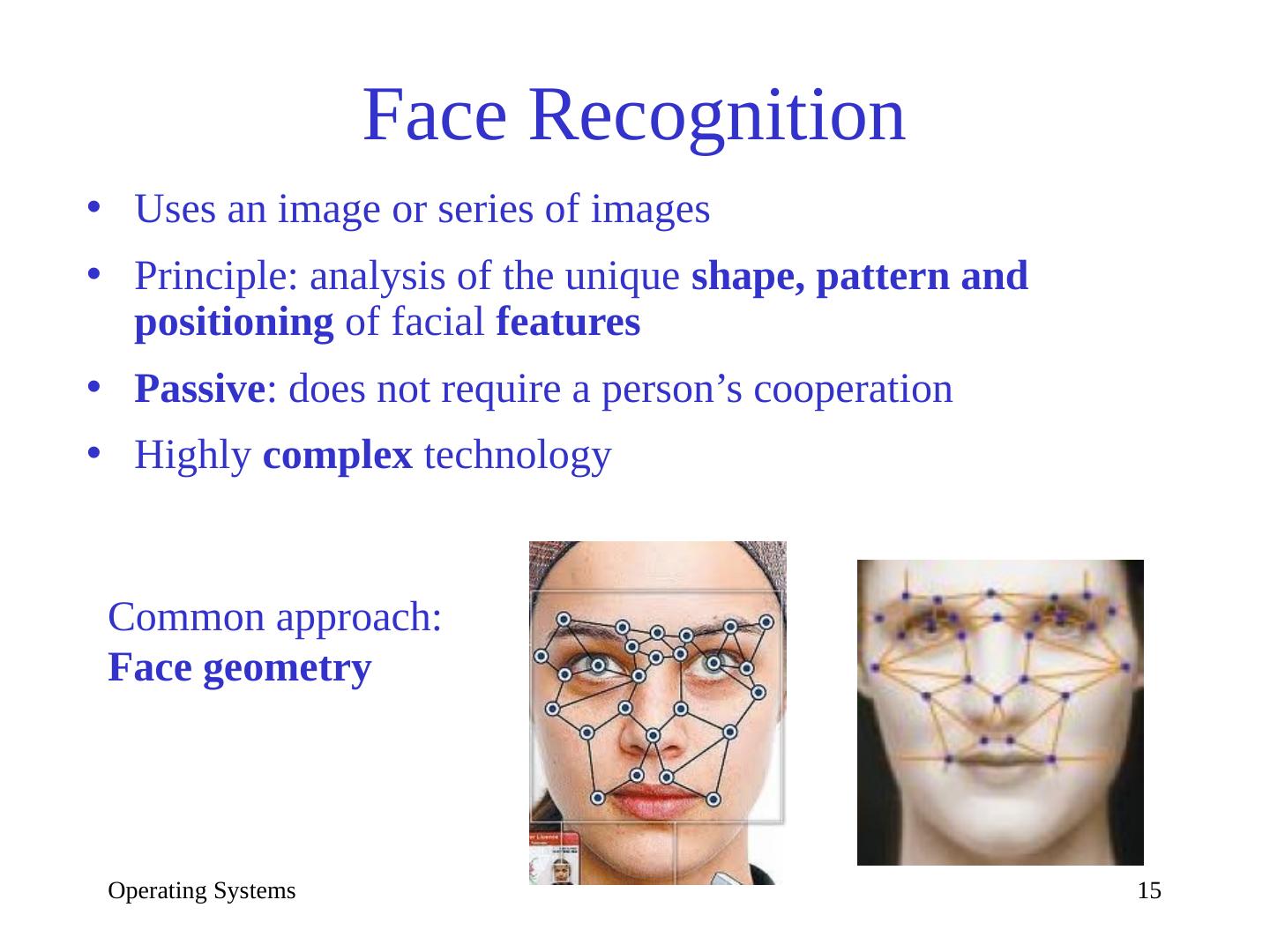
15 .Face Recognition Uses an image or series of images Principle: analysis of the unique shape, pattern and positioning of facial features Passive : does not require a person’s cooperation Highly complex technology Common approach: Face geometry Operating Systems 15
16 .Voice Recognition N ot speech recognition, it is speaker recognition Low-cost (cheap hardware) Not very accurate (voice varies, noise) Can be stolen (recorded) Operating Systems 16
17 .Hand geometry one of the most deployed biometrics world wide Ben Gurion Airport (Israel) Operating Systems 17
18 .Signature Verification Static/off-line: match pattern (image) can easily be reproduced Dynamic/On-line: match movement of the pen during signing process (pressure, speed) Many commercial products Operating Systems 18
19 .Iris recognition Based on visible features , i.e. rings, furrows, freckles and the corona Safest, most accurate biometrics technology Heathrow Airport (London ) Operating Systems 19
20 .Retina recognition Capture the pattern of blood vessels throughout the retina No two retinas are the same, even in identical twins More difficult/less convenient than iris scan Operating Systems 20
21 .Thermograms infrared camera to detect the heat patterns Other techniques DNA Unique (except for identical twins) but many imitations : n ot fully automated, slow, expensive p rivacy issue – DNA contains information about race , paternity, medical conditions r equires a physical sample of tissue Operating Systems 21
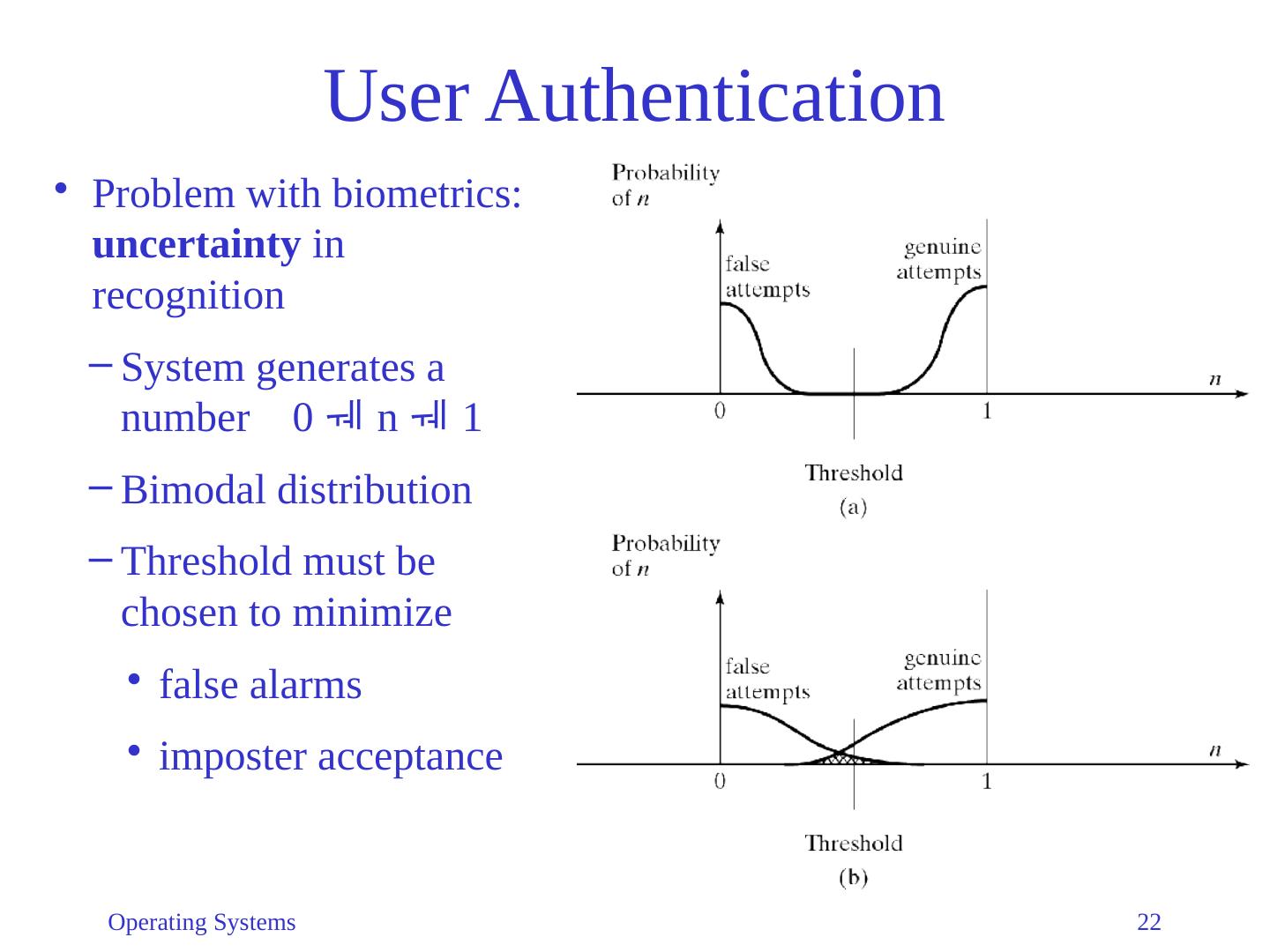
22 .User Authentication Problem with biometrics: uncertainty in recognition System generates a number 0 n 1 Bimodal distribution Threshold must be chosen to minimize f alse alarms imposter acceptance Operating Systems 22
23 .User Authentication Passwords Must protect stored password files from access Must prevent trial and error ( guessing ) Protecting password files Maintain unencrypted; rely on access control Encrypt using “one-way” function H: H -1 is unknown knowing H(x) does not yield x k eep only H(pw) with user name a t login, compute H(pw’) and compare with H(pw) Operating Systems 23
24 .User Authentication Preventing password guessing System-generated pw Random string: difficult to memorize “ Pronounceable ” words System-validated Accept only passwords that obey specifications (length, mix of letters/digits, upper/lower case) Employ password-cracking programs to reject easy-to-guess passwords Time-limited Expiration date or number of uses Operating Systems 24
25 .User Authentication O ne-time passwords Smart card (can be lost or stolen) Use secret function ; System generates a challenge n, user replies with f(n) as password; e.g. f(n) =3* n /2 Use one-way function to generate series of one-time passwords from one password pw … H(H(H(pw))) H(H(pw)) H(pw) pw Intruder can derive H(H(pw)) from H(pw) but not H(pw) from H(H(pw)) because H -1 is unknown Operating Systems 25
26 .User Authentication guess any valid password: repeatedly generate strings s (dictionary, random, …), check if H(s) is in table System-extended pw f or each pw , generate random number slt (called “salt”) s tore : UserName, slt , H ( slt,pw ) g uessing: must check H( slt,s ) for every slt in table s alting does not make it harder to guess the password of a specific user Operating Systems 26
27 .Functions of a Protection System External safeguards Guard physical access (locks, badges, cameras) Verification of user identity (User Authentication) Communication safeguards Protect public/vulnerable lines: cryptography Access control Can S ubject perform f unction on R esource Information flow control Can S get information contained in R (indirectly) Operating Systems 27
28 .Secure Communication Principles of cryptography: C ipher text, P lain text, K ey(s) E ncrypt: C = E( P,K e ) D ecrypt: D( C,K d ) = P Goals: Secrecy = message content not revealed Integrity = message not modified Authenticity = establish identity of sender Nonrepudiability = establish identity of creator (regardless of who sent it) an actor cannot deny creation of message (signature) Operating Systems 28
29 .Secure Communication Secret-key Cryptosystems Symmetric : S and R s hare a common secret key K which is used for both encrypting and decrypting Operating Systems 29