- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- <iframe src="https://www.slidestalk.com/u9099/MongoDB_Security_Checklist?embed" frame border="0" width="640" height="360" scrolling="no" allowfullscreen="true">复制
- 微信扫一扫分享
MongoDB Security Checklist
MongoDB部署是否安全?本文将介绍MongoDB部署的安全最佳实践。讨论内容包括授权、客户机/服务器SSL、SELinux等功能。
展开查看详情
1 .MongoDB Security Checklist Tim Vaillancourt Sr Technical Operations Architect, Percona Speaker Name
2 .`whoami` { name: “tim”, lastname: “vaillancourt”, employer: “percona”, techs: [ “mongodb”, “mysql”, “cassandra”, “redis”, “rabbitmq”, “solr”, “mesos” “kafka”, “couch*”, “python”, “golang” ] }
3 .Agenda ● Authorization ● External Authentication ● SSL / TLS Encryption ● Filesystem Security ● SELinux ● Network Security
4 .Security ● Security is becoming more pressing almost every day ● Example: 2017 MongoDB Ransom Attacks ○ Publicly accessible hosts compromised remotely ○ Database data uploaded off of the network
5 .Security ● MongoDB Ransom Attacks ○ Database data was then deleted ○ A MongoDB document is left behind as a ransom note, demanding $$$ ○ Your security approach had to be very weak
6 .Security
7 .Authorization: Role-based Security ● Always enable auth on Production Installs! ○ Default enabled on 3.5 / 3.6+! ● Built-in Roles ○ Database User: Read or Write data from collections ■ “All Databases” or Single-database ○ Database Admin ○ Backup and Restore ○ Cluster Admin ○ Superuser/Root
8 .Authorization: Role-based Security ● User-Defined Roles ○ Exact Resource+Action specification ○ Very fine-grained ACLs ■ Action + DB + Collection specific ● Helper script for PSMDB(!): percona-server-mongodb-enable-auth.sh
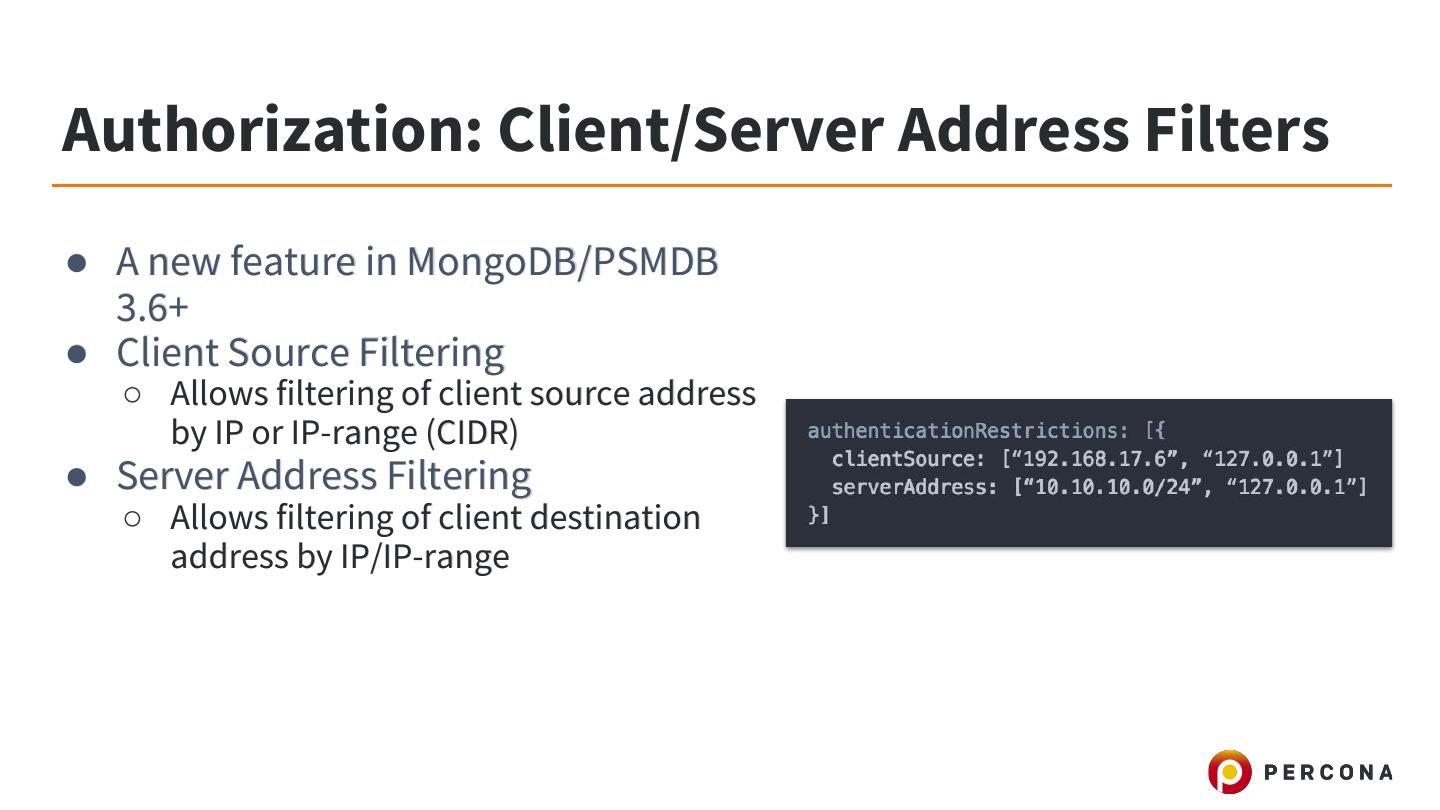
9 .Authorization: Client/Server Address Filters ● A new feature in MongoDB/PSMDB 3.6+ ● Client Source Filtering ○ Allows filtering of client source address by IP or IP-range (CIDR) ● Server Address Filtering ○ Allows filtering of client destination address by IP/IP-range
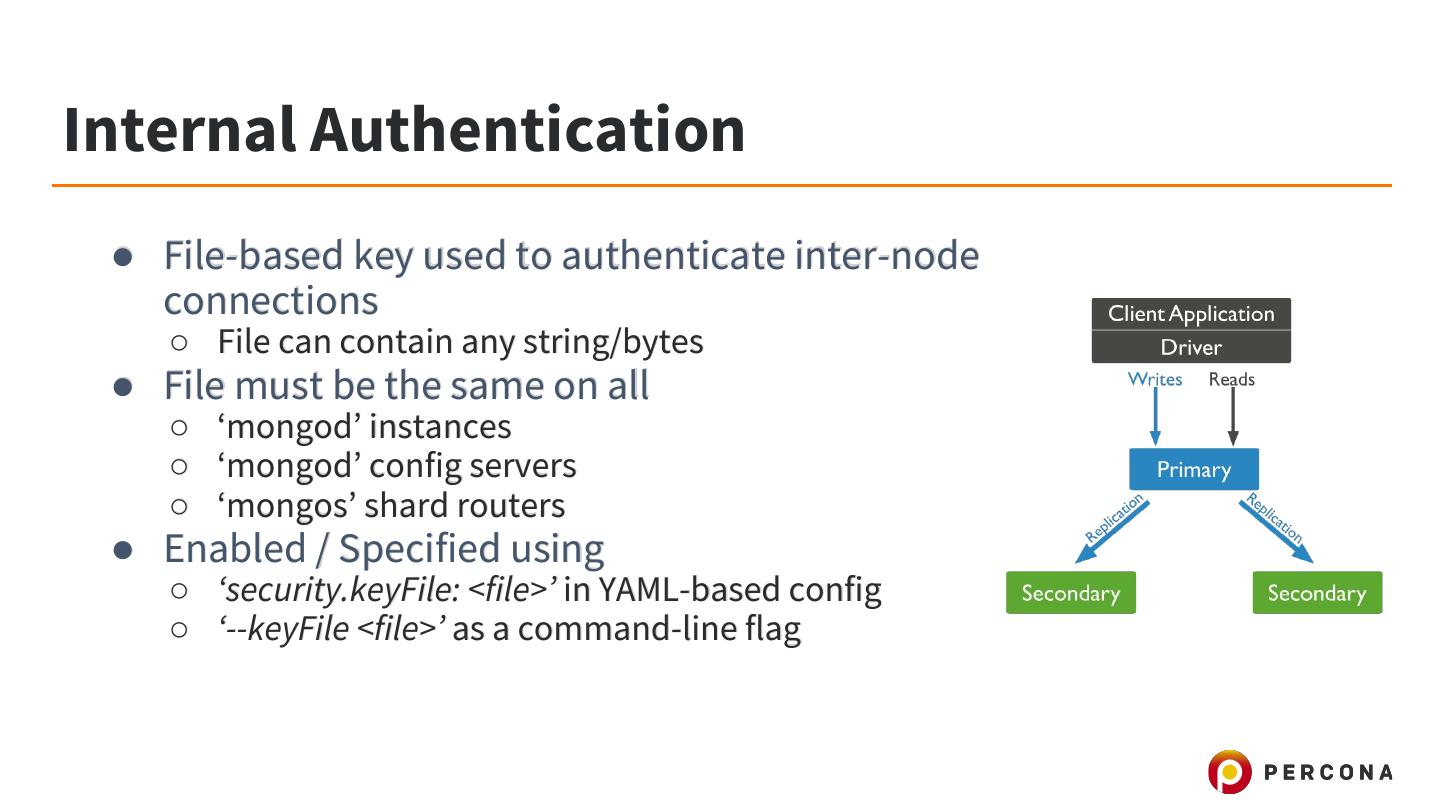
10 .Internal Authentication ● File-based key used to authenticate inter-node connections ○ File can contain any string/bytes ● File must be the same on all ○ ‘mongod’ instances ○ ‘mongod’ config servers ○ ‘mongos’ shard routers ● Enabled / Specified using ○ ‘security.keyFile: <file>’ in YAML-based config ○ ‘--keyFile <file>’ as a command-line flag
11 .LDAP ● LDAP Authentication ○ Supported in PSMDB and MongoDB Enterprise ■ PSDMB implementation != MongoDB Enterprise implementation ○ The following components are necessary for external authentication to work ■ LDAP Server ■ SASL Daemon ■ SASL Library ○ More on this here: https://www.percona.com/blog/2017/11/06/mongodb-security-using-ldap-authentication/
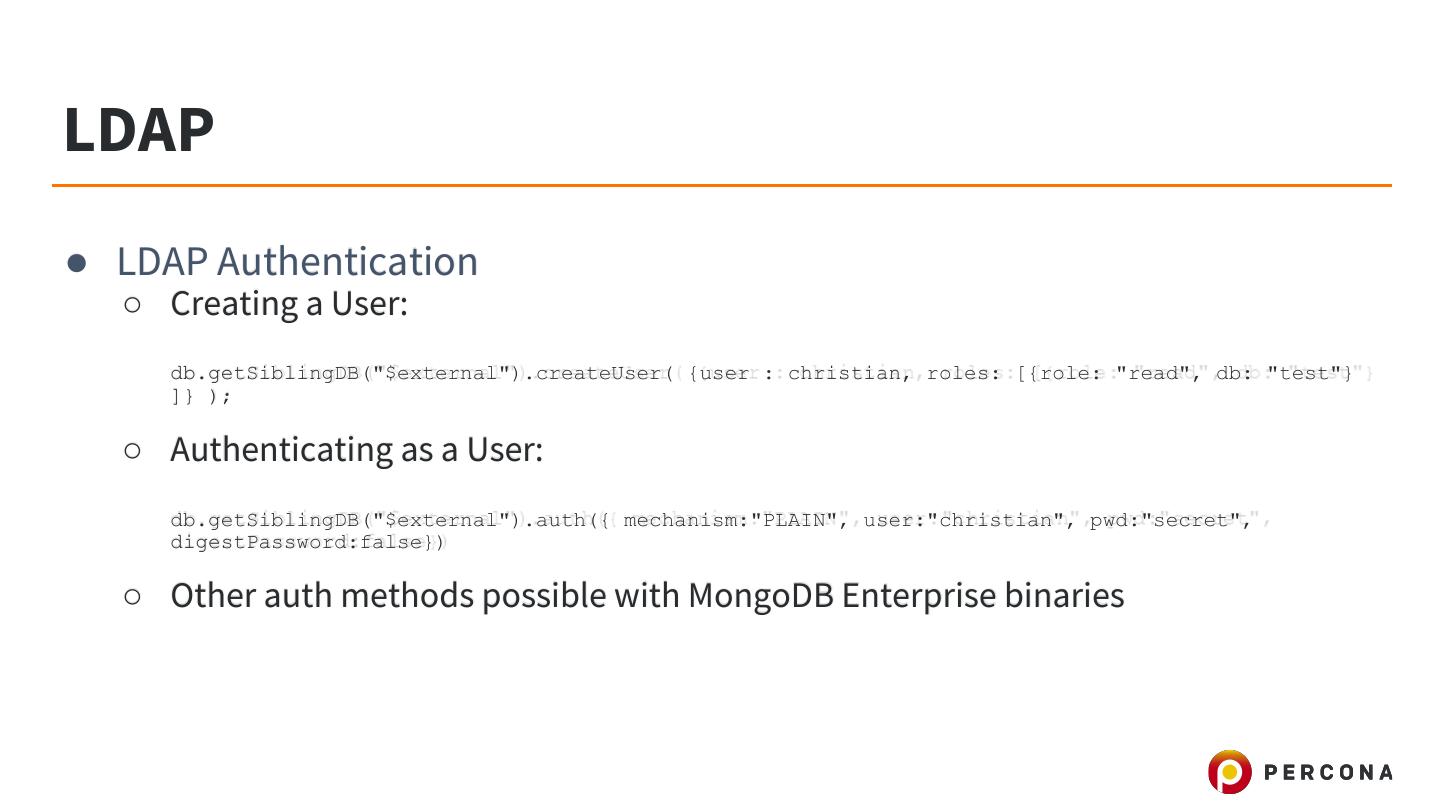
12 .LDAP ● LDAP Authentication ○ Creating a User: db.getSiblingDB("$external").createUser( {user : christian, roles: [{role: "read", db: "test"} ]} ); ○ Authenticating as a User: db.getSiblingDB("$external").auth({ mechanism:"PLAIN", user:"christian", pwd:"secret", digestPassword:false}) ○ Other auth methods possible with MongoDB Enterprise binaries
13 .SSL / TLS Connections ● SSL / TLS Connections ○ Supported since MongoDB 2.6x ■ May need to compile-in yourself on older binaries ■ Supported 100% in Percona Server for MongoDB ○ Minimum of 128-bit key length for security ○ Relaxed and strict (requireSSL) modes ○ System (default) or Custom Certificate Authorities are accepted
14 .SSL / TLS Connections ● SSL Client Authentication (x509) ○ MongoDB supports x.509 certificate authentication for use with a secure TLS/SSL connection as of 2.6.x. ○ The x.509 client authentication allows clients to authenticate to servers with certificates rather than with a username and password. ○ Enabled with ‘security.clusterAuthMode: x509’ in config file
15 .Filesystem Attack-Surface ● Use a service user+group (‘mongod’ or ‘mongodb’ on most systems) ○ Ensure data path, log file and key file(s) are owned by this user+group ● Data Path ○ Mode: 0750
16 .Filesystem Attack-Surface ● Log File ○ Mode: 0640 ○ Contains real queries and their fields!!! ■ See Log Redaction for PSMDB (or MongoDB Enterprise) to remove these fields ● Key File(s) ○ Files Include: keyFile and SSL certificates or keys ○ Mode: 0600
17 .Encryption at Rest ● MongoDB Enterprise ○ Encryption supported in Enterprise binaries ($$$) ● Percona Server for MongoDB ○ Use CryptFS/LUKS block device for encryption of data volume ○ Documentation published (or coming soon) ○ Completely open-source / Free
18 .Encryption at Rest ● Application-Level ○ Selectively encrypt only required fields in application ○ Benefits ■ The data is only readable by the application (reduced touch points) ■ The resource cost of encryption is lower when it’s applied selectively ■ Offloading of encryption overhead from database
19 .System Access ● Recommended to restrict system access to Database Administrators ● A “shell” on a system can be enough to take the system over! ● Why is this risky? ○ Shells can execute local attacks on software vulnerabilities ○ Access to root or filesystem paths is not necessarily required
20 .System Access ● Packages to Remove / Uninstall ○ GCC (GNU C Compiler) ■ This is often used to build local attacks ○ Generic scripting languages (wherever possible) ■ Python ■ Perl ■ Ruby ■ Golang
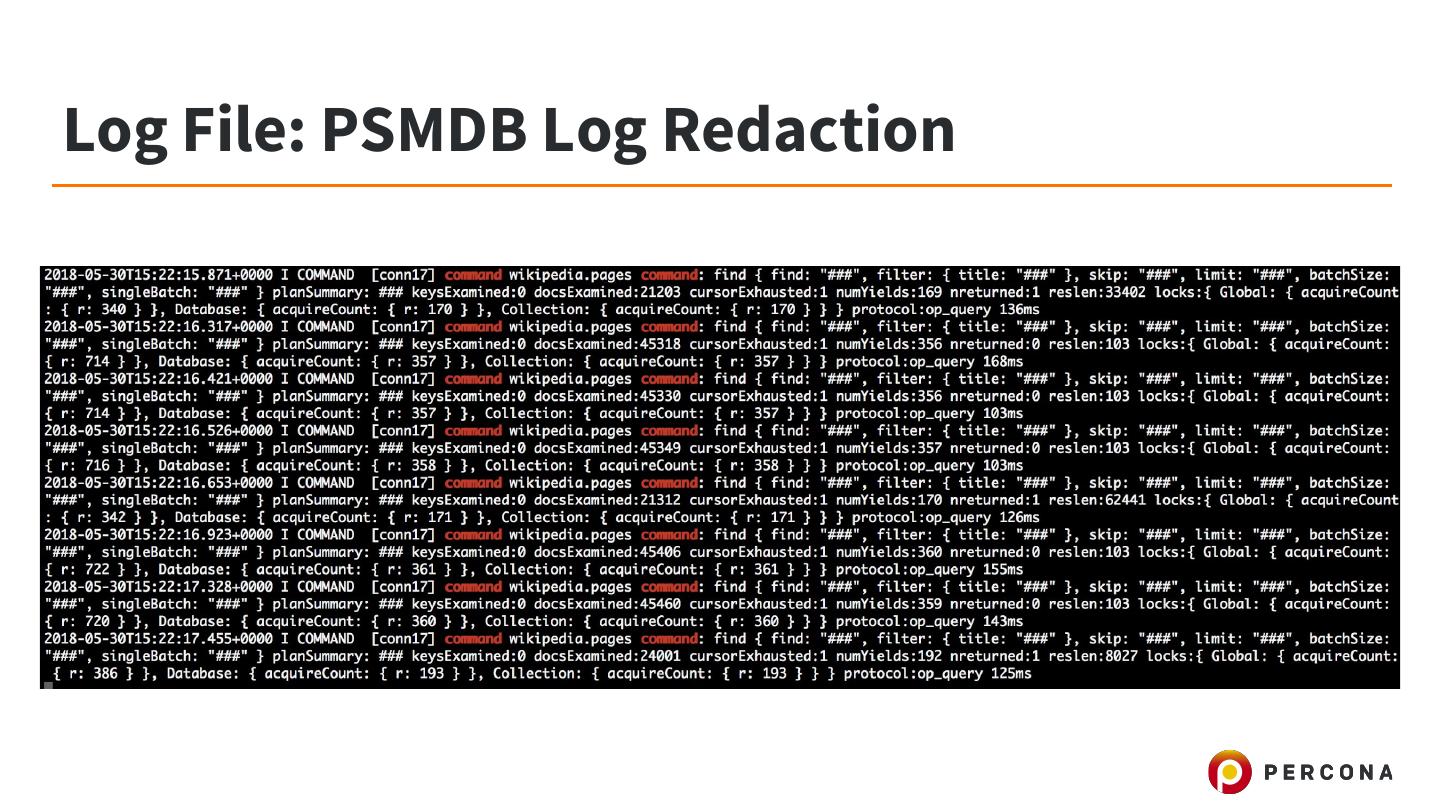
21 .Log File: PSMDB Log Redaction ● Percona Server for MongoDB feature ○ Also available in MongoDB Enterprise binaries ● Allows the redaction of values in logging of server queries, commands, etc ● Useful for PCI compliance, etc ● Beware: debug log-level will still expose user data!
22 .Log File: PSMDB Log Redaction
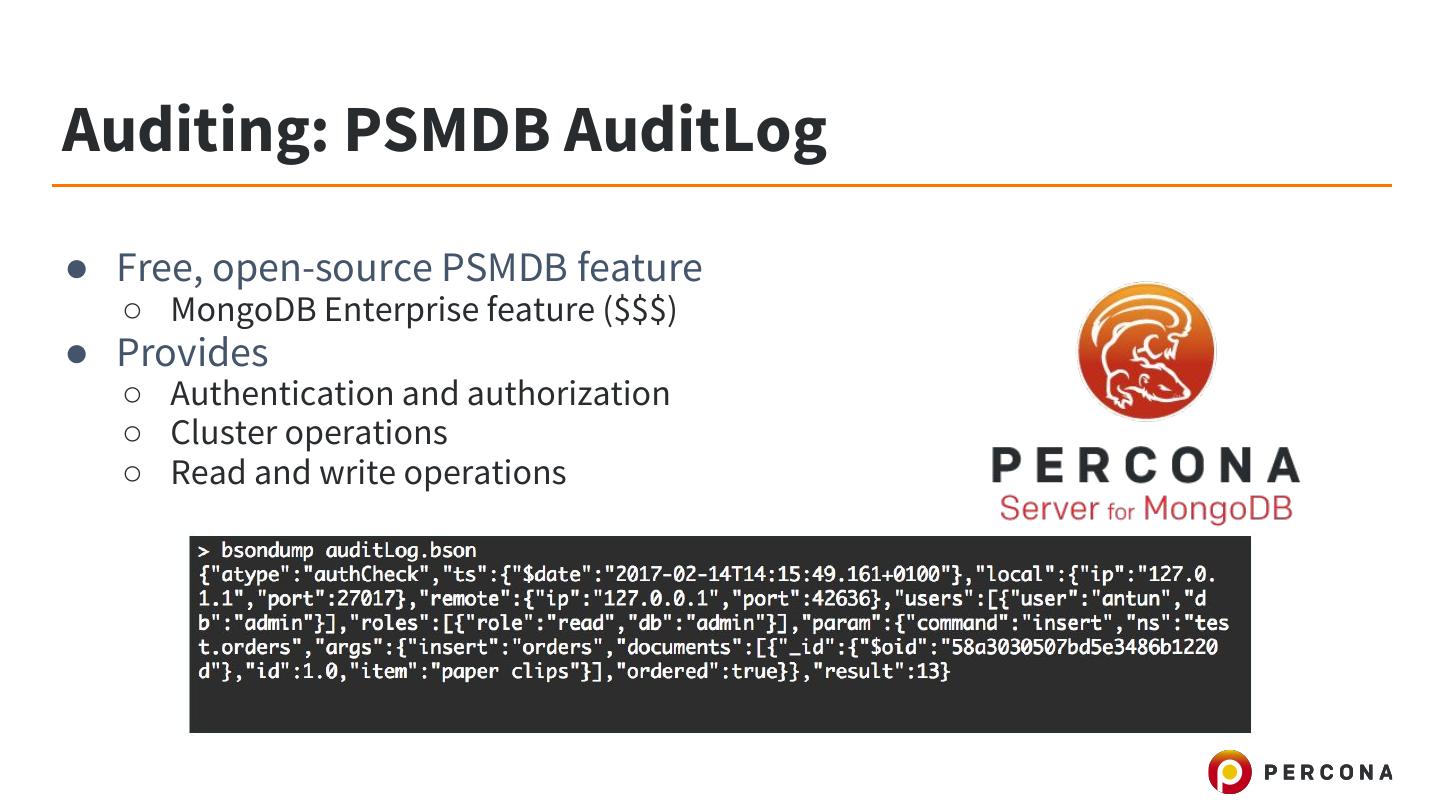
23 .Auditing: PSMDB AuditLog ● Free, open-source PSMDB feature ○ MongoDB Enterprise feature ($$$) ● Provides ○ Authentication and authorization ○ Cluster operations ○ Read and write operations
24 .Auditing: PSMDB AuditLog ● Provides ○ Schema operations ○ Custom application messages (if configured) ● Writes to BSON files on disk ○ Read data with ‘bsondump --pretty’ ○ Ensure directory NOT world-readable!
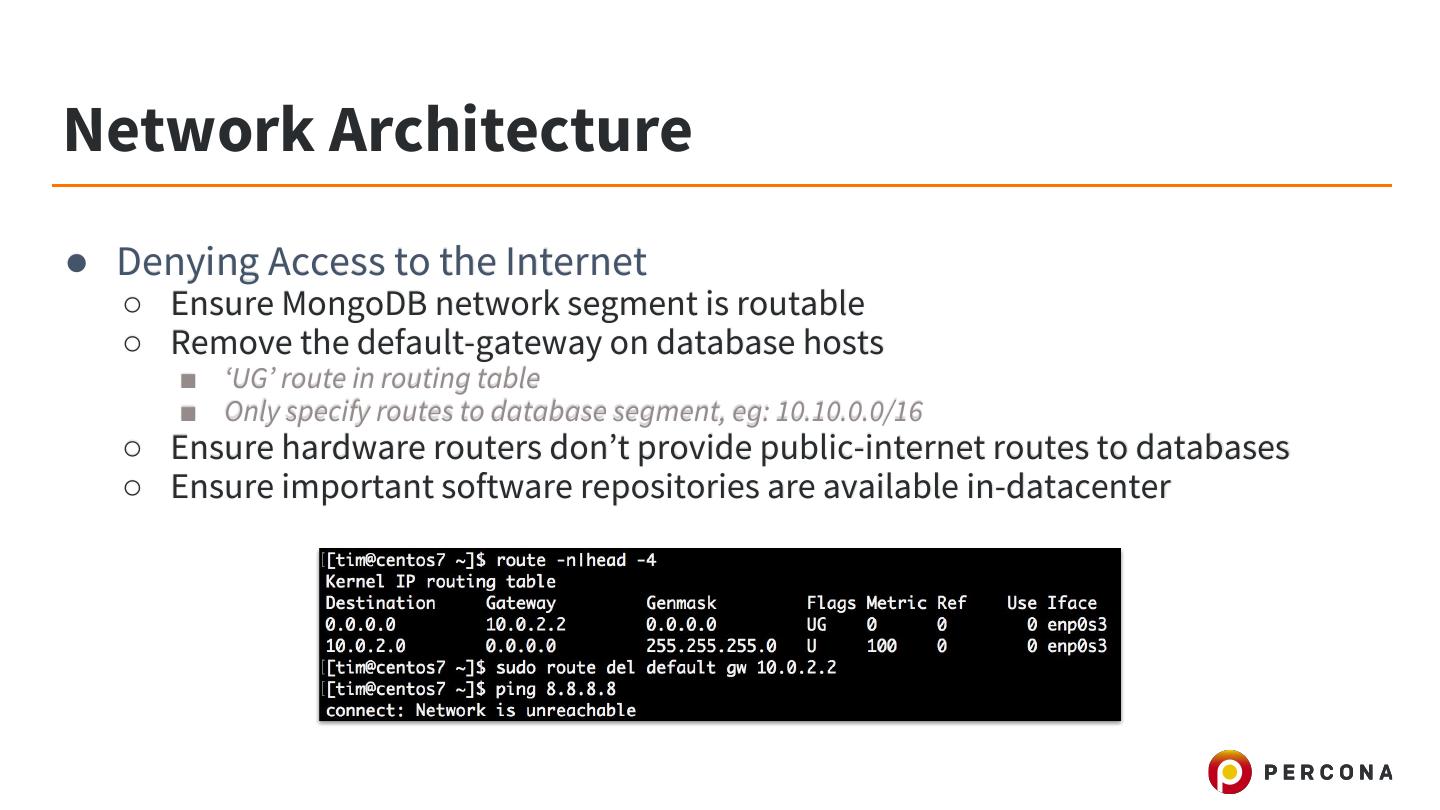
25 .MongoDB Bind Address ● A configuration variable controlling the listen address of MongoDB ○ ‘net.bindIp’ YAML-config field ○ --bindIp mongod command-line flag ● Defaults ○ Before 3.5/3.6 MongoDB will listen on all interfaces by default ○ 3.5+ default bindIp is ‘localhost’ ○ Risks ■ Addition of interfaces can add attack surface (VMs, etc)
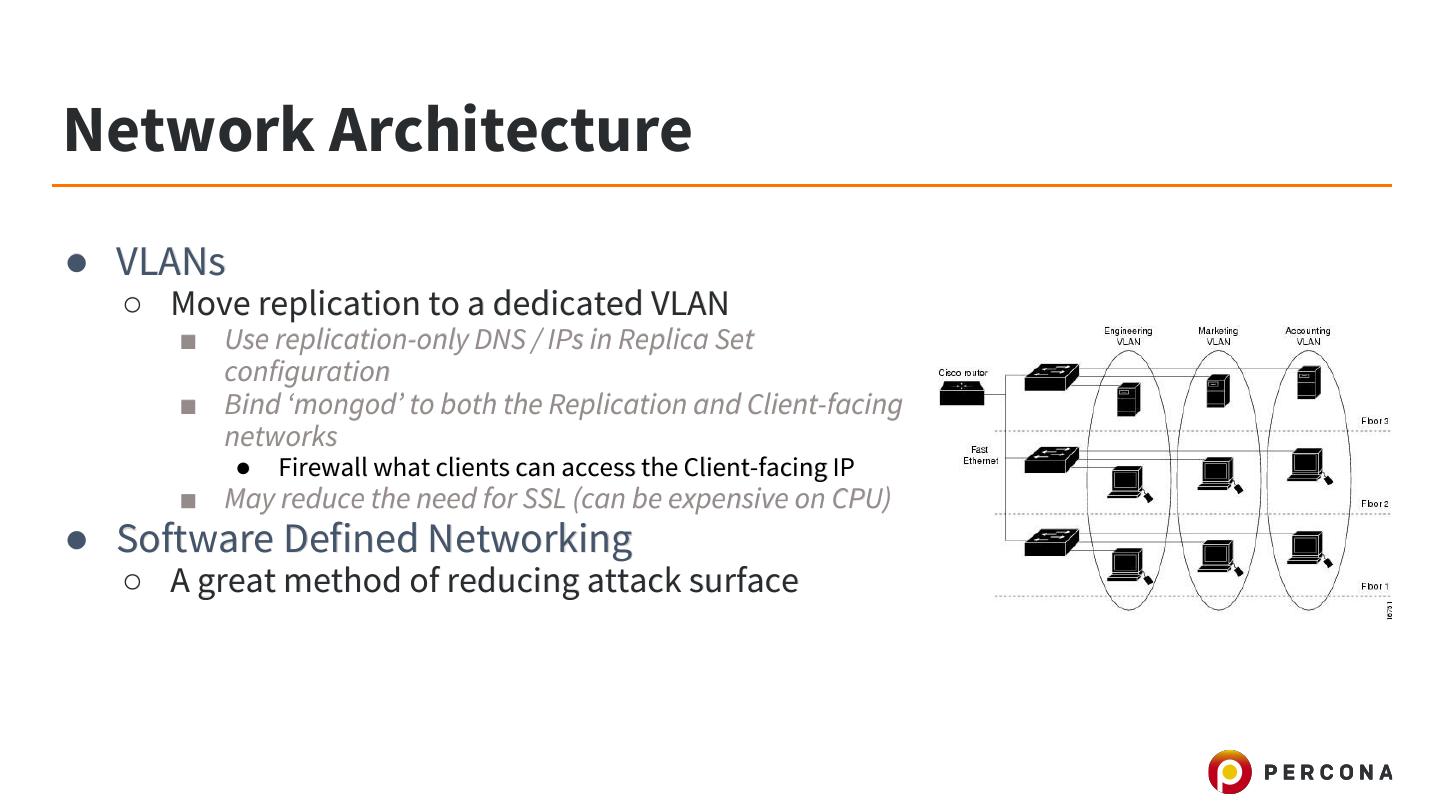
26 .Firewalls ● Firewall Solutions ○ Software (IPTables) ■ Drawback: software, can be compromised! ○ Hardware (Routers/etc) ● Single TCP port ○ MongoDB Client API ○ MongoDB Replication API ○ MongoDB Sharding API
27 .Firewalls ● Sharding Considerations ○ Only the ‘mongos’ process needs access to shard ‘mongod’ servers ○ Client driver does not need to reach shards directly, only ‘mongos’ ● Replica Set Considerations ○ All nodes must be accessible to the driver ● Secure NTP Daemon ○ Mitigate NTP reflection attacks ○ Restrict access to NTP
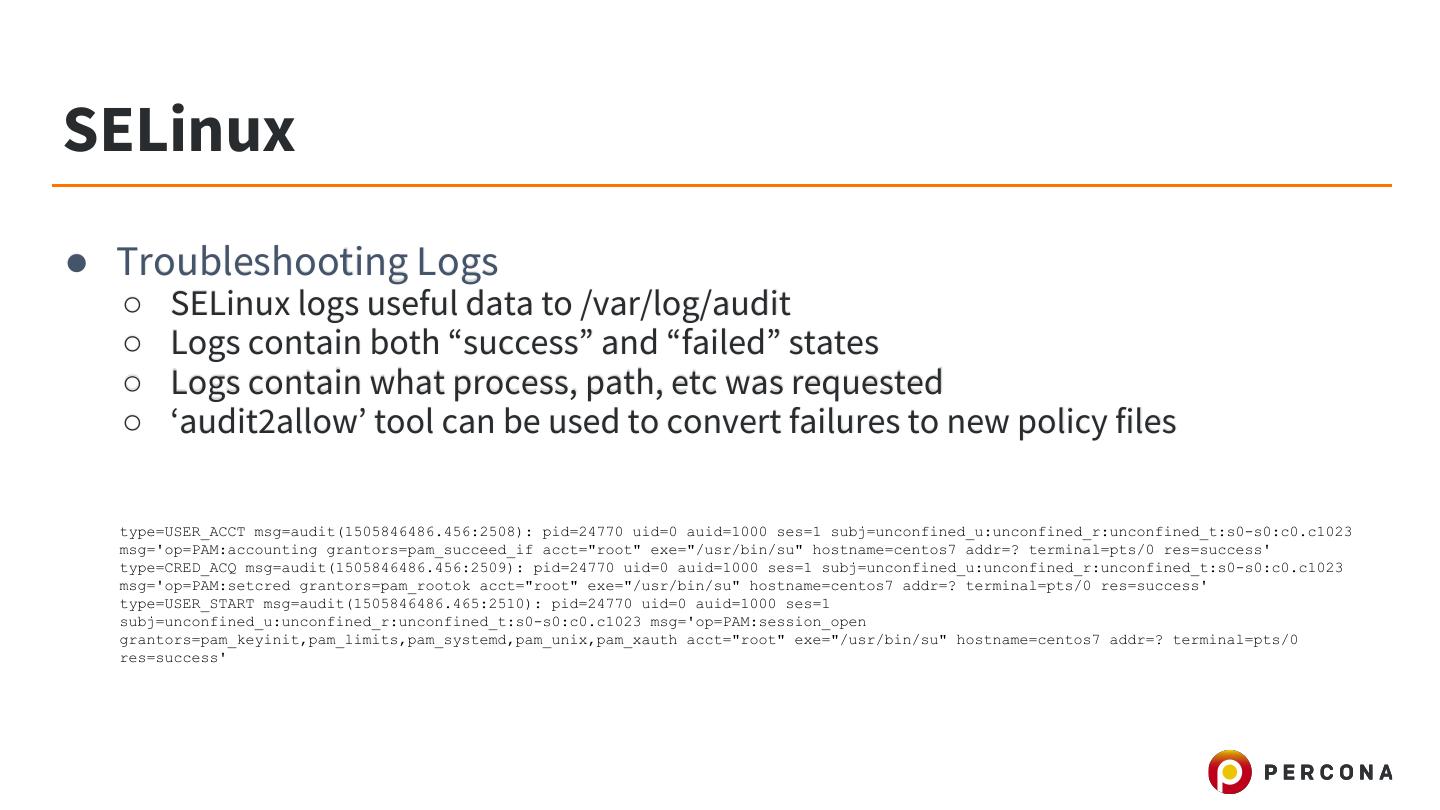
28 .SELinux ● That thing every Stackoverflow / Forum tells you to just disable ● Very effective at reducing attack surface on host ● ACL-based “policies” control what is allowed on a system ● Modes ○ Enforcing: Don’t allow policy violations ○ Permissive: Allow policy violations and log them ○ Disabled: You really don’t like security
29 .SELinux ● Relatively simple to deploy on Linux Database servers ○ Database hosts are usually single-purpose ○ Databases need very little filesystem access (only data dir, log dir and config files) ● Percona Server for MongoDB support ○ Built-in CentOS / RHEL 7+ RPMs support (others are planned) ○ Works 100% with ‘Enforcing’ Mode SELinux ■ Default Mode on CentOS 7.x